Building the Real Human Network
Disclaimer
This white paper has not been approved by any competent authority in any Member State of the European Union. The person seeking admission to trading is solely responsible for the content of this white paper.
This white paper complies with Title II of Regulation (EU) 2023/1114 and, to the best of the knowledge of the management body, the information presented in the white paper is fair, clear and not misleading and the white paper makes no omission likely to affect its import.
Introducing World Network
World Network was founded with the mission of creating a globally-inclusive identity and financial network, owned by the majority of humanity. If successful, World Network could considerably increase economic opportunity, scale a reliable solution for distinguishing humans from AI online while preserving privacy, enable global democratic processes, and show a potential path to AI-funded UBI.
World Network consists of a privacy-preserving digital identity network (World ID) built on proof of human and, where laws allow, a digital currency (WLD). Every human has access to WLD tokens simply for being human. World ID and WLD token are currently complemented by World App, the first frontend to World ID and World Network, developed by the contributor team at Tools for Humanity (TFH).
“Proof of human” is one of the core ideas behind World, and refers to establishing an individual is both human and unique. Once established, it gives the individual the ability to assert they are a real person and different from another real person, without having to reveal their real-world identity.
Today, proof of human is an unsolved problem on a global scale, making it difficult to vote online or distribute value on a large scale. The problem is even more pressing as increasingly powerful AI models will further amplify the difficulty of distinguishing humans from bots. If successful as part of World Network, World ID could become a global proof of human standard.
Some of the core assumptions behind World are:
- Proof of human is a missing and necessary digital primitive. This primitive will become more important as increasingly powerful AI models become available.
- Scalable and inclusive proof of human, for the first time, allows aligning the incentives of all network participants around adding real humans to the network. Bitcoin is issued to secure the Bitcoin network. Worldcoin is issued to grow the World Network, with security inherited from Ethereum.
- In a time of increasingly powerful AI, the most reliable way to issue a global proof of human is through custom biometric hardware.
The following dynamic Whitepaper shares the reasoning behind the implementation of the project as well as the current state and roadmap.
World ID
World ID is privacy preserving proof of human. It enables users to verify their humanness online while maintaining their privacy through zero-knowledge proofs, via a custom biometric device called the Orb. The Orb has been designed based on the realization that custom biometric hardware might be the only long term viable solution to issue AI-safe proof of human verifications. World IDs are issued on World Network, which allows individuals to prove that they are human to any verifier (including web2 applications) while maintaining their privacy through zero-knowledge proofs. In the future, it should be possible to issue other credentials on the protocol as well.
World ID aspires to be personbound, meaning a World ID should only be used by the individual it was issued to. It should be very difficult to use by a fraudulent actor who stole or acquired World ID credentials.
Worldcoin (WLD)
While network effects will ultimately come from useful applications being built on top of the financial and identity infrastructure, the token is issued to all network participants to align their incentives around the growth of the network. This is especially important early on to bootstrap the network and bypass the “cold start problem”.
World App
World App is the first frontend to World ID: it guides individuals through the verification with the Orb, custodies an individual’s World ID credentials and implements the cryptographic protocols to share those credentials with third parties in a privacy preserving manner. It is designed to provide frictionless access to global decentralized financial infrastructure. Eventually, there should be many different wallets integrating World ID.
How does World Work?
World revolves around World ID, a privacy-preserving global identity network. Using World ID, individuals will be able to prove that they are a real, unique human to any platform that integrates with the protocol. This will enable fair airdrops, provide protection against bots/sybil attacks on social media, and enable the fairer distribution of limited resources. Furthermore, World ID can also enable global democratic processes and novel forms of governance (e.g., via quadratic voting), and it may eventually support a path to AI-funded UBI.
To engage with the World Network protocol, individuals must first download World App, the first wallet app that supports the creation of a World ID. Individuals visit a physical imaging device called the Orb to get their World ID Orb-verified. Most Orbs are operated by a network of independent local businesses called Orb Operators. The Orb uses multispectral sensors to verify humanness and uniqueness to issue an Orb-verified World ID, with all images being promptly deleted on-device per default (absent explicit consent to Data Custody).
Potential Applications
World could significantly increase equality of opportunity globally by advancing a future where everyone, regardless of their location, can participate in the global digital economy through universally-accessible decentralized financial and identity infrastructure. As the network grows, so should its utility.
Today, many interactions in the digital realm are not possible globally. The way humans transact value, identify themselves, and interact on the internet is likely to change fundamentally. With universal access to finance and identity, the following future becomes possible:
Finance
Owning & Transferring Digital Money: Sending money will be near instant and borderless, globally. Available to everyone. The world could be connected financially and everyone would be able to interact economically on the internet. The COVID relief fund for India, where over $400 million was raised in a short period of time by individuals around the world to support the country is a hint at what can be possible. Overall, this has the potential to connect people on a global scale unlike anything previously seen in human history.
Digital money is safer than cash, which can be more easily stolen or forged. This is especially important in crisis situations where instant cross-border financial transactions need to be possible, such as during the Ukrainian refugee crisis, where USDC was used to distribute direct aid. Additionally, digital money is an asset that individuals can own and control directly without having to trust third parties.
Identity
Keep the Bots Out: Bots on Twitter, spam messages, and robocalls are all symptoms of the lack of sound and frictionless digital identity. These issues are exacerbated by rapidly advancing AI models, which can solve CAPTCHAs and produce content that is convincingly "human". As services ramp up defenses against such content, it becomes essential that an inclusive and privacy-preserving solution for proof of human is available as public infrastructure. If every message or transaction included a "verified human" property, a lot of noise could be filtered from the digital world.
Governance: Currently, collective decision making in web3 largely relies on token-based governance (one token, one vote), which excludes some people from participating and heavily favors those with more economic power. A reliable sybil-resistant proof of human like World ID opens up the design space for global democratic governance mechanisms not just in web3 but for the internet. Additionally, for AI to maximally benefit all humans, rather than just a select group, it will become increasingly important to include everyone in its governance.
Intersection of Finance and Identity
Incentive Alignment: Coupons, loyalty programs, referral programs and more generally sharing value with customers are traditionally prone to fraud as the incentives for fraudulent actors are high. Frictionless and fraud resistant digital identity helps to align incentives and benefit both consumers and companies. This could even incept a new wave of companies owned in part by their users.
Equal Distribution of Scarce Resources: Crucial elements of modern society, including subsidies and social welfare, can be rendered more equitably by employing proof of human. This is particularly pertinent in developing economies, where social benefit programs confront the issue of resource capture—fake identities employed to acquire more than a person’s fair share of resources. In 2021, India saved over $500 million in subsidy programs by implementing a biometric-based system that reduced fraud. A decentralized proof of human protocol can extend similar benefits to any project or organization globally. As AI advances, fairly distributing access and some of the created value through UBI will play an increasingly vital role in counteracting the concentration of economic power. World ID could ensure that each individual registers only once and to guarantee equitable distribution.
Proof of human (PoH)
Different applications have different requirements for PoH. For high-stakes use cases such as global UBI, the democratic governance of AI and the World Network, a highly secure and inclusive PoH mechanism to prevent multiple registrations is needed. Therefore, the World Network developer community with the World Foundation is laying the foundations for a high-assurance PoH mechanism with World ID. World IDs are issued to every unique human through biometric verification devices, with the first such device being the Orb. The following sections walk through the fundamental building blocks of PoH and how those are implemented in the context of World ID.
Building Blocks
On a high level, there are several building blocks that are required for an effective PoH mechanism. Those include “deduplication” to ensure everyone can only verify once, “authentication” to ensure only the legitimate owner of the proof of human credential can use it and “recovery” in case of lost or compromised credentials. This section discusses those building blocks on a high level.
A proof of human mechanism consists of three different actors and the data that they exchange.
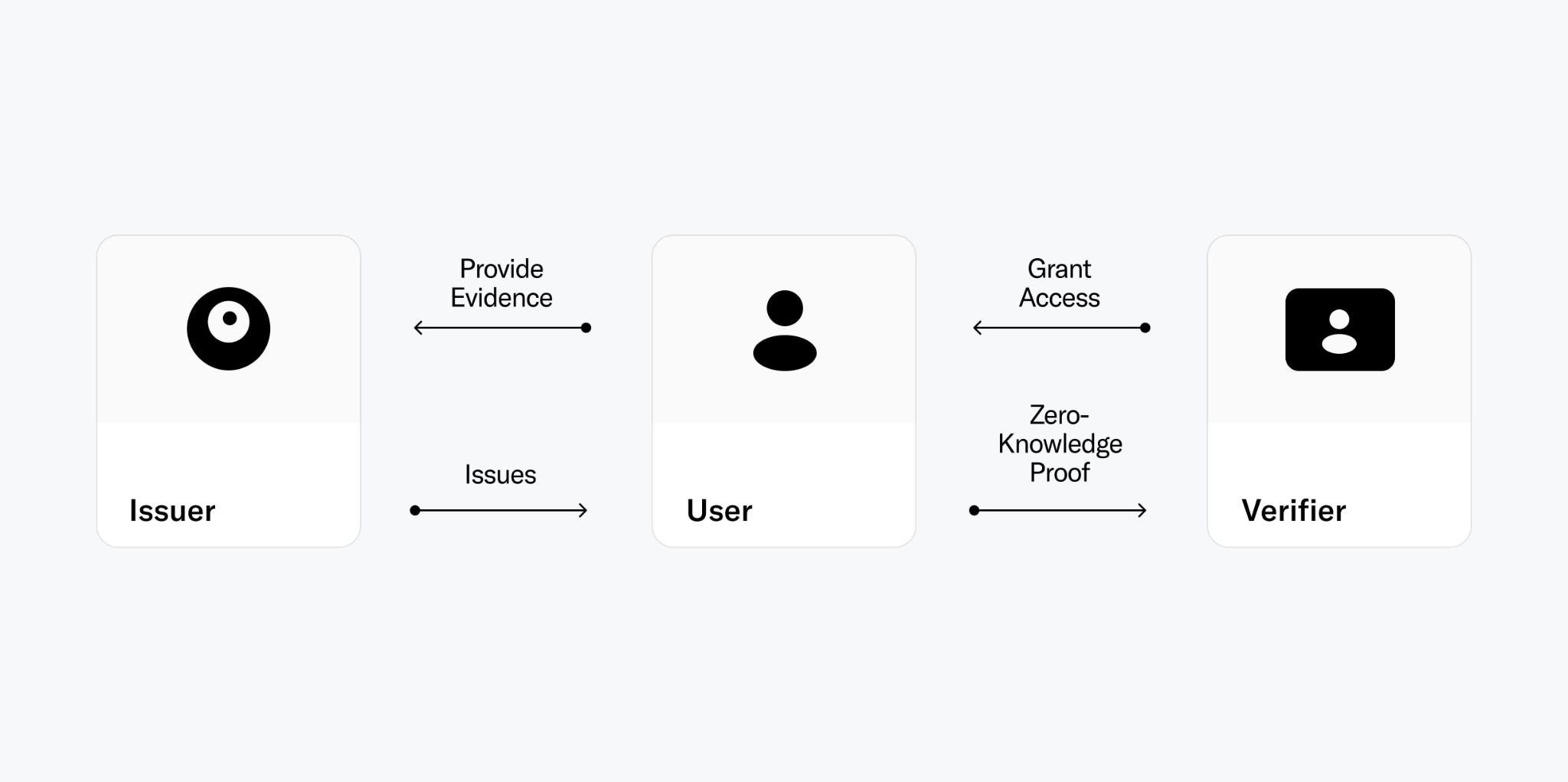
For the context of this section, these terms are defined as follows:
- User: An individual seeking to prove specific claims about herself in order to access certain resources or more generally qualify for certain actions. Within the context of a H protocol those claims are related to proving uniqueness and personhood.
- Credential: A collection of data that serves as proof for particular attributes of the user that indicate the user is a human being. This could be a range of things, from the possession of a valid government ID to being verified as human and unique through biometrics.
- Issuer: An trusted entity that affirms certain information about the user and grants them a PoH credential, which enables the user to prove their claims to others.
- Verifier: An entity that examines a user's PoH credential and checks its authenticity as part of a verification process to grant the user access to certain actions.
Certain interactions between users, issuers and verifiers, like deduplication, recovery and authentication are important building blocks for a functional PoH mechanism. This section gives a high level overview of the building blocks of a general PoH mechanism. Detailed explanations on how those are implemented with World ID follow in later sections.

Deduplication
For a PoH to be useful, it needs to have a notion of uniqueness. If the PoH can be acquired multiple times and transferred to fraudulent actors or bots, it cannot be trusted and fails to serve its purpose. Therefore, a PoH mechanism needs to deduplicate between the users that are issued a proof of human credential. This is the hardest challenge for any PoH mechanism.
Authentication
To make PoH credentials useful it needs to be hard to transfer credentials to someone else (e.g. bots) and for them to use the credentials to prevent fraud. This is especially important to protect individuals who may be unaware of the consequences of selling their credentials. This challenge is inherent in identity systems as a whole. Authentication can prevent fraudsters from using credentials, even if the respective user is unaware or attempts to collaborate with the fraudster.
When issuing PoH credentials, issuers only need to validate that someone is indeed a unique person. Beyond that, no additional personal information is required. However, each PoH credential needs to be uniquely tied to a specific person. Even if credentials are not transferable, wallets and phones can be transferred. Therefore, for high-integrity use cases, it is crucial to authenticate the user as the rightful owner of the PoH credential. This prevents the unauthorized use of credentials. A similar approach is followed during e.g. airline boarding, where an airline gate assistant verifies both the possession of a valid travel document and the consistency of the individual's identity with the document.
Recovery
If the user has lost access to their credentials or their credentials have been compromised, effective recovery mechanisms are needed. However, in setups where users are responsible for managing their own keys, this is a significant challenge. In the context of a PoH protocol, there are multiple mechanisms that can be used:
- Restoring a User-Managed Backup: The simplest method for credential recovery involves storing encrypted user-managed backups of their credentials. This allows users to restore their credentials, such as on a new device when their previous one is lost.
- Social Recovery: If no user-managed backup exists, but the user has set up social recovery, the credentials can be recovered through the help of friends and family.
- Recover Keys: If neither backups nor social recovery are available, the user needs to return to the issuer to regain access to their original credential. The user needs to prove to the issuer that they are the legitimate owner of a certain credential. Upon successful authentication, the issuer grants access to the credential again. This process is similar to obtaining a new government ID after losing the previous one. The user can get a new ID with the same information on it1. This process may not be viable for some credentials: for example, if a private key was generated by the user and only the public key is recorded by the issuer (e.g. World ID).
- Re-Issuance: In situations where regaining access to the original credential through the issuer is not possible or undesirable (e.g. due to identity theft). In that case, re-issuance provides a way to invalidate the previous credential and issue a new credential. This can be compared to freezing a credit card and ordering a new one. Importantly, the availability of a re-issuance mechanism to rotate keys makes the illegitimate acquisition of other individuals’ PoH credentials financially unviable from a game-theoretic perspective. The true holder of the credential can always recover their credentials and invalidate the bought/stolen credential. However, this does not protect against all cases of identity transfer, especially those that involve collusion or coercion.
Two other properties add to the integrity of a PoH mechanism:
Revocation
While the hope is that all participants act with integrity, this cannot be assumed. In instances where an issuer is found to be compromised or malicious, the impact can be mitigated by issuers or developers removing affected PoH credentials from their list of accepted credentials. If the issuance of a credential is decentralized across multiple issuing locations and only a subset is affected, the respective subset could be revoked by the issuing authority itself. An example in terms of today's credentials could be a university granting a diploma to a person who hasn't met all the criteria. If the fraud is identified, the diploma is revoked.
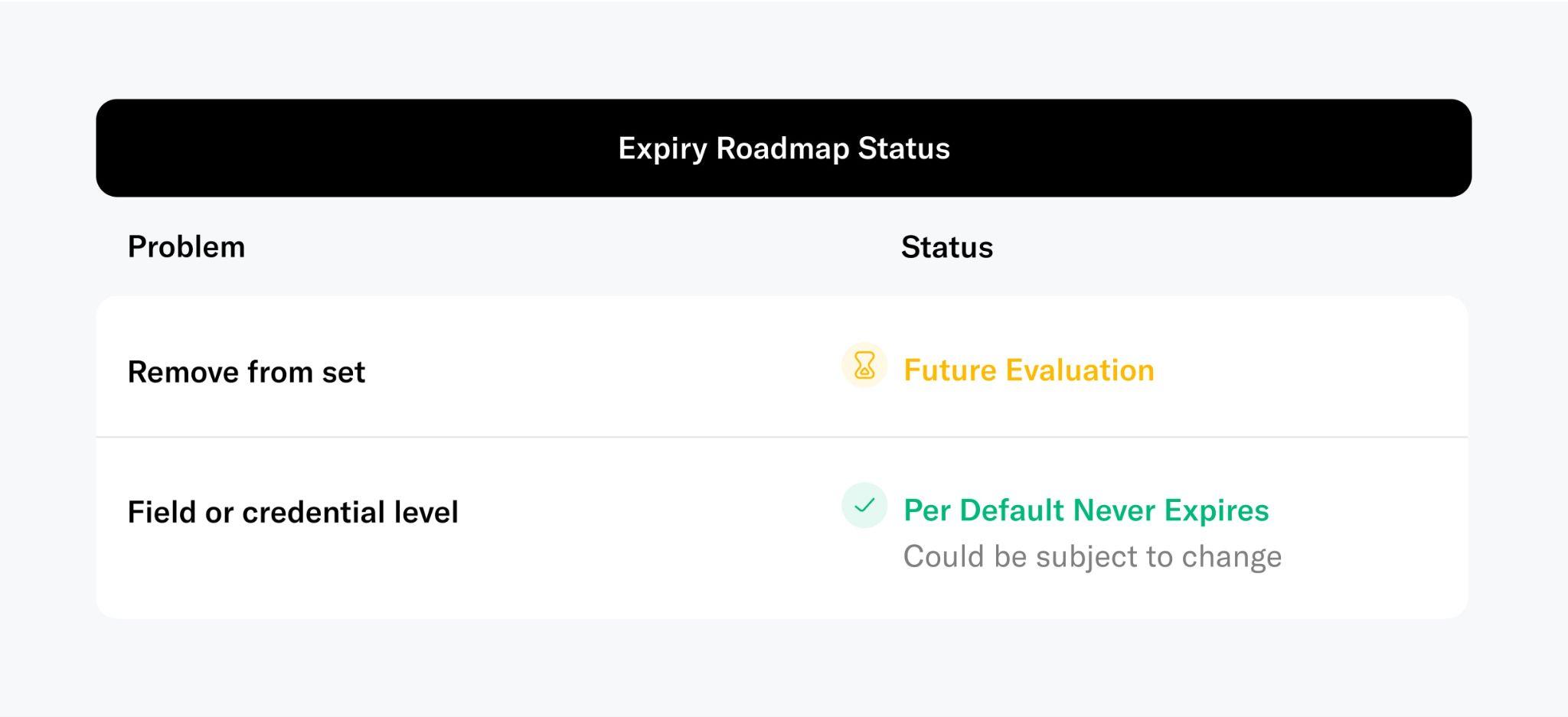
Expiry
The efficacy of security mechanisms degrades over time and new mechanisms are continuously being developed. As a result, many identity systems incorporate a predefined expiry date to credentials at the point of issuance. An example are passports. Although expiry is not required for a PoH mechanism to work, its inclusion can increase the PoH’s integrity.
The combination of the mentioned building blocks make up for a functional proof of human mechanism. An exemplary smartphone App is shown in the following figure.

Solving PoH at Scale
Based on these high level building blocks, several requirements can be deduced to evaluate different approaches to a global PoH mechanism:
- Inclusivity and scalability: A global PoH should be maximally inclusive, i.e. available to everyone. This means the mechanism should be able to distinguish between billions of people. There should be a feasible path to implementation at a global scale and people should be able to participate regardless of nationality, race, gender or economic means.
- Fraud Resistant: For a global proof of human, the important part is not “identification” (i.e. “is someone who they claim they are?”), but rather negative identification (i.e.“has this person registered before?”). This means that fraud prevention, in terms of preventing duplicate sign-ups, is critical. A significant amount of duplicates would severely restrict the design space of possible applications and make it impossible to treat all humans equally. This would have severe implications for use cases like a fair token distribution, democratic governance, reputation systems like credit scores, and welfare (including UBI).
- Personbound: Once a proof of human is issued, it should be personbound: it should be hard to sell or steal (i.e. transfer) and hard to lose. Note that if the PoH mechanism is designed properly, this wouldn’t prevent pseudonymity. This leads to the requirement that the proof of human mechanism should allow for authentication in a way that makes it hard for fraudsters to impersonate the legitimate individual. Further, even if the individual lost all information, irrespective of any past actions, it should always be possible for them to recover.
Those cover the requirements that can be deduced from the required building blocks of a proof of human mechanism. However, there are further important requirements that can be deduced from the values inherent to the World:
- Decentralization: The issuance of a global proof of human credential is foundational infrastructure that should not be controlled by a single entity to maximize resilience and integrity.
- Privacy: The proof of human mechanism should preserve the privacy of individuals. Data shared by individuals should be minimized. Users should be in control of their data.
Mechanisms to Verify Uniqueness Among Billions
Based on the above requirements, this section compares different mechanisms to establish a global proof of human mechanism in the context of the World Network.

Online accounts
The simplest attempt to establish proof of human at scale involves using existing accounts such as email, phone numbers and social media. This method fails, however, because one person can have multiple accounts on each kind of platform. Further, accounts aren’t personbound i.e. they can be easily transferred to others. Also, the (in)famous CAPTCHAs, which are commonly used to prevent bots, are ineffective here because any human can pass multiple of them. Even the most recent implementations2that basically rely on an internal reputation system, are limited.
In general, current methods for deduplicating existing online accounts (i.e. ensuring that individuals can only register once), such as account activity analysis, lack the necessary fraud resistance to withstand substantial incentives. This has been demonstrated by large-scale attacks targeting even well-established financial services operations.
Official ID verification (KYC)
Online services often request proof of ID (usually a passport or driver's license) to comply with Know your Customer (KYC) regulations. In theory, this could be used to deduplicate individuals globally, but it fails in practice for several reasons.
KYC services are simply not inclusive on a global scale; more than 50% of the global population does not have an ID that can be verified digitally. Further, it is hard to build KYC verification in a privacy–preserving way. When using KYC providers, sensitive data needs to be shared with them. This can be solved using zkKYC and NFC readable IDs. The relevant data can be read out by the user's phone and be locally verified as it is signed by the issuing authority. Proving unique humanness can be achieved by submitting a hash based on the information of the user’s ID without revealing any private information. The main drawback of this approach is that the prevalence of such NFC readable IDs is considerably lower than that of regular IDs.
Where NFC readable IDs are not available, ID verification can be prone to fraud—especially in emerging markets. IDs are issued by states and national governments, with no global system for verification or accountability. Many verification services (i.e. KYC providers) rely on data from credit bureaus that is accumulated over time, hence stale, without the means to verify its authenticity with the issuing authority (i.e. governments), as there are often no APIs available. Fake IDs, as well as real data to create them, are easily available on the black market. Additionally, due to their centralized nature, corruption at the level of the issuing and verification organizations cannot be eliminated.
Even if the authenticity of provided data can be verified, it is non-trivial to establish global uniqueness among different types of identity documents: fuzzy matching between documents of the same person is highly error-prone. This is due to changes in personal information (e.g. address), and the low entropy captured in personal information. A similar problem arises as people are issued new identity documents over time, with new document numbers and (possibly) personal information. Those challenges result in large error rates both falsely accepting and rejecting users. Ultimately, given the current infrastructure, there is no way to bootstrap global proof of human via KYC verification due to a lack of inclusivity and fraud resistance.
Web of Trust
The underlying idea of a “web of trust” is to verify identity claims in a decentralized manner.
For example, in the classic web of trust employed by PGP, users meet for in-person “key signing parties” to attest (via identity documents) that keys are controlled by their purported owners. More recently, projects like Proof of Humanity are building webs of trust for Web3. These allow decentralized verification using face photos and video chat, avoiding the in-person requirement.
Because these systems heavily rely on individuals, however, they are susceptible to human error and vulnerable to sybil attacks. Requiring users to stake money can increase security. However, doing so increases friction as users are penalized for mistakes and therefore disincentivized to verify others. Further, this decreases inclusivity as not everyone might be willing or able to lock funds. There are also concerns related to privacy (e.g. publishing face images or videos) and susceptibility to fraud using e.g. deep fakes, which make these mechanisms fail to meet some of the design requirements mentioned above.
Social graph analysis
The idea of social graph analysis is to use information about the relationships between different people (or the lack thereof) to infer which users are real.
For example, one might infer from a relationship network that users with more than 5 friends are more likely to be real users. Of course, this is an oversimplified inference rule, and projects and concepts in this space, such as EigenTrust, Bright ID and soulbound tokens (SBTs) propose more sophisticated rules. Note that SBTs aren’t designed to be a proof of human mechanism but are complementary for applications where proving relationships rather than unique humanness is needed. However, they are sometimes mentioned in this context and are therefore relevant to discuss.
Underlying all of these mechanisms is the observation that social relations constitute a unique human identifier if it is hard for a person to create another profile with sufficiently diverse relationships. If it is hard enough to create additional relationships, each user will only be able to maintain a single profile with rich social relations, which can serve as the user's proof of human. One key challenge with this approach is that the required relationships are slow to build on a global scale, especially when relying on parties like employers and universities. It is a priori unclear how easy it is to convince institutions to participate, especially initially, when the value of these systems is still small. Further, it seems inevitable that in the near future AI (possibly assisted by humans acquiring multiple “real world” credentials for different accounts) will be able to build such profiles at scale. Ultimately, these approaches require giving up the notion of a unique human entirely, accepting the possibility that some people will be able to own multiple accounts that appear to the system as individual unique identities.
Therefore, while valuable for many applications, the social graph analysis approach also does not meet the fraud resistance requirement for proof of human laid out above.
Biometrics
Each of the systems described above fails to effectively verify uniqueness on a global scale. The only mechanism that can differentiate people in non-trusted environments is their biometrics. Biometrics are the most fundamental means to verify both humanness and uniqueness. Most importantly, they are universal, enabling access irrespective of nationality, race, gender or economic means.Additionally, biometric systems can be highly privacy-preserving if implemented properly. Further, biometrics enable the previously mentioned building blocks by providing a recovery mechanism (that works even if someone has forgotten everything) and can be used for authentication. Therefore, biometrics also enable the proof of human credential to be personbound.
Different systems have different requirements. Authenticating a user via FaceID as the rightful owner of a phone is very different from verifying billions of people as unique. The main differences in requirements relate to accuracy and fraud resistance. With FaceID, biometrics are essentially being used as a password, with the phone performing a single 1:1 comparison against a saved identity template to determine if the user is who they claim to be. Establishing global uniqueness is much more difficult. The biometrics have to be compared against (eventually) billions of previously registered users in a 1:N comparison. If the system is not accurate enough, an increasing number of users will be incorrectly rejected.
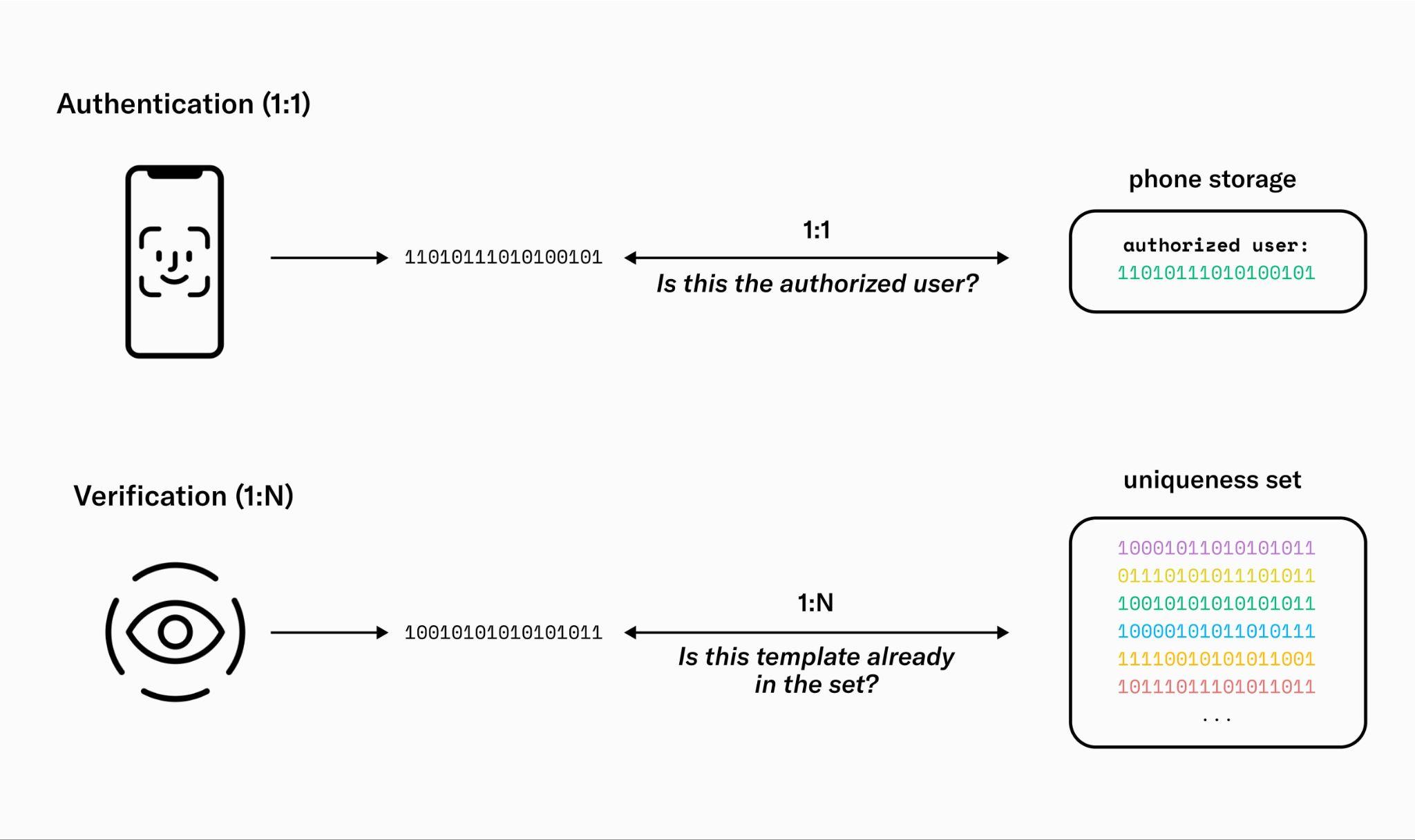
The error rates and therefore the inclusivity of the system are majorly influenced by the statistical characteristics of the biometric features being used. Iris biometrics outperform other biometric modalities and can achieve false match rates beyond (or one false match in 40 trillion). This is several orders of magnitude more accurate than the current state of the art in face recognition. Moreover, the structure of the iris exhibits remarkable stability over time.
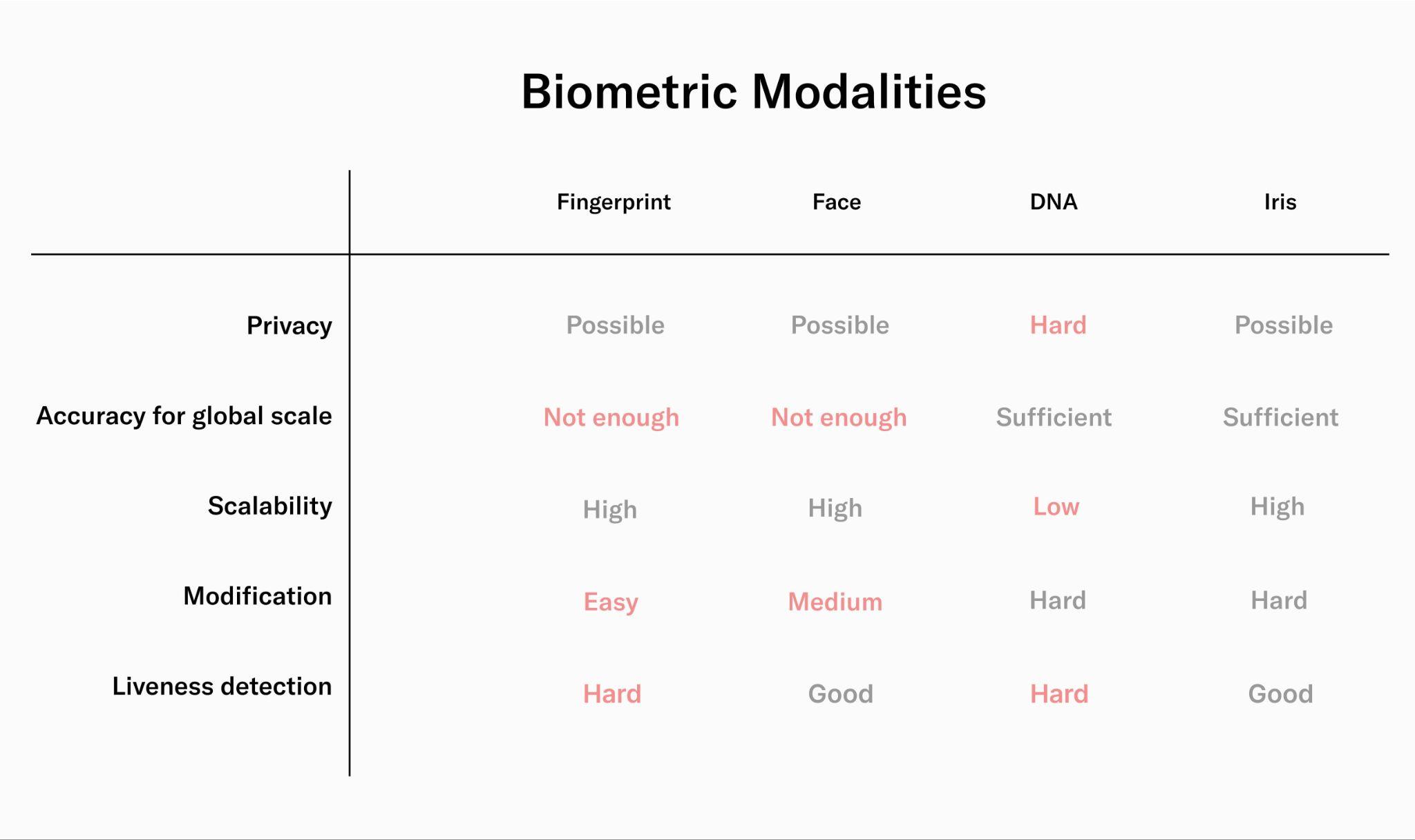
Furthermore, the iris is hard to modify. Modifying fingerprints through cuts is easy, while imaging them accurately can be difficult, as the ridges and valleys can wear off over time. Moreover, using all ten fingerprints for deduplication or combining different biometric modalities is vulnerable to combinatorial attacks (e.g. by combining fingerprints from different people). DNA sequencing could in theory provide high enough accuracy, but DNA reveals a lot of additional private information about the user (at least to the party that runs the sequencing). Additionally, it is hard to scale from a cost perspective and implementing reliable liveness detection measures is hard. Facial biometrics offers significantly better liveness detection compared to DNA sequencing. However, compared to iris biometrics, the accuracy of facial recognition is much lower. This would result in a growing number of erroneous collisions as the number of registered users increases. Even under optimal conditions, at a global scale of billions of people, over ten percent of legitimate new users would be rejected, compromising the inclusivity of the system.
Therefore, based on the outlined trade-offs of different biometric modalities, iris recognition is the only one which is suitable for global verification of uniqueness in the context of the World Network.
World ID: Implementing Proof of Human at Scale
Based on the conclusion that the only path to verify uniqueness on a global scale is iris biometrics, Tools for Humanity built a custom biometric device, called the Orb. This device issues an AI-safe3 proof of human credential called World ID. The Orb is built from the ground up to verify humanness and uniqueness in a fair and inclusive manner.

The issuance of World ID is privacy-preserving, as the humanness check happens locally and no images need to be saved (or uploaded) by the issuer. Using World ID reveals minimal information about the individual, as the protocol employs zero-knowledge proofs. The vision for the device is for its development, production and operation to be decentralized over time such that no single entity will be in control of World ID issuance.
The following section explains the previously mentioned building blocks for an effective proof of human mechanism:
- Deduplication
- Authentication
- Recovery
- Revocation
- Expiry
and how they are implemented in the context of World ID.
Deduplication
The hardest part for an inclusive yet highly secure proof of human mechanism is to make sure every user can receive exactly one proof of human. Based on the previous evaluation iris biometrics are the best means to accurately verify uniqueness on a global scale (see limitations).
The other potential error inherent to biometric algorithms is the false acceptance of a user. The false acceptance rate is largely dependent upon the system's capacity to detect presentation attacks, which are attempts to deceive or spoof the verification process. While no biometric system is entirely impervious to such attacks, the important metric is the effort required for a successful attack. This consideration was fundamental to the conception of the Orb. Developing the Orb was a decision that did not come lightly. It represented a high-cost endeavor. However, from first principles, it was required to build the most inclusive yet secure verification of humanness and uniqueness. The Orb is designed to verify uniqueness with high accuracy, even in hostile contexts where the presence of malicious actors cannot be excluded. To accomplish this, the Orb is equipped with every viable camera sensor spanning the electromagnetic spectrum, complemented by suitable multispectral illumination. This enables the device to differentiate between fraudulent spoofing attempts and legitimate human interactions with a high degree of accuracy. The Orb is further equipped with a powerful computing unit to run several neural networks concurrently in real-time. These algorithms operate locally on the Orb to validate humaneness, while safeguarding user privacy. While no hardware system interacting with the physical world can achieve perfect security, the Orb is designed to set a high bar, particularly in defending against scalable attacks. The anti-fraud measures integrated into the Orb are refined constantly.
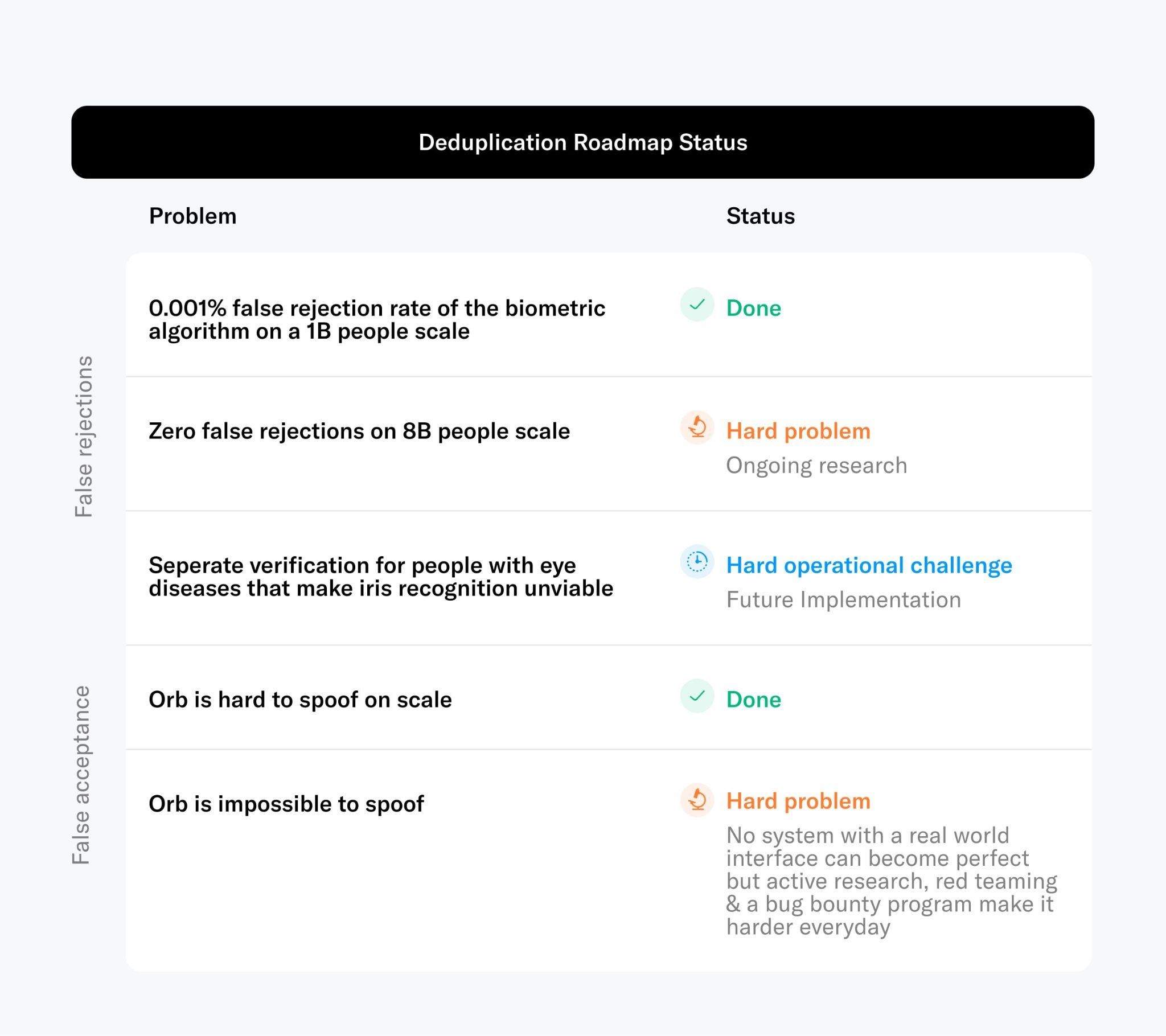
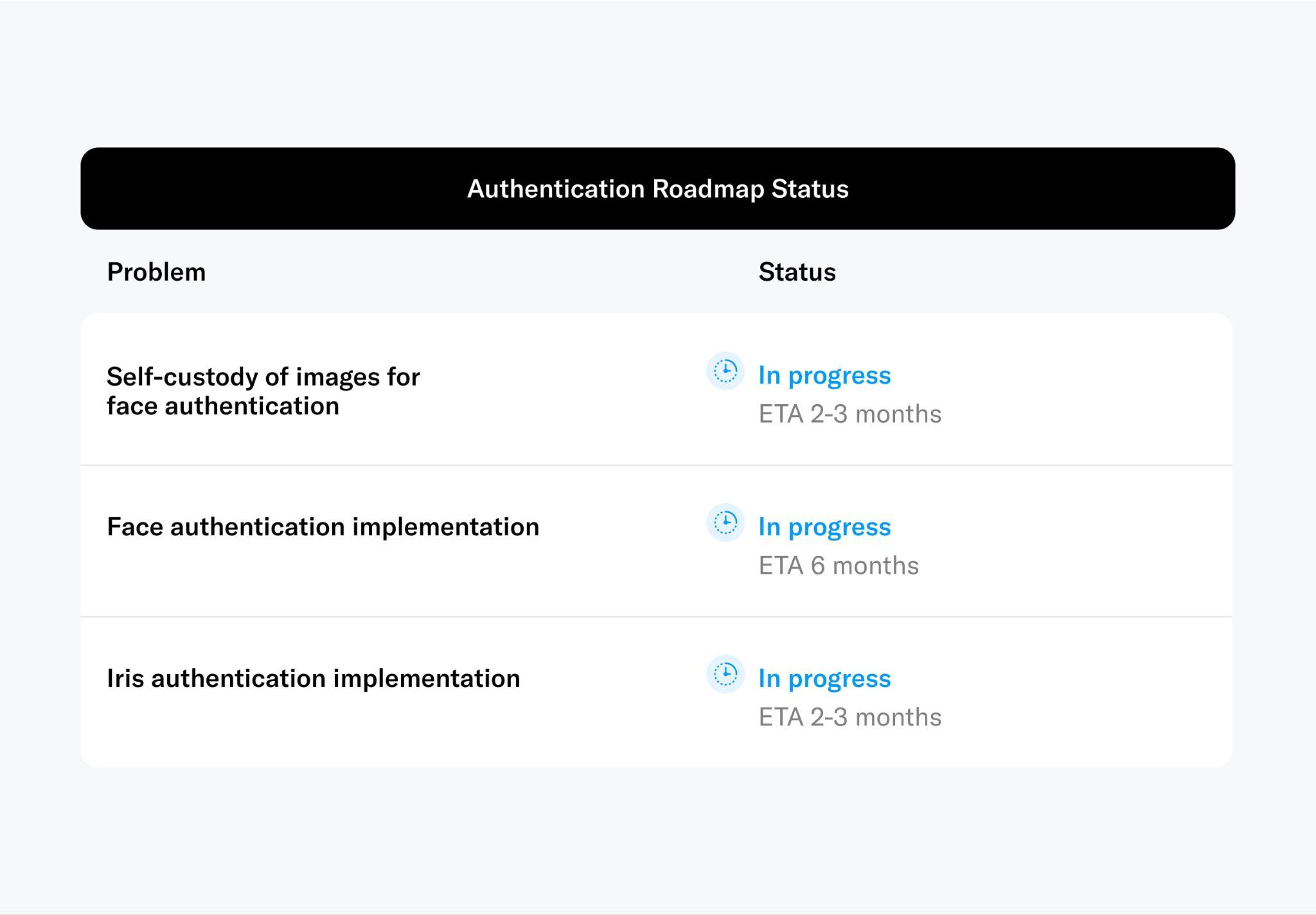
Authentication
Authentication seeks to ensure that only the legitimate owner of a World ID issued by the Orb is able to authenticate themself beyond proving that they own the keys. This plays a critical role in preventing the selling or stealing of World IDs. Within the scope of World ID, there are two primary mechanisms at one's disposal. Selecting the appropriate mechanism is up to the verifier, as each mechanism offers varying degrees of assurance and friction.
Face Authentication
Face-based authentication is similar to Apple's Face ID. Authentication involves a 1:1 comparison with a pre-existing template that is stored on the user's phone, which requires considerably lower levels of accuracy in contrast to the 1:N global verification of uniqueness4 that the Orb is performing. Therefore, the entropy inherent to facial features is sufficient. To enable this feature, an encrypted embedding of the user's face, signed by the Orb, is end-to-end encrypted and transmitted to the World ID wallet on the user's mobile device. Subsequently, facial recognition, performed locally on the user’s device in a fashion similar to Face ID, could be used to authenticate users, thereby ensuring that only the person to whom the World ID was originally issued can use it for authentication purposes.
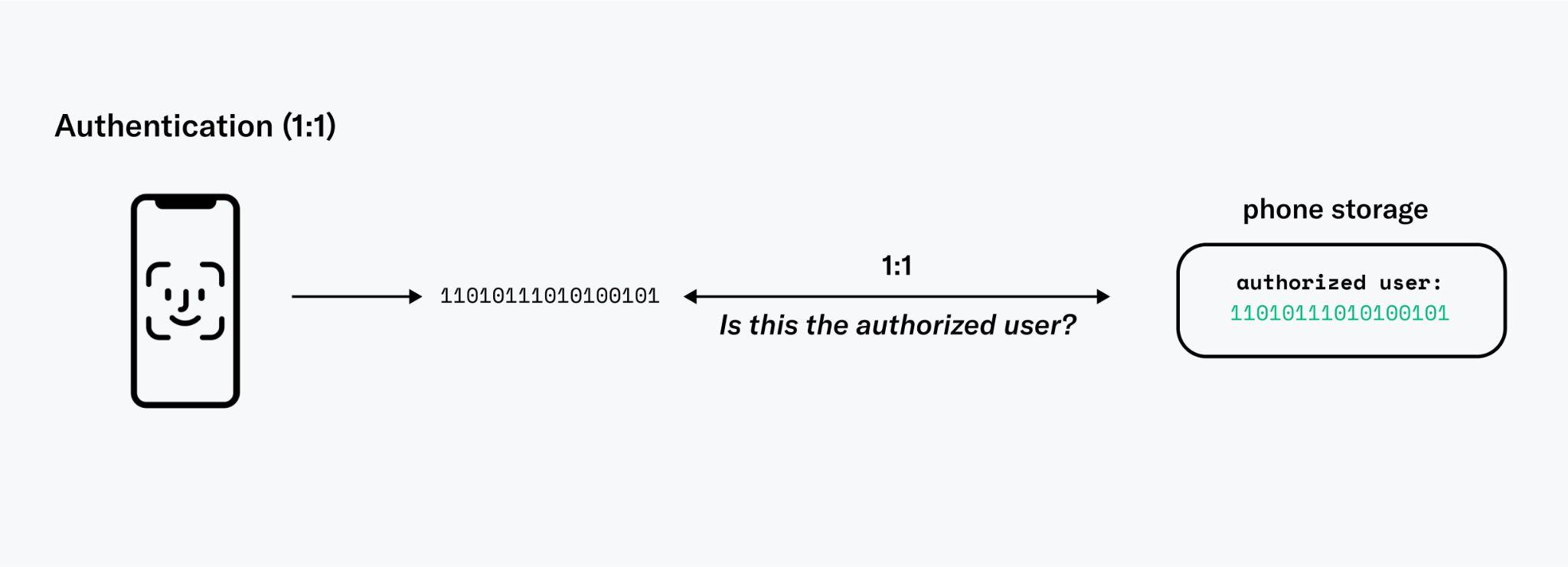
This mechanism facilitates the extension of the secure hardware guarantees from the Orb to the user's mobile device. However, given that the user's device is not intrinsically trusted, there is no absolute assurance that the appropriate code is being executed nor that the camera input can be trusted. To increase security, ongoing research is investigating Zero Knowledge Machine Learning (ZKML) on mobile devices. Nevertheless, in the absence of custom hardware, this approach cannot provide the same security guarantees as the Orb. Therefore, face authentication on the user's device should be reserved for applications with lower stakes.
While this feature is not yet implemented, it is expected to be released later this year. The first step for the implementation is for the Orb to send an end-to-end encrypted face embedding to the user's phone where it can later be compared against a selfie. The self-custody of face images is a requirement for face authentication and therefore determines who can later on participate in face authentication. Therefore, this feature has a high priority on the roadmap.
Iris Authentication
This is conceptually similar to face authentication with the difference that a user needs to return to an Orb, presenting a specific QR code generated by the user’s World ID wallet. This process validates the individual as the rightful owner of their World ID. Using iris authentication through the Orb increases security.
This authentication mechanism can be compared with, for example, physically showing up to a bank or notary to authenticate certain transactions. Although inconvenient, and therefore rarely required, it provides increased security guarantees. This feature is under active development and is expected to be released in the coming months.
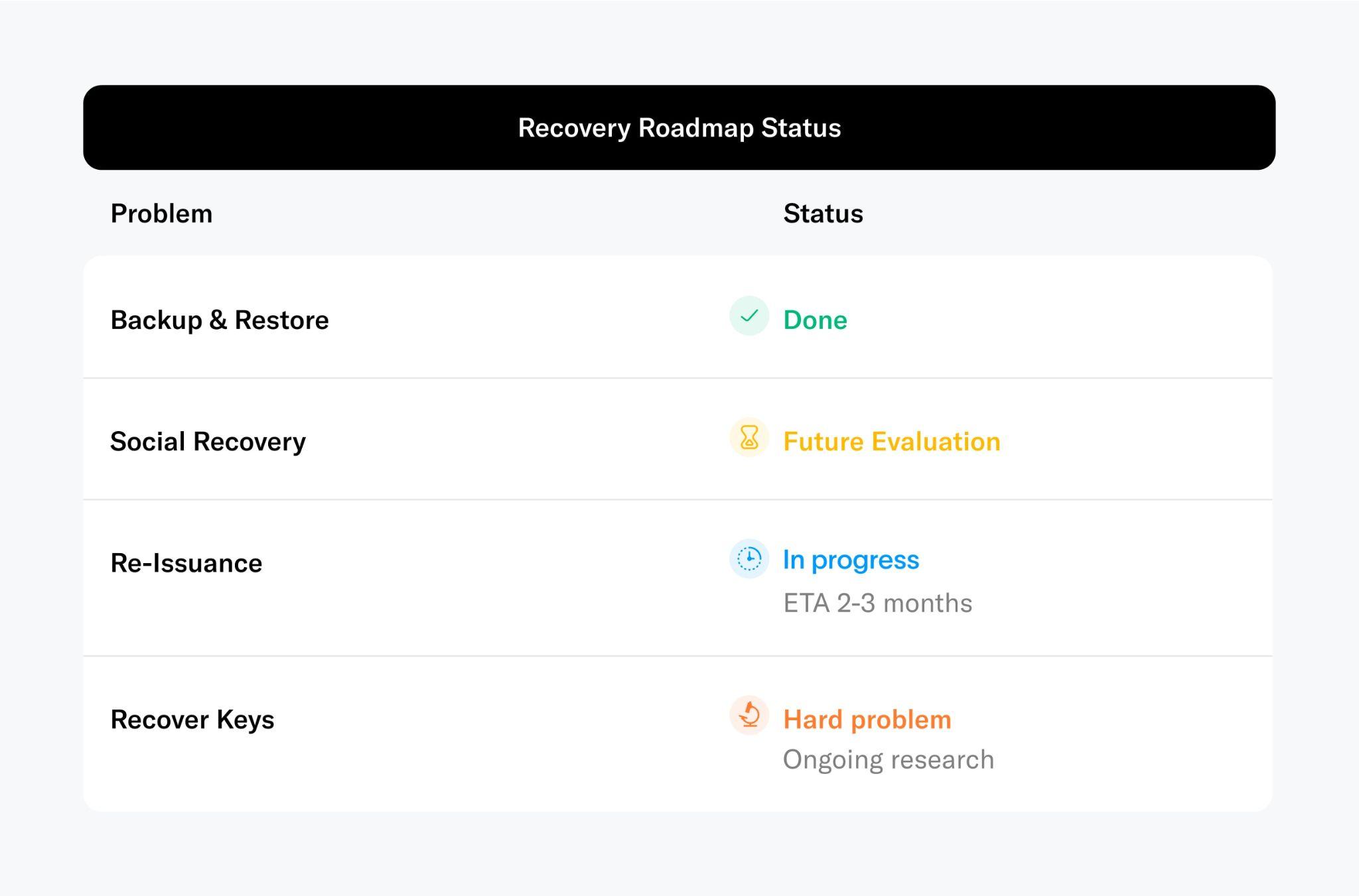
Recovery
The simplest way to restore World ID is via a backup. Social recovery is not implemented today but is likely to be explored in the future. The most important recovery mechanism for Orb-based proof of human is reissuance. If the user has lost access or the World ID has been compromised by a fraudulent actor, individuals can get their World ID re-issued by returning to the Orb, without the need to remember a password or similar information.
It is critical to understand, however, that the recovery facilitated by biometrics exclusively refers to the World ID. Neither other credentials held by the user's wallet nor the wallet itself can be recovered, due to security considerations.
The initial implementation is planned to be realized through key rotation, which will be released soon. Notably, use cases that require long-lasting nullifiers5 such as reputation or single-claim rewards will be limited due to the nullifier’s potential reset through recovery. This is also discussed in the limitations section. However, this limitation does not impact the 'humanness' attestation; for instance, the verification of an account on a continuous basis through sessions, or time-bounded votes where only participants whose latest recovery preceded the beginning of the voting period are allowed. To enable key recovery requires solving hard research challenges to preserve privacy.
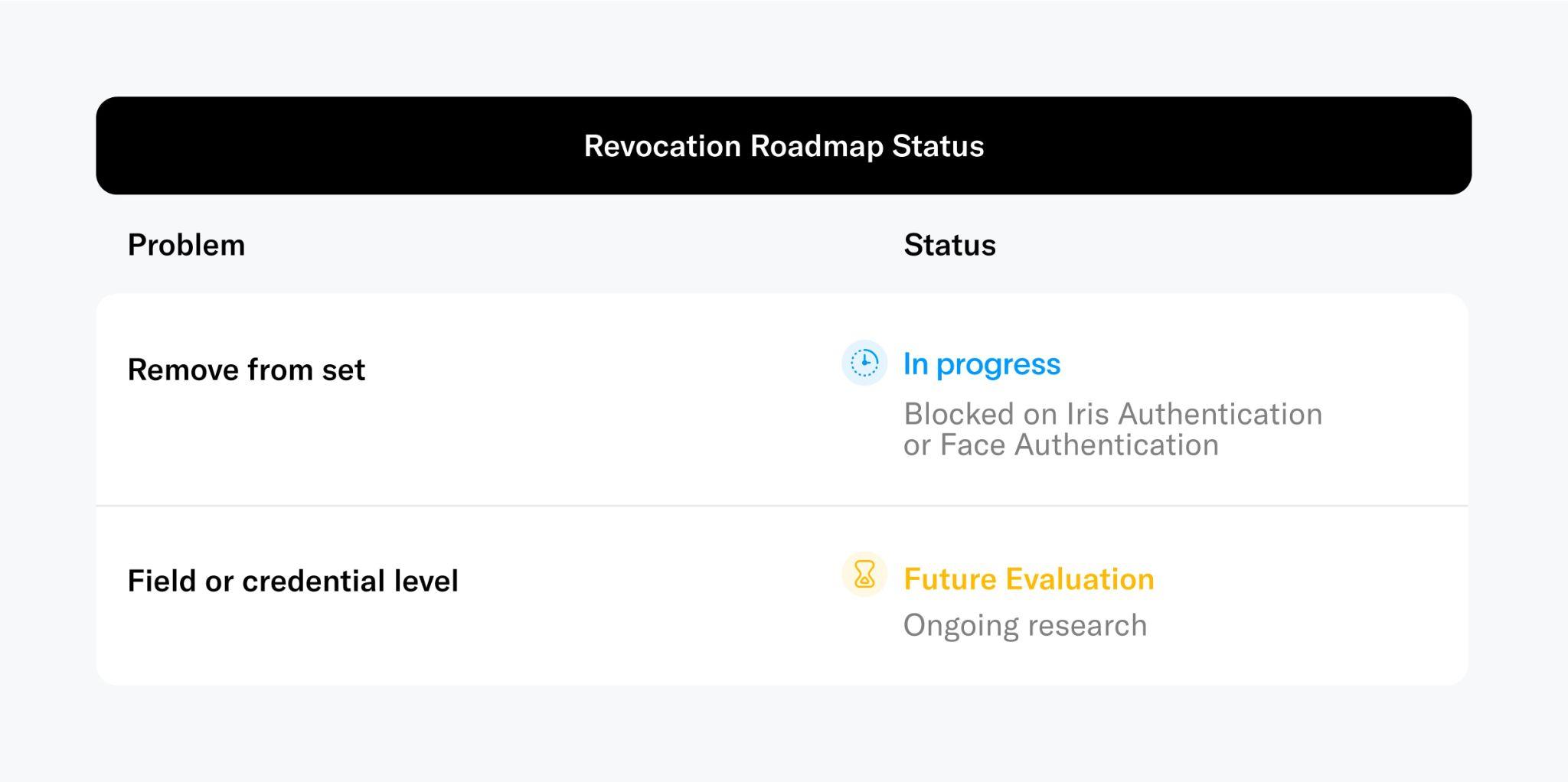
Revocation
In the event of a compromised Orb, malicious actors could theoretically generate counterfeit World IDs6. If it is determined by the community that an issuer is acting inappropriately or a device is compromised, the World Foundation, in alignment with the prevailing governance structure, can "deny list" World IDs linked to a specific issuer or device for its own purposes, while other application developers can implement their own measures. Users who inadvertently find themselves impacted can simply get their World ID re-issued by any other Orb. More details around the mechanism can be found in the decentralization.
Expiry
Even in the absence of tangible fraudulent activities, a device could retrospectively be identified by the community as vulnerable, or simply as having outdated security standards. In such instances, in line with the governing principles of the Foundation, World IDs can be subjected to a set expiry. This essentially amounts to a revocation process but with a predefined expiry period that affords individuals ample time for re-verification, such as one year. Further, in accordance with its governance, the Foundation could eventually decide to expire verifications after a set period of time to further strengthen the integrity of the proof of human mechanism in the interest of all participants.
Further Research
Despite the defensive measures outlined in this section, which significantly raise the threshold for fraudulent activities and can likely limit its impact beyond any existing scalable proof of human verification mechanism, it is important to recognize their inability to completely protect against all threats, such as collusion or other attempts to circumvent the one-person-one-proof principle (i.e. bribing others to vote a particular way). To further raise the bar, innovative ideas and research in mechanism design will be necessary.
Footnotes
-
Possibly except for the validity date ↩
-
In recent implementations virtually all major providers switched from “labeling traffic lights” to the so-called silent CAPTCHAs (e.g. reCaptcha v3) ↩
-
In this context, AI-safe refers to a process that’s hard for AI models. It’s assumed, for example, that spoofing the Orb is significantly harder for AI than performing a CAPTCHA. ↩
-
where N is the total number of previously verified users ↩
-
In the context of World ID, each holder has a unique nullifier for themselves in each application. This nullifier is what enables sybil resistance while preserving privacy as verifiers can use such nullifiers to prevent multiple registrations. ↩
-
the Orb's secure computing environment was designed to make such compromises extremely difficult ↩
Technical Implementation
The preceding sections explained the necessity for a universal, secure, and inclusive proof of human mechanism. Additionally, they discussed why iris biometrics appears to be the sole feasible path for such a proof of human mechanism. The realization via the Orb and World ID has also been explained on a high level. The subsequent section dives deeper into the specifics of the architectural design and implementation of both the Orb and World ID.
Architecture Overview
To get a World ID, an individual begins by downloading the World App. The app generates their World ID keys and guides them through the verification with an Orb. The Orb verifies humanness through the use of specialized hardware and several neural networks that run in real time on the device. Given the humanness check is successful, it generates and signs an iris code which is subsequently checked for uniqueness in the uniqueness service. If successful the public key of the World ID is added to a set of verified World IDs.
Once verified through the Orb, individuals have a verified World ID, a privacy-preserving proof-of-personhood credential. Through World ID, they can claim a set amount of WLD token every week (World Grants), where laws allow. World ID can also be used to authenticate as unique and human with other services (e.g., prevent user manipulation in the case of voting). In the future, other credentials can be issued on the World Network Protocol as well.
To make World ID and the World Network Protocol easy to use, an open source Software Development Kit (SDK) is available to simplify interactions for both Web3 and Web2 applications with World ID.

The Orb
Previous sections discussed why a custom hardware device using iris biometrics is the only approach to ensure inclusivity (i.e. everyone can sign up regardless of their location or background) and fraud resistance, promoting fairness for all participants. This section discusses the engineering details of the Orb, which was first prototyped and developed by Tools for Humanity.
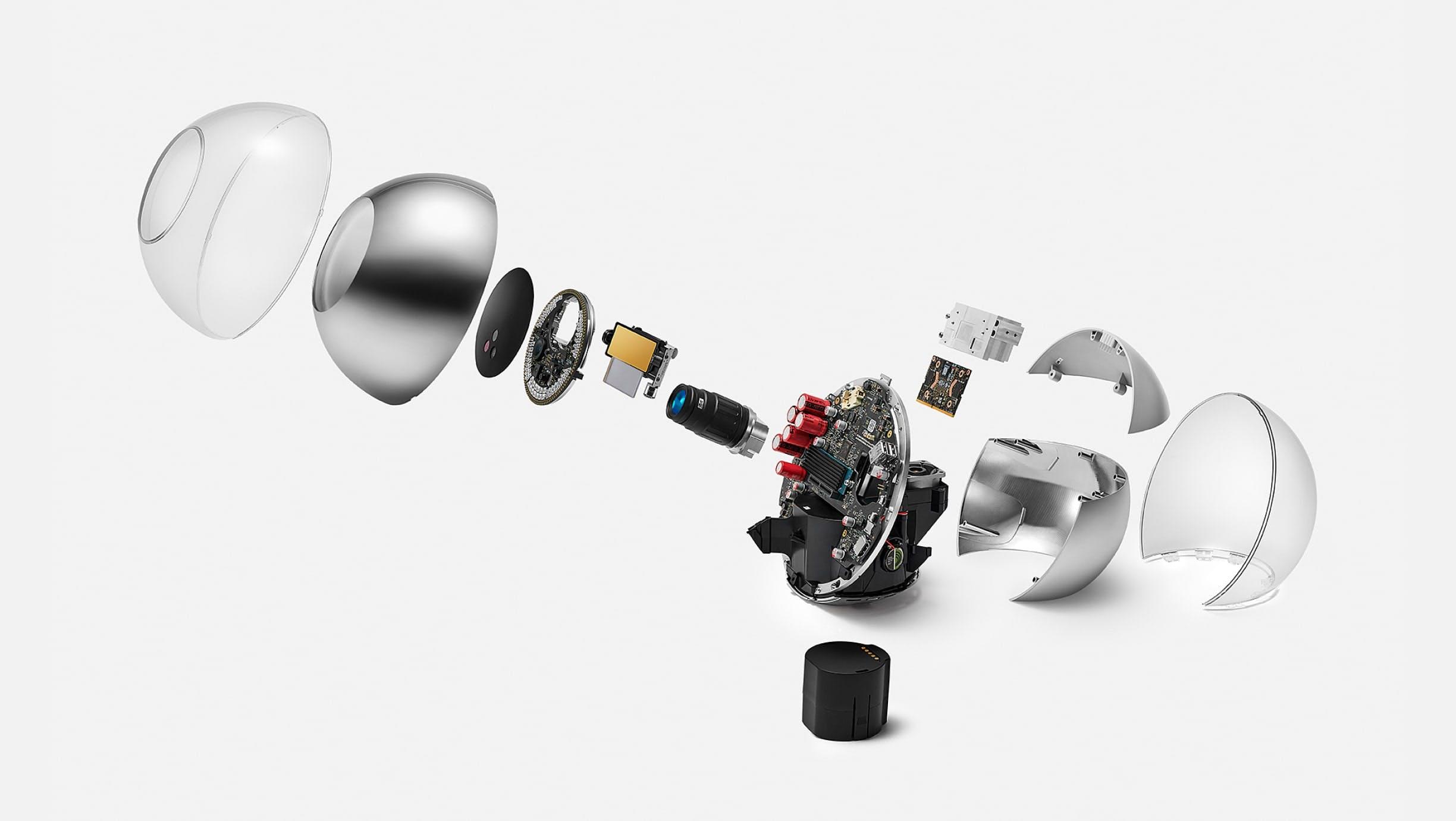
Why Custom Hardware is Needed
It would have been significantly easier to use off the shelf available devices like smartphones or iris imaging devices. However, neither is suitable for uncontrolled and adversarial environments in the presence of significant incentives. To reliably distinguish people, only iris biometrics are suitable for this globally scalable use case . To enable maximum accuracy, device integrity, spoof prevention as well as privacy, a custom device is necessary. The reasoning is described in the following section.
In terms of the biometric verification itself, the fastest and most scalable path would be to use smartphones. However, there are several key challenges with this approach. First, smartphone cameras are insufficient for iris biometrics due to their low resolution across the iris, which decreases accuracy. Further, imaging in the visible spectrum can result in specular reflections on the lens covering the iris and low reflectivity of brown eyes (most of the population) introduces noise. The Orb captures high quality iris images with more than an order of magnitude higher resolution compared to iris recognition standards. This is enabled by a custom, narrow field-of-view camera system. Importantly, images are captured in the near infrared spectrum to reduce environmental influences like different light sources and specular reflections. More details on the Orb’s imaging system can be found in the following sections.
Second, the achievable security bar is very low. For proof of human, the important part is not identification (i.e. “Is someone who they claim they are?”), but rather proving that someone has not verified yet (i.e. “Is this person already registered?”). A successful attack on a proof of human system does not necessitate the attacker’s impersonation of an existing individual, which is a challenging requirement that would be needed to unlock someone's phone. It merely requires the attacker to look different from everyone who has registered so far. Phones and existing iris cameras are missing multi-angle and multi-spectral cameras as well as active illumination to detect so-called presentation attacks (i.e. spoof attempts) with high confidence. A widely-viewed video demonstrating an effective method for spoofing Samsung’s iris recognition illustrates how straightforward such an attack could be in the absence of capable hardware.
Further, a trusted execution environment would need to be established in order to ensure that verifications originated from legitimate devices (not emulators). While some smartphones contain dedicated hardware for performing such actions (e.g., the Secure Enclave on the iPhone, or the Titan M chip on the Pixel), most smartphones worldwide do not have the hardware necessary to verify the integrity of the execution environment. Without those security features, basically no security can be provided and spoofing the image capture as well as the enrollment request is straightforward for a capable attacker. This would allow anyone to generate an arbitrary number of synthetic verifications.
Similarly, no off-the-shelf hardware for iris recognition met the requirements that were necessary for a global proof of human. The main challenge is that the device needs to operate in untrusted environments which poses very different requirements than e.g. access control or border control where the device is operated in trusted environments by trusted personnel. This significantly increases the requirements for both spoof prevention as well as hardware and software security. Most devices lack multi-angle and multispectral imaging sensors for high confidence spoof detection. Further, to enable high security spoof detection, a significant amount of local compute on the device is needed, without the ability to intercept data transmission, which is not the case for most iris scanners. A custom device enables full control over the design. This includes tamper detection that can deactivate the device upon intrusion, firmware that is designed for security to make unauthorized access very difficult, as well as the possibility to update the firmware down to the bootloader via over the air updates. All iris codes generated by an Orb are signed by a secure element to make sure they originate from a legitimately provisioned Orb, instead of, for example, an attacker’s laptop. Further, the computing unit of the Orb is capable of running multiple real-time neural networks on the five camera streams (mentioned in the last section). This processing is used for real time image capture optimization as well as spoof detection. Additionally, this enables maximum privacy by processing all images on the device such that no iris images need to be stored by the verifier.
While no hardware system interacting with the physical world can achieve perfect security, the Orb is designed to set a high bar, particularly in defending against scalable attacks. The anti-fraud measures integrated into the Orb are constantly refined. Several teams at Tools for Humanity are continuously working on increasing the accuracy and sophistication of the liveness algorithms. An internal red team is probing various attack vectors. In the near future, the red teaming will extend to external collaborators including through a bug bounty program.
Lastly, the correlation between image quality and biometric accuracy is well established, and it is expected that deep learning will benefit even more from increased image quality. Given the goal of reducing error rates as much as possible to achieve maximum inclusivity, the image quality of most devices was insufficient.
Since commercially available iris imaging devices did not meet the image quality or security needs, Tools for Humanity dedicated several years to developing a custom biometric verification device (the Orb) to enable universal access to the global economy in the most inclusive manner possible.
Hardware
Three years of R&D, including one year of small-scale field testing and one year of transition to manufacturing at scale, have led to the current version of the Orb, which is being open sourced. Feedback for design improvements is welcome and highly encouraged. The remainder of this section will go through a teardown of the Orb, with a few engineering anecdotes included.
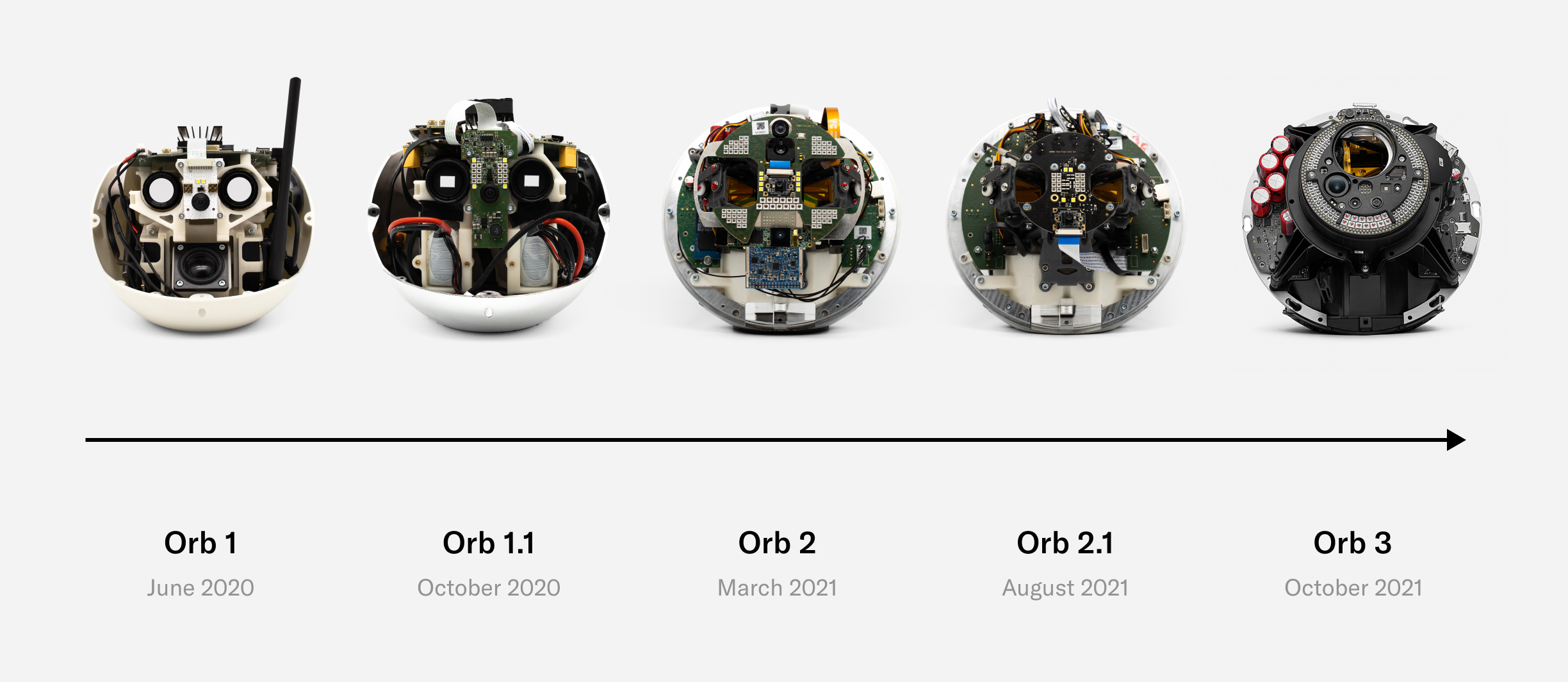
Today’s Orb represents a precise balance of development speed, compactness, user experience, cost and at-scale production with minimal compromise being made on imaging quality and security. There will likely be future versions that are optimized even further both by Tools for Humanity and other companies as the World ecosystem decentralizes. However, the current version represents a key milestone that enables scaling the World.
The following takes the reader through some of the most important engineering details of the Orb, as well as how the imaging system works. For security purposes, only tamper detection mechanisms that are meant to catch intrusion attempts are left out.
Design
Fundamental to the development of the Orb was its design. A spherical shape is an engineering challenge. However, it was important for the design of the Orb to reflect the values of World. The spherical shape stands for Earth, which is home to all. Similarly the Orb is tilted at 23.5 degrees, the same degree at which the Earth is tilted relative to its orbital plane around the sun. There’s even a 2mm thick clear shell on the outside of the Orb which protects the Orb just like the atmosphere protects Earth. The resemblance of Earth symbolizes that World is meant to give everyone the opportunity to participate, regardless of their background and the Orb and its use of biometrics is a reflection of that since nothing is required other than being human.

Mechanics
When removing the shell, the mainboard, optical system and cooling system become visible. Most of the optical system is hidden in an enclosure that, together with the shell, forms a dust- and water-resistant environment to enable long-term use even in challenging environments.
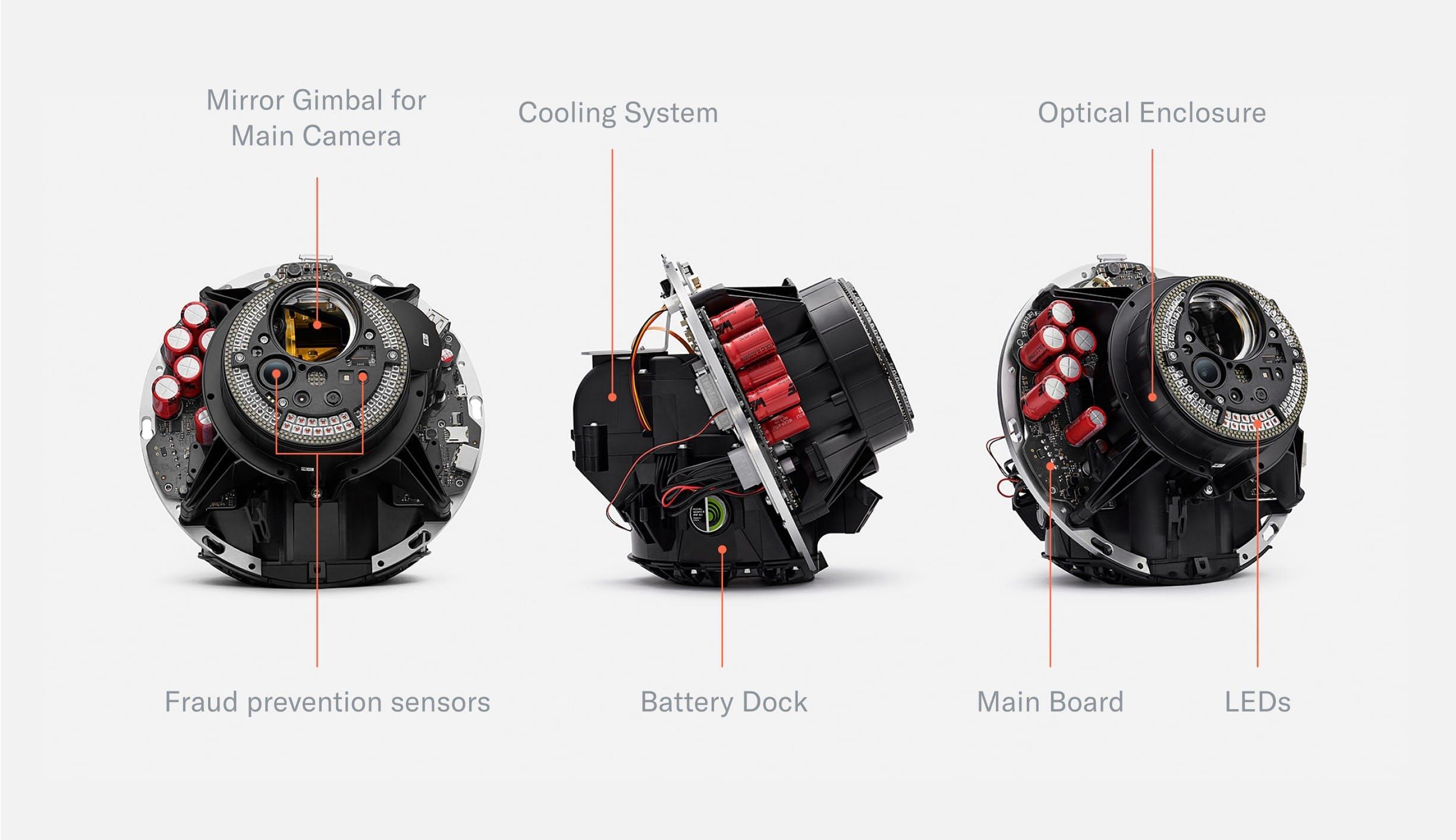
The Orb consists of two hemispheres separated by the mainboard which is tilted at 23.5°—the angle of the rotational axis of the earth. The mainboard holds a powerful computing unit to enable local processing for maximum privacy. The frontal half of the Orb is dedicated to the sealed optical system. The optical system consists of several multispectral sensors to verify liveness and a 2D gimbal-enabled narrow field of view camera to capture high resolution iris images. The other hemisphere is dedicated to the cooling system as well as speakers. An exchangeable battery can be inserted from the bottom to enable uninterrupted operation in a mobile setting.
Once the shell is removed, the Orb can be divided into four core parts:
- Front: The optical system
- Middle: The mainboard separates the device into two hemispheres
- Back: The main computing unit as well as the active cooling system
- Bottom: An exchangeable battery
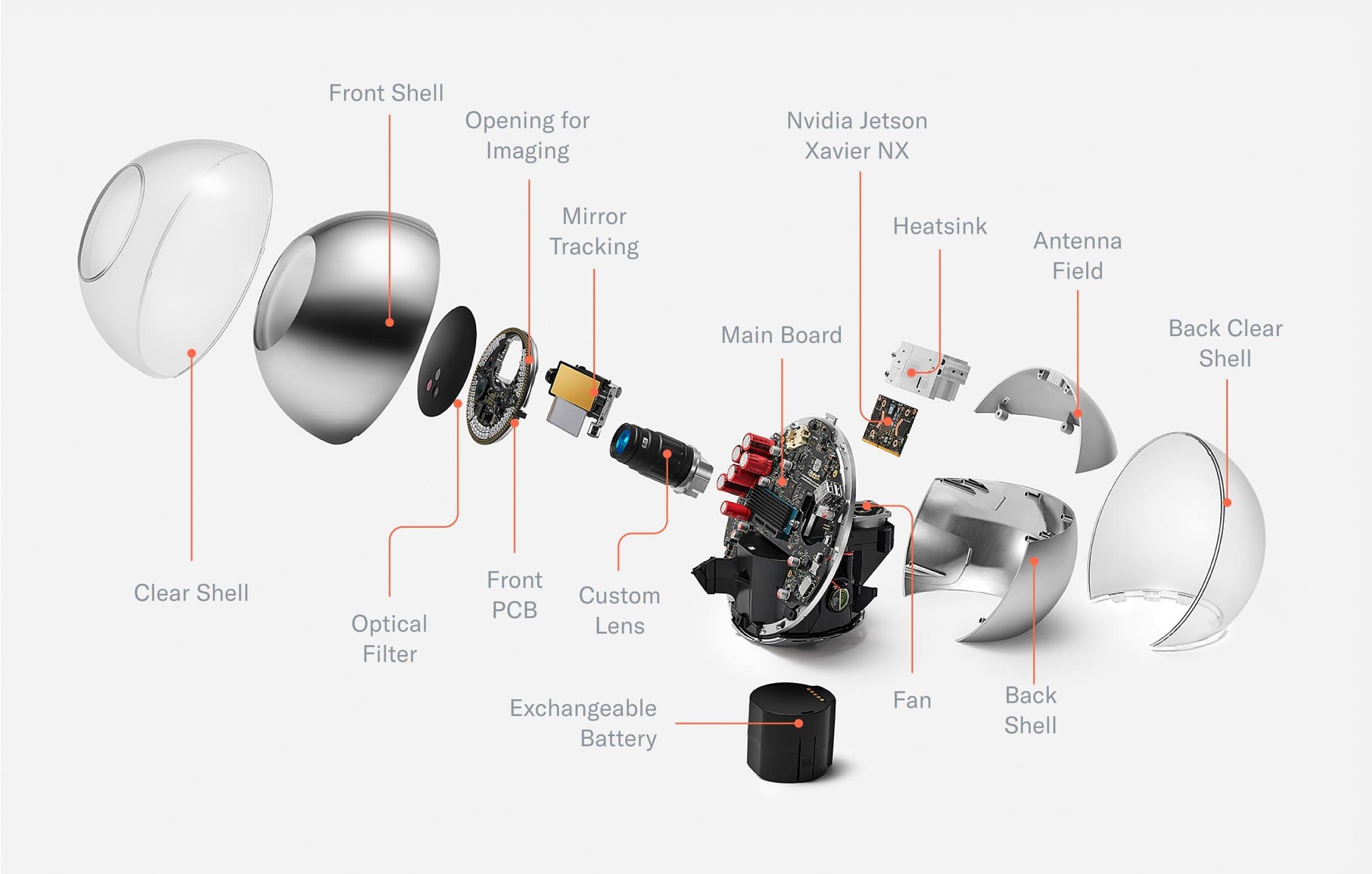
With the housing material removed (e.g. the dust-proof enclosure of the optical system), all relevant components of the Orb become visible. This includes the custom lens, which is optimized for both near infrared imaging and fast, durable autofocus. The front of the optical system is sealed by an optical filter to keep dust out and minimize noise from the visible spectrum to optimize image quality. In the back, a plastic component in the otherwise chrome shell allows for optimized antenna placement. The chrome shell is covered by a clear shell to avoid deterioration of the coating over time.
First prototypes were tested outside the lab as early as possible. Naturally, this taught the team many lessons, including:
Optical System
With the first prototype, the signup experience was notoriously difficult. Over the course of a year the optical system was upgraded with autofocus and eye tracking such that alignment becomes trivial when the person is within an arm's length of the Orb.
Battery
No off-the-shelf battery would last for a full day on a single charge. A custom exchangeable battery was designed based on 18650 Li-Ion cells—the same form factor as the cells used in modern electric cars. The battery consists of 8 cells with 3.7V nominal voltage in a 4S2P configuration (14.8V) with a capacity of close to 100Wh, which is a limit imposed by regulations related to logistics. Now there’s no limit to Orb uptime.

The Orb’s custom battery is made of Li-Ion 18650 cells (the same cells used in many electric cars). With close to 100Wh, the capacity is optimized for battery lifetime while complying with transportation regulations. A USB-C connector makes recharging convenient.
Shell
The coating of the shell sometimes deteriorated in the handheld use case. Therefore, a 2mm clear shell was added to both optimize the design as well as protect the chrome coating from scratches and other wear.
UX LEDs
To make the user experience more intuitive, especially in loud environments where a person might not be able to hear sound feedback, an LED ring was added to help guide people through the sign-up process. Similarly, status LEDs were exposed next to the only button on the Orb to indicate its current state.
Optical System
Early field tests showed that the verification experience needed to be even simpler than anticipated. To do this, the team first experimented with many approaches featuring mirrors that allowed people to use their reflection to align with the Orbs imaging system. However, designs that worked well in the lab quickly broke down in the real world. The team ended up building a two-camera system featuring a wide angle camera and a telephoto camera with an adjustable ~5° field of view by means of a 2D gimbal. This increased the spatial volume in which a signup can be successfully completed by several orders of magnitude, from a tiny box of 20x10x5mm for each eye to a large cone.
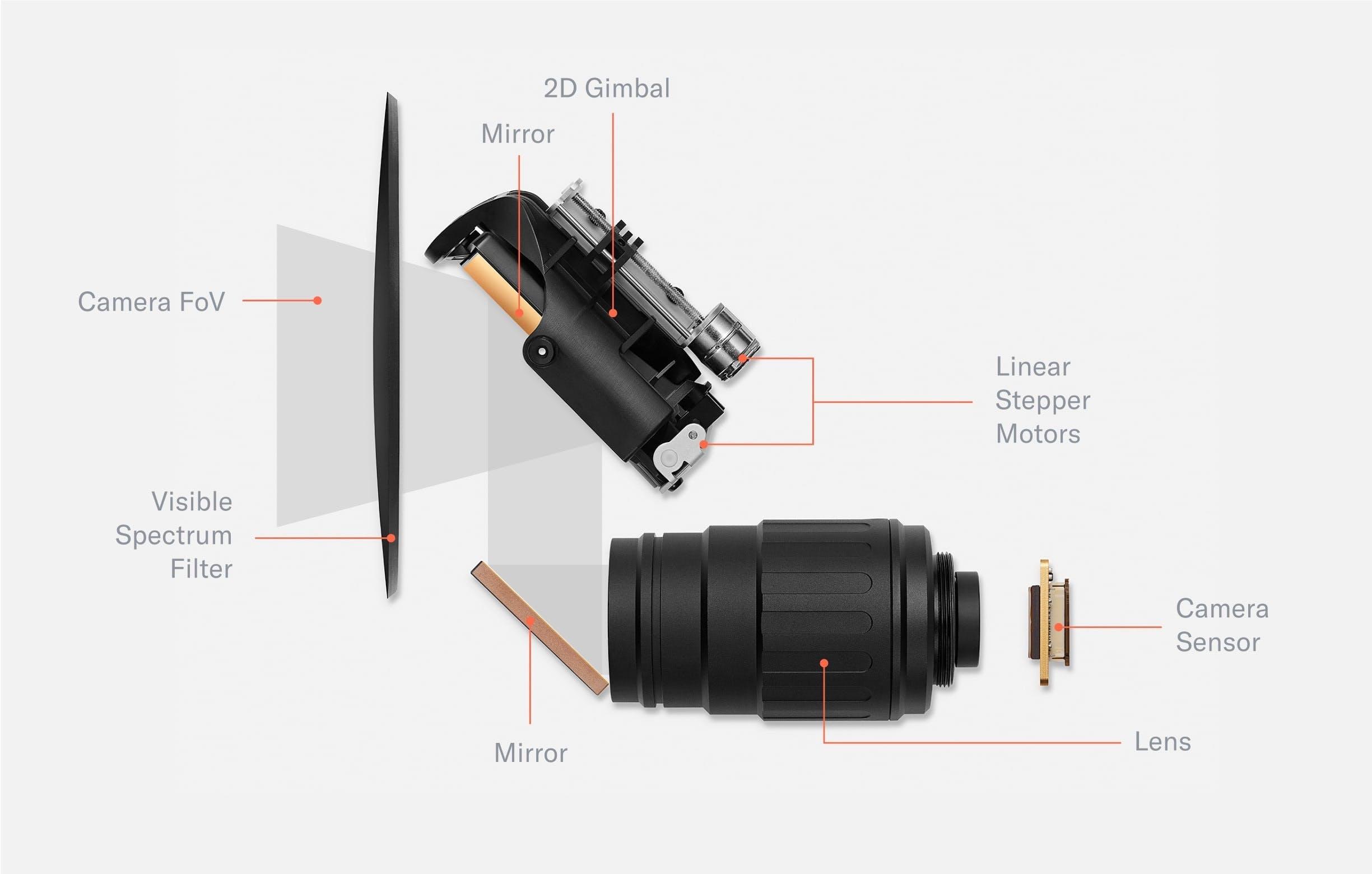
The main imaging system of the Orb consists of a telephoto lens and 2D gimbal mirror system, a global shutter camera sensor and an optical filter. The movable mirror increases the field of view of the camera system by more than two orders of magnitude. The optical unit is sealed by a black, visible spectrum filter which seals the high precision optics from dust and only transmits near infrared light. The image capture process is controlled by several neural networks.
The wide angle camera captures the scene, and a neural network predicts the location of both eyes. Through geometrical inference, the field of view of the telephoto camera is steered to the location of an eye to capture a high resolution image of the iris, which is further processed by the Orb into an iris code.
Beyond simplicity, the image quality was the main focus. The correlation between image quality and biometric accuracy is well established.
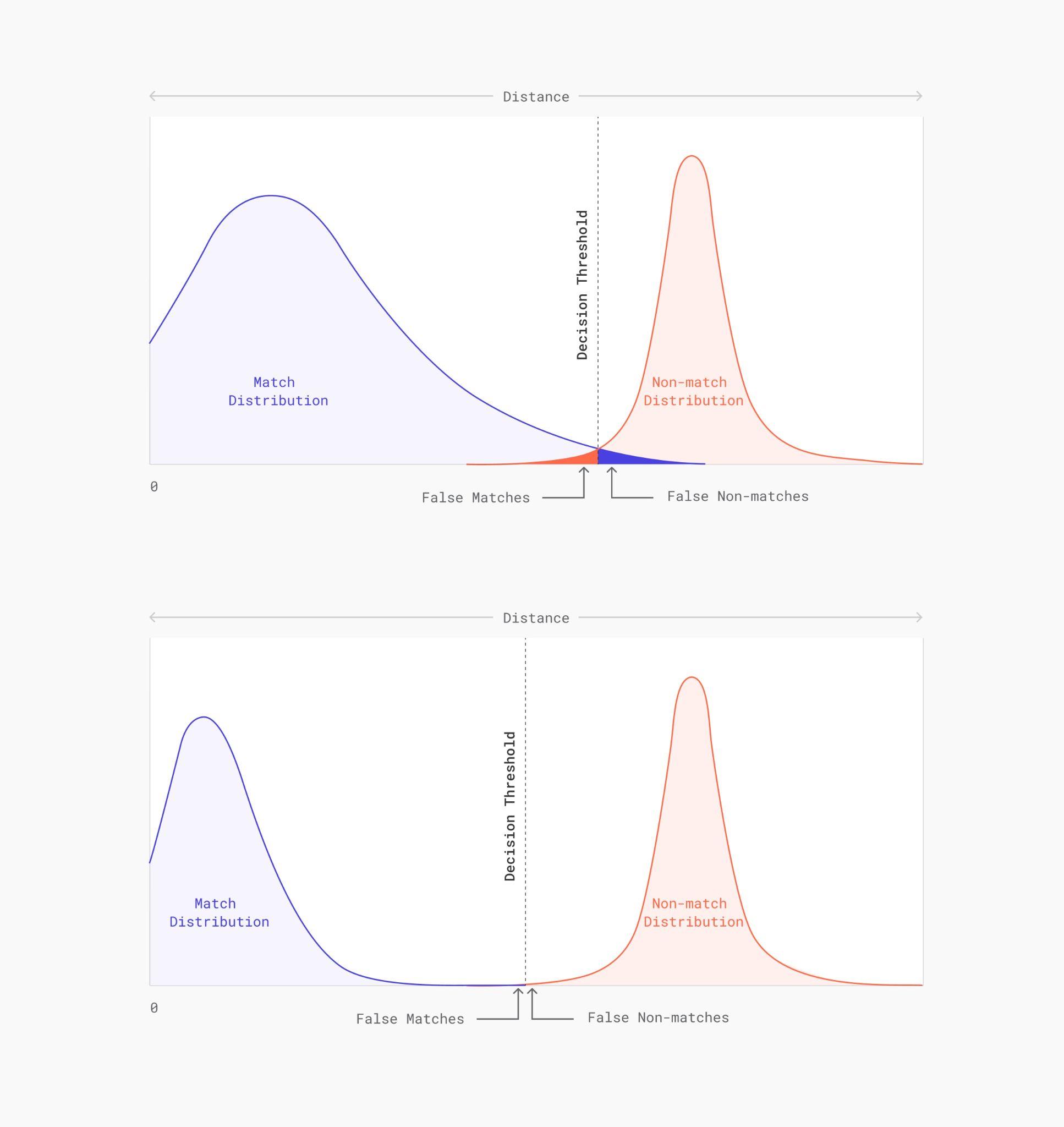
Here pairwise comparisons are plotted: the match distribution for pairs of the same identity (blue) and non-match distribution for pairs of different identity (red). In a perfect system, the match-distribution would be a very narrow peak at zero. However, multiple sources of error widen the distribution, leading to more overlap with the non-match distribution and therefore increasing False Match and False Non-Match rates. High quality image acquisition narrows the match-distribution significantly and therefore minimizes errors. The width of the non-match distribution is determined by the amount of information that is captured by the biometric algorithm: the more information is encoded in the embeddings the narrower the distribution.
Many off-the-shelf products have been tested but there wasn’t any lens compact enough to meet the imaging requirements while still being affordable. Therefore, the team partnered with a well known specialist in the machine vision industry to build a customized lens. The lens is optimized for the near infrared spectrum and has an integrated custom liquid lens which allows for neural network controlled millisecond-autofocus. It is paired with a global shutter sensor to capture high resolution, distortion free images.

Fig. 3.10:
a) Custom telephoto lens. The telephoto lens was custom designed for the Orb. The glass is coated to optimize image capture in the near infrared spectrum. An integrated liquid lens allows for durable millisecond autofocus. The position of the liquid lens is controlled by a neural network to optimize focus. To capture images free of motion blur, the global shutter sensor is synchronized with pulsed illumination.
b) A comparison of the image quality of the World Network Orb vs. the industry standard clearly show the advancements made in the space. The camera and the corresponding pulsed infrared illumination are synchronized to minimize motion blur and suppress the influence of sunlight. This way, the Orb creates lab environment conditions for imaging, no matter its location. Needless to say, the infrared illumination is compliant with eye safe standards (such as EN 62471:2008).
Image quality was the one thing never compromised no matter how difficult it was. In terms of resolution the Orb is orders of magnitude above the industry standard. This provides the basis for the lowest error rates possible to, in turn, maximize the inclusivity of the system.
Electronics
When disassembling the Orb further, several PCBs (Printed Circuit Boards) are visible, including the front PCB containing all illumination, the security PCB for intrusion detection and the bridge PCB which connects the front PCB with the largest PCB: the mainboard.
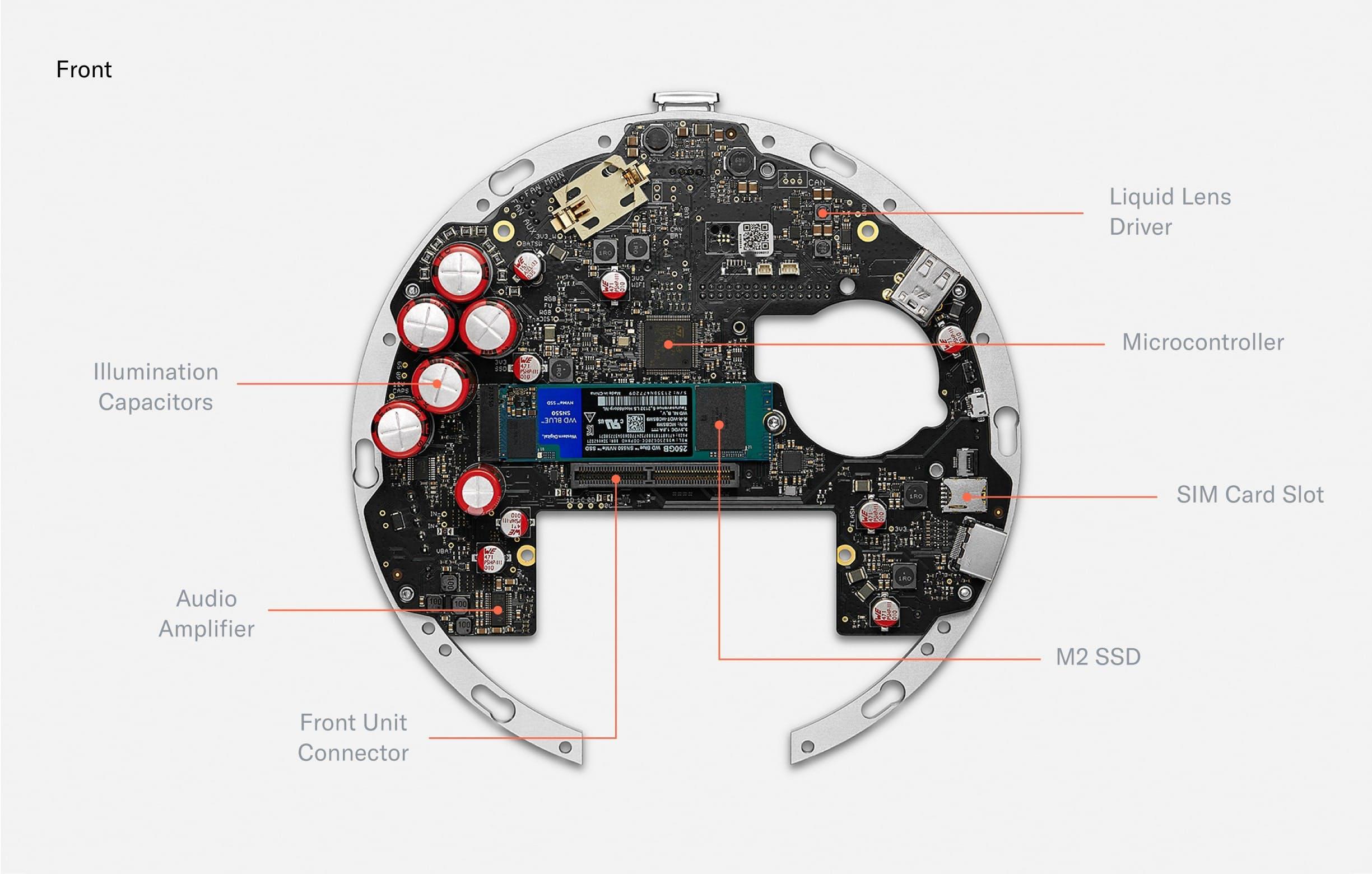
The front of the mainboard holds capacitors to power the pulsed, near infrared illumination (certified eye safe). There are also drivers to power the deformation of the liquid lens in the optical system. A microcontroller controls precise timing of the peripherals. An encrypted M.2 SSD can be used to store images for voluntary data custody and image data collection. Those images are secured by a second layer of asymmetric encryption such that the Orb can only encrypt, but cannot decrypt. The contribution of data is optional and data deletion can be requested at any point in time through the World App. A SIM card slot enables optional LTE connectivity.
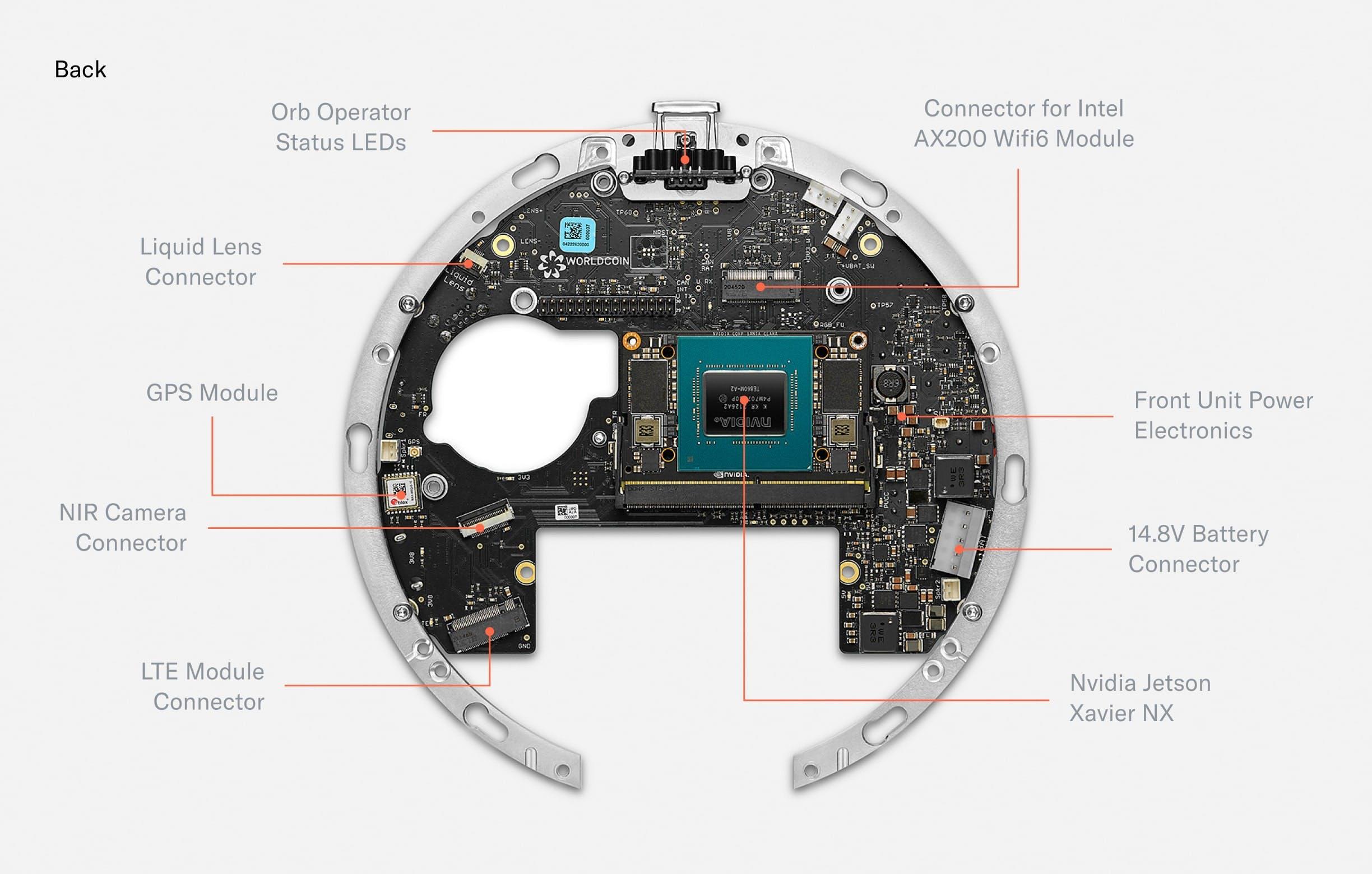
Fig. 3.
The back of the mainboard holds several connectors for active elements of the optical system. Additionally, a GPS module enables precise location of Orbs for fraud prevention purposes. A Wi-Fi Module equips the Orb with the possibility to upload iris codes to make sure every person can only sign up once. Finally, the mainboard hosts a Nvidia Jetson Xavier NX which runs multiple neural networks in real time to optimize image capture, perform local anti-spoof detection and calculate the iris code locally to maximize privacy.
The mainboard acts as a custom carrier board for the Nvidia Jetson Xavier NX SoM which is the main computing unit powering the Orb. The Jetson is capable of running multiple neural networks on several camera streams in real-time to optimize image capture (autofocus, gimbal positioning, illumination, quality checks i.e. “is_eye_open”) and perform spoof detection. To optimize for privacy, images are fully processed on the device, and are only stored by Tools for Humanity if the user gives explicit consent to help improve the system.
Apart from the Jetson, the other major “plugged-in” component is a 250GB M.2 SSD. The encrypted SSD can be used to buffer images for voluntary data contribution. Images are protected by a second layer of asymmetric encryption such that the Orb can only encrypt, but cannot decrypt. The contribution of data is optional and data deletion can be requested at any point in time through the app.
Further, a STM32 microcontroller controls time-critical peripherals, sequences power, and boots the Jetson. The Orb is equipped with Wi-Fi 6 and a GPS module to locate the Orb and prevent misuse. Finally, a 12 bit liquid lens driver allows for controlling the focus plane of the telephoto lens with a precision of 0.4mm.
The most densely packed PCB of the Orb is the front PCB. It mainly consists of LEDs. The outermost RGB LEDs power the “UX LED ring.” Further inside, there are 79 near infrared LEDs of different wavelengths. The Orb uses 740nm, 850nm and 940nm LEDs to capture a multispectral image of the iris to make the uniqueness algorithm more accurate and detect spoofing attempts.
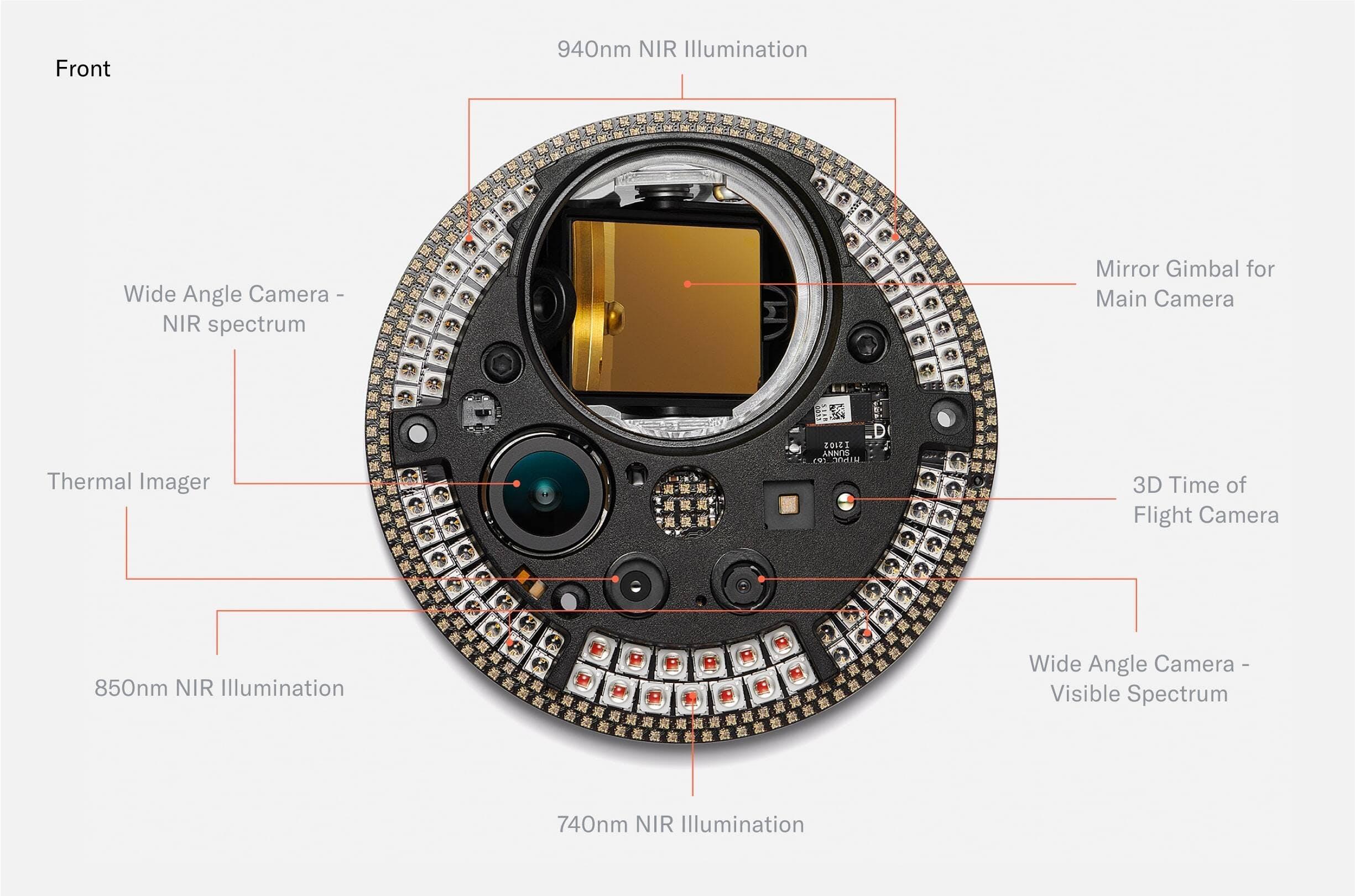
The front PCB also hosts several multispectral imaging sensors. The most basic one is the wide angle camera, which is used for steering the telephoto iris camera. Since every human can only receive one proof of human and World is giving away a free Worldcoin token to every person who chooses to verify with the Orb, the incentives for fraud are high. Therefore, further imaging sensors for fraud prevention purposes were added.
When designing the fraud prevention system, the team started from first principle reasoning: which measurable features do humans have? From there, the team experimented with many different sensors and eventually converged to a set that includes a near infrared wide angle camera, a 3D time of flight camera and a thermal camera. Importantly, the system was designed to enable maximum privacy. The computing unit of the Orb is capable of running several AI algorithms in real time which distinguish spoofing attempts from genuine humans based on the input from those sensors locally. No images are stored unless users give explicit consent to help improve the system for everyone.
Biometrics
Following the exploration of iris biometrics as a choice of modality, this section provides a detailed look into the process of iris recognition from image capture to the uniqueness check:
- Biometric Performance at a Billion People Scale, addresses the scalability of iris recognition technology. It discusses the potential of this biometric modality to establish uniqueness among billions of humans, examines various operating modes and anticipated error rates and ultimately concludes the feasibility of using iris recognition at a global scale.
- Iris Feature Generation with Gabor Wavelets introduces the use of Gabor filtering for generating unique iris features, explaining the scientific principles behind this traditional method which is fundamental to understanding how iris recognition works.
- Iris Inference System explores the practical application of the previously discussed principles. This section describes the uniqueness algorithm and explains how it processes iris images to ensure accurate and scalable verification of uniqueness. This provides a comprehensive overview of the system's operation, demonstrating how theoretical principles translate into practical application.
Collectively, these sections offer a holistic overview of iris recognition, from the core scientific principles to their practical application in the Orb.
Biometric performance at a billion people scale
In order to get a rough estimation on the required performance and accuracy of a biometric algorithm operating on a billion people scale, assume a scenario with a fixed biometric model, i.e. it is never updated such that its performance values stay constant.
Failure Cases
A biometric algorithm can fail in two ways: It can either identify a person as a different person, which is called a false match or it can fail to re-identify a person although this person is already enrolled, which is called a false non match. The corresponding rates - the false match rate (FMR) and the false non match rate (FNMR) - are the two critical KPIs for any biometric system.
For the purposes of this analysis, consider three different systems with varying levels of performance.
- One of the systems, as reported by John Daugman in his paper, demonstrates a false match rate of at a false non-match rate of 0.00014.
- Another system, represented by one of the leading iris recognition algorithms from NEC, has performance values as reported in the IREX IX report and IREX X leaderboard from the National Institute for Standards and Technology (NIST). These values include a false match rate of at a false non-match rate of 0.045.
- The third system, conceived during the early ideation stage of World, represents a conservative estimate of how well iris recognition could perform outside of the lab environment i.e. in an uncontrolled, outdoor setting. Despite these constraints, it anticipated a false match rate of and a false non-match rate of 0.005. While not ideal, it demonstrated that iris recognition was the most viable path for a global proof of human.
A more in-depth examination of how these values are obtained from various sources is also available.
Effective Dual Eye Performance
The values mentioned above pertain to single eye performance, which is determined by evaluating a collection of genuine and imposter iris pairs. However, utilizing both eyes can significantly enhance the performance of a biometric system. There are various methods for combining information from both eyes, and to evaluate their performance, consider two extreme cases:
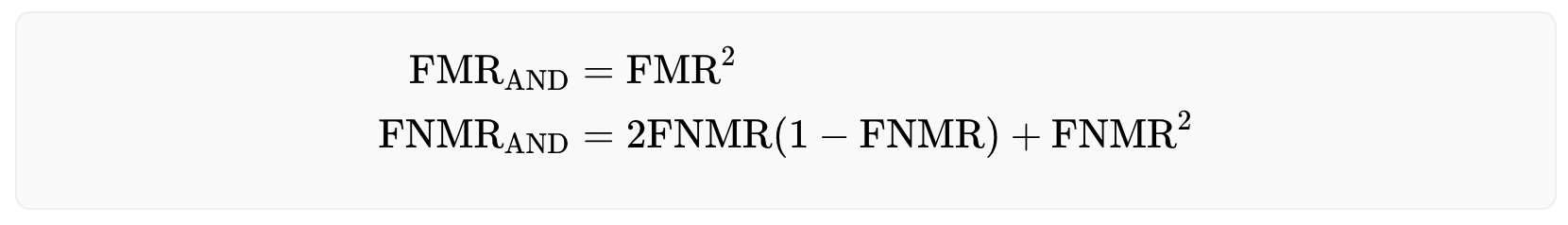
- The AND-rule, in which a user is deemed to match only if their irises match on both eyes.
- The OR-rule, in which a user is considered a match if their iris on one eye matches that of another user's iris on the same eye.
The OR-rule offers a safer approach as it requires only a single iris match to identify a registered user, thus minimizing the risk of falsely accepting the same person twice. Formally, the OR-rule reduces the false non-match rate while increasing the false match rate. However, as the number of registered users increases over time, this strategy may make it increasingly difficult for legitimate users to enroll to the system due to the high false match rate. The effective rates are given below:
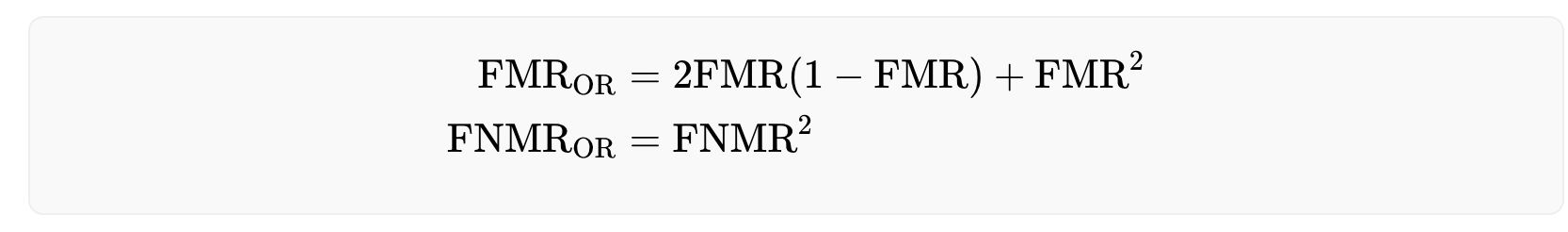
On the other hand, the AND-rule allows for a larger user base, but comes at the cost of less security, as the false match rate decreases and the false non-match rate increases. The performance rates for this approach are as follows:
False Matches
The probability for the i-th (legitimate) user to run into a false match error can be calculated by the equation

with being the false match rate. Adding up these numbers yields the expected number of false matches that have happened after the i-th user has enrolled, i.e the number of falsely rejected users (derivation).
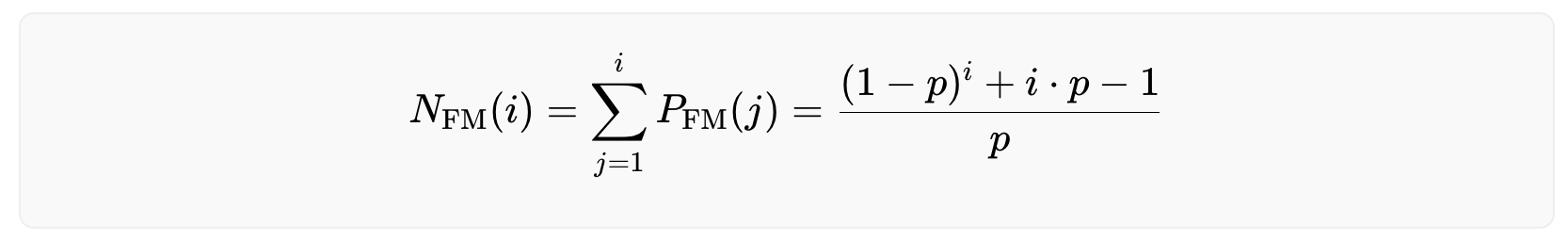
A high false match rate significantly impacts the usability of the system, as the probability of false matches increases with a growing number of users in the database. Over time the probability of being (falsely) rejected as a new user converges to 100%, making it nearly impossible for new users to be accepted.
The following graph illustrates the performance of the biometric system using both the OR and AND rule. The graph is separated into two sections, with the left side representing the OR rule and the right side representing the AND rule. The top row of plots in the graph shows the probability of the i-th user being falsely rejected, and the bottom row of plots shows the expected number of users that have been falsely rejected after the i-th user has successfully enrolled. The different colors in the graph correspond to the three systems mentioned earlier: green represents Daugman’s system, blue represents NEC’s system, and red represents the initial worst case estimate.
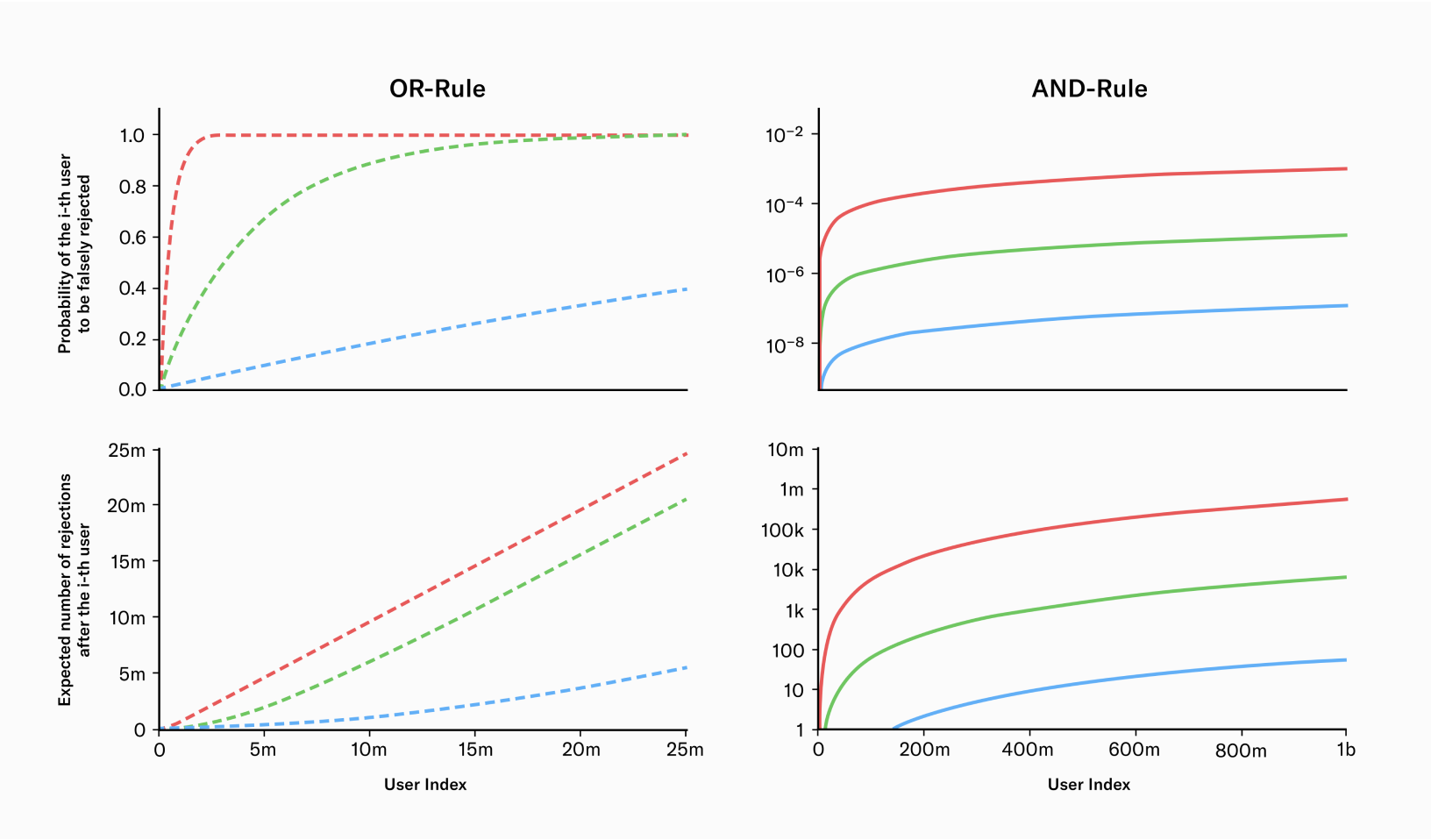
The main findings from the analysis indicate that when using the OR-rule, the system's effectiveness breaks down with just a few million users, as the chance of a new user being falsely rejected becomes increasingly likely. In comparison, operating with the AND-rule provides a more sustainable solution for a growing user base.
Further, even the difference between the worst case and the best case estimate of current technology matters. The performance of biometric algorithms designed by Tools for Humanity has been continuously improving due to ongoing research efforts. This has been achieved by pushing beyond the state-of-the-art by replacing various components of the uniqueness verification process with deep learning models which also significantly improves the robustness to real world edge cases. At the time of writing, the algorithm's performance closely resembled the green graph depicted in the figure above when in an uncontrolled environment (depending on the exact choice of the FNMR). This is an accomplishment noteworthy in and of itself. Nonetheless, further improvements in the algorithm's performance are expected through ongoing research efforts. The optimum case is a vanishing error rate in practice on a global scale.
Note that for a large number of users (i≫1) and a very performant biometric system (p≪1) the equation above becomes numerically unstable. To calculate the number of rejected users for such a scenario, Taylor expand the critical part of the equation around small values of p.
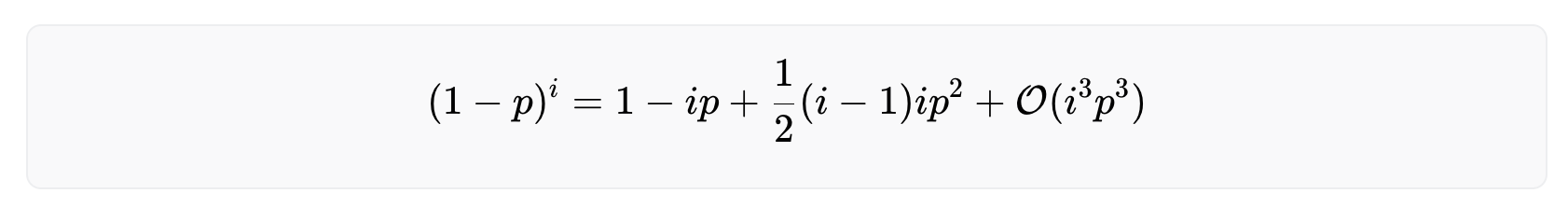
The derivation of the above equation can be found here. Inserting this in the equation above yields
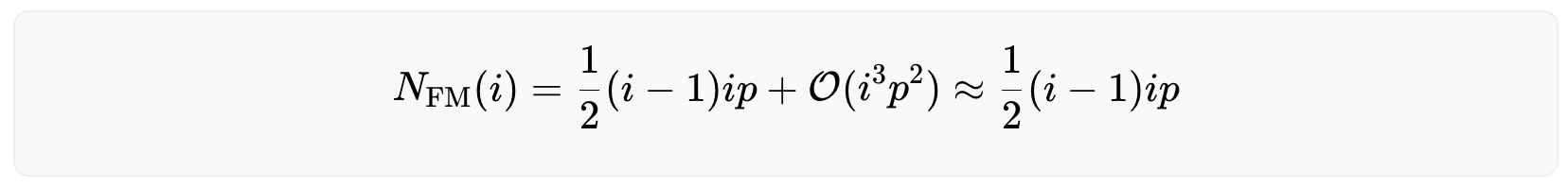
which is a valid approximation as long as
False Non Matches
When it comes to fraudulent users, the probability of them not being matched stays constant and does not increase with the number of users in the system. This is because there is only one other iris that can cause a false non-match - the user's own iris from their previous enrollment. Thus, the probability of encountering a false non-match is given by
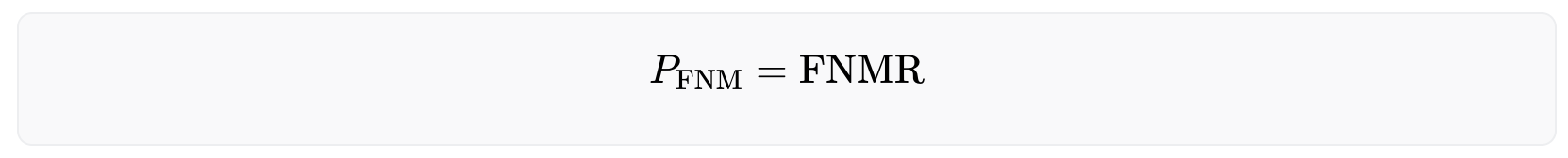
The number of expected false non matches can be calculated with
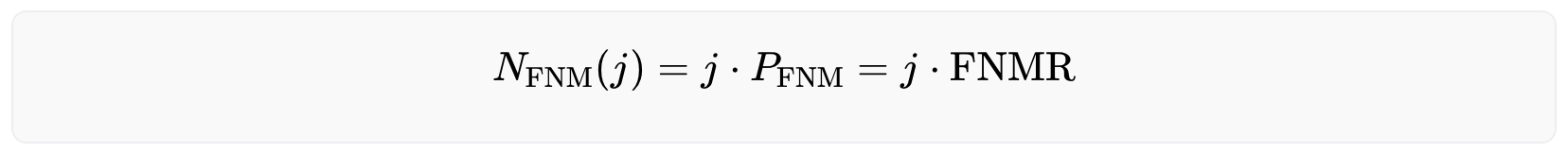
with j indicating the j-th untrustworthy user who tries to fool the system.
Conclusion
The conclusion is that iris recognition can establish uniqueness on a global scale. Further, to onboard billions of individuals, the algorithm needs to use the AND-rule. Otherwise, the rejection rate will be too high and it will be practically impossible to onboard billions of users.
The current performance is already beyond the original conservative estimate and the project expects the system to eventually surpass current state-of-the-art lab environment performance, even if subject to an uncontrolled environment: On the one hand, the custom hardware comprises an imaging system that outperforms typical iris scanners by more than an order of magnitude in terms of image resolution. On the other hand, current advances in deep learning and computer vision offer promising directions towards a “deep feature generator” - a feature generation algorithm that does not rely on handcrafted rules but learns from data. So far the field of iris recognition has not yet leveraged this new technology.
Iris Feature Generation with Gabor Wavelets
The objective for iris feature generation algorithms is to generate the most discriminative features from iris images while reducing the dimensionality of data by removing unrelated or redundant data. Unlike 2D face images that are mostly defined by edges and shapes, iris images present rich and complex texture with repeating (semi-periodic) patterns of local variations in image intensity. In other words, iris images contain strong signals in both spatial and frequency domains and should be analyzed in both. Examples of iris images can be found on John Daugman's website.
Gabor filtering
Research has shown that the localized frequency and orientation representation of Gabor filters is very similar to the human visual cortex’s representation and discrimination of texture. A Gabor filter analyzes a specific frequency content at a specific direction in a local region of an image. It has been widely used in signal and image processing for its optimal joint compactness in spatial and frequency domain.
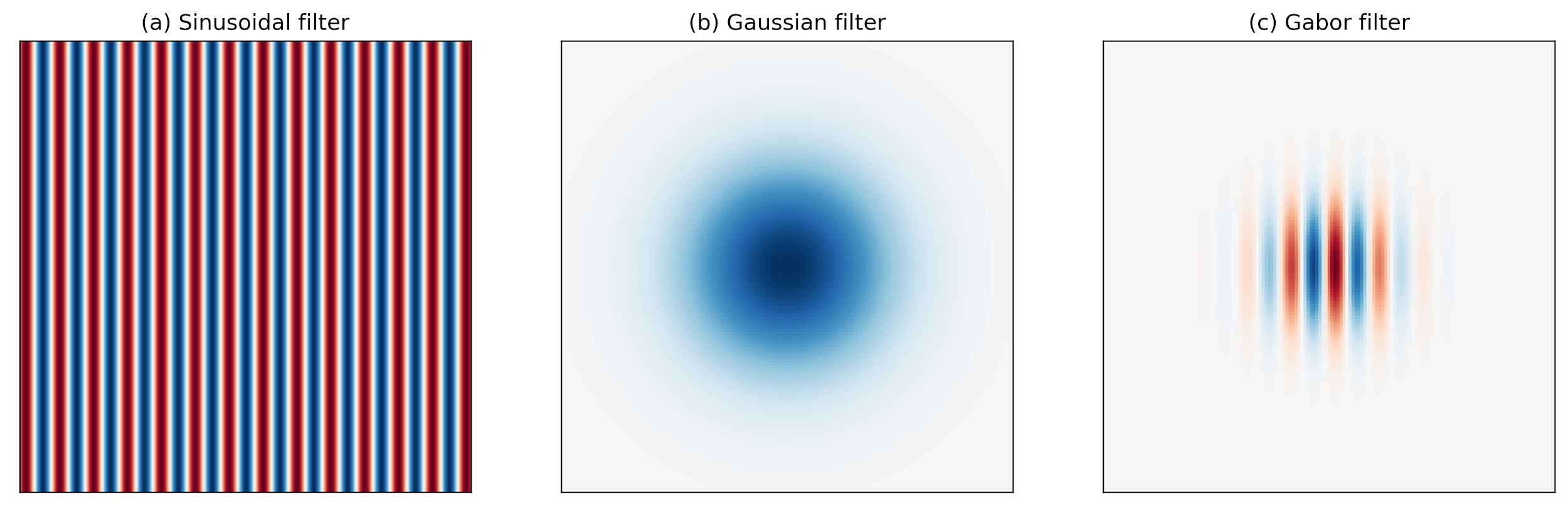
As shown above, a Gabor filter can be viewed as a sinusoidal signal of particular frequency and orientation modulated by a Gaussian wave. Mathematically, it can be defined as
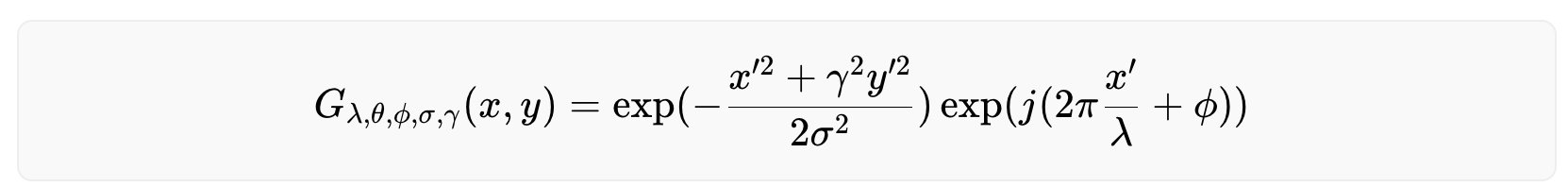
with
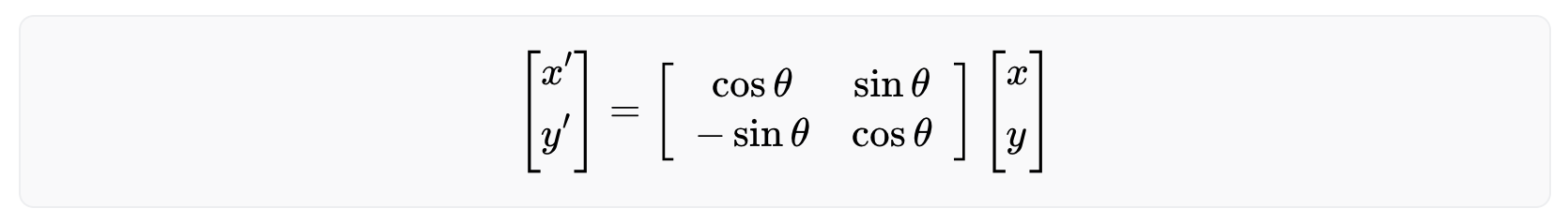
Among the parameters, σ and γ represent the standard deviation and the spatial aspect ratio of the Gaussian envelope, respectively, λ and ϕ are the wavelength and phase offset of the sinusoidal factor, respectively, and θ is the orientation of the Gabor function. Depending on its tuning, a Gabor filter can resolve pixel dependencies best described by narrow spectral bands. At the same time, its spatial compactness accommodates spatial irregularities.
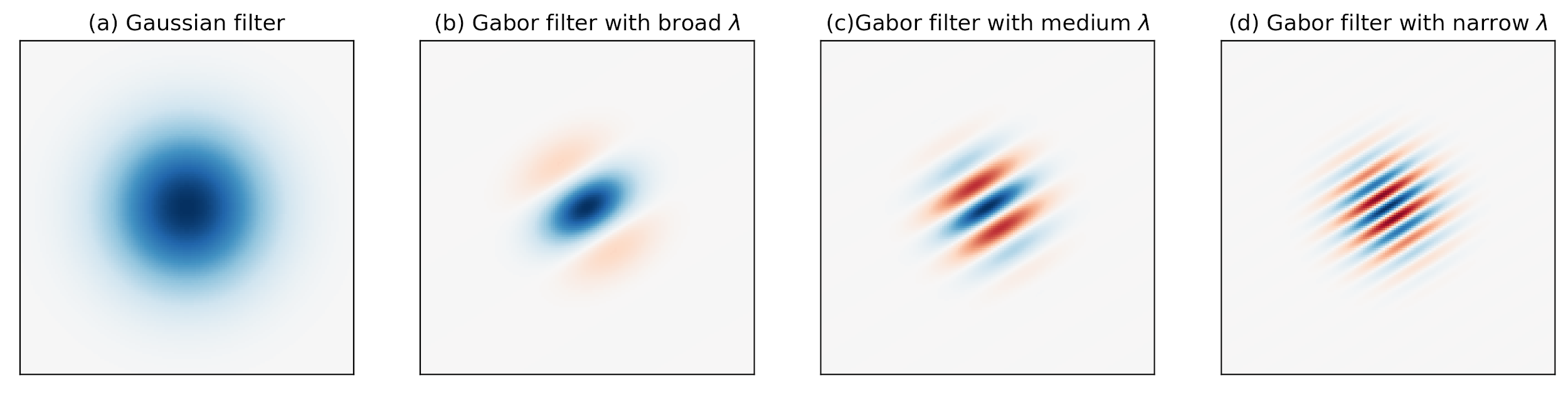
The following figure shows a series of Gabor filters at a 45 degree angle in increasing spectral selectivity. While the leftmost Gabor wavelet resembles a Gaussian, the rightmost Gabor wavelet follows a harmonic function and selects a very narrow band from the spectrum. Best for iris feature generation are the ones in the middle between the two extremes.
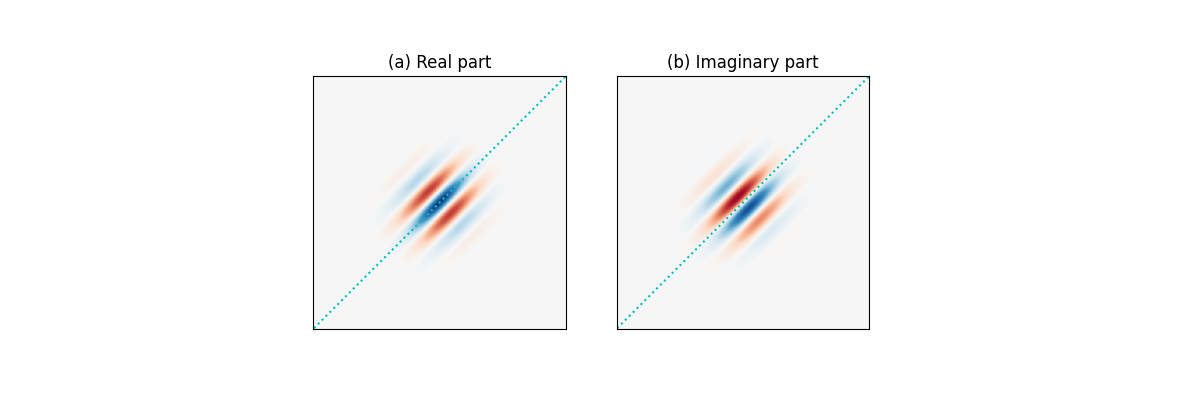
Because a Gabor filter is a complex filter, the real and imaginary parts act as two filters in quadrature. More specifically, as shown in the figures below, (a) the real part is even-symmetric and will give a strong response to features such as lines; while (b) the imaginary part is odd-symmetric and will give a strong response to features such as edges. It is important to maintain a zero DC component in the even-symmetric filter (the odd-symmetric filter already has zero DC). This ensures zero filter response on a constant region of an image regardless of the image intensity.
Multi-scale Gabor filtering
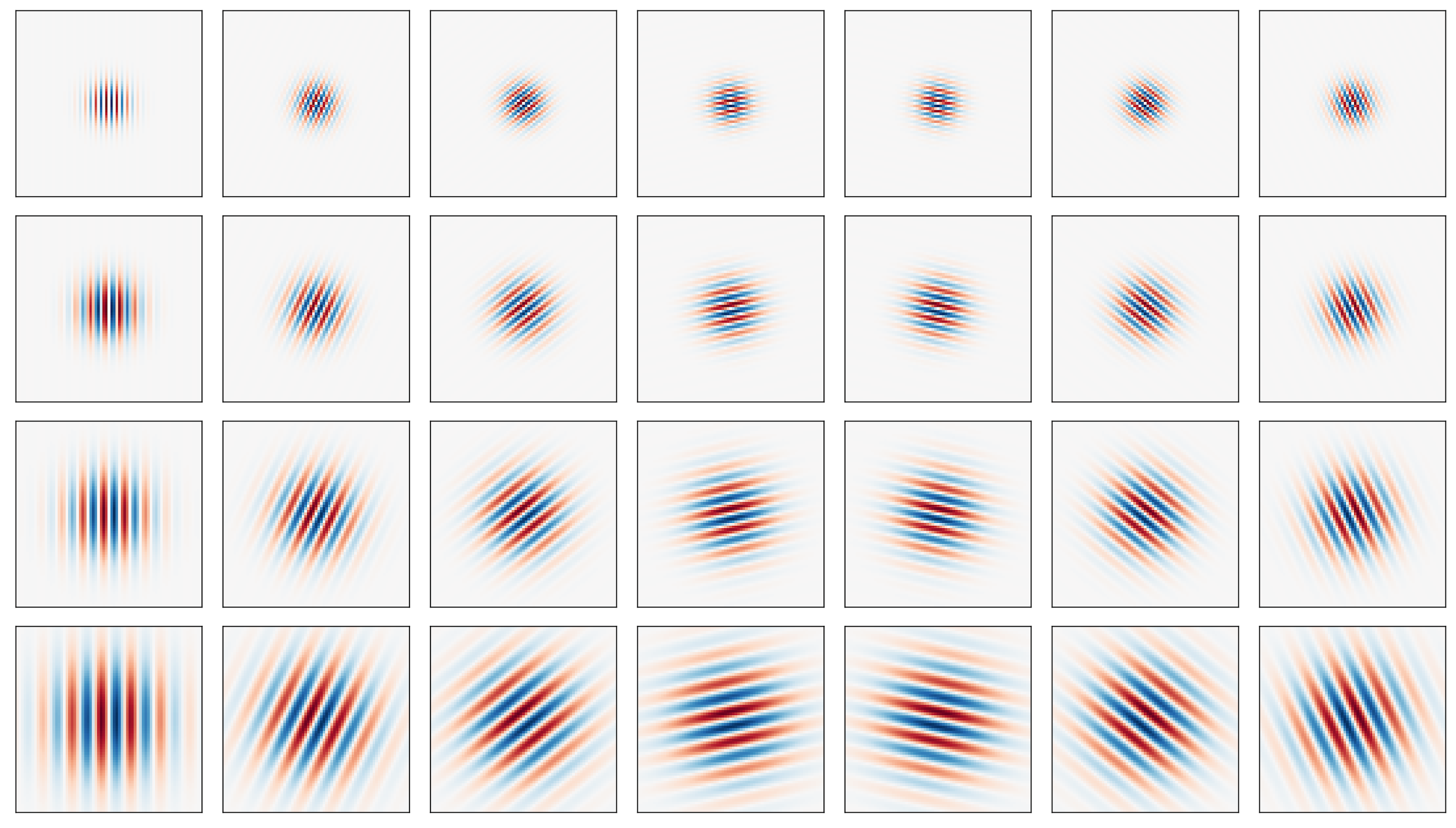
Like most textures, iris texture lives on multiple scales (controlled by ). It is therefore natural to represent it using filters of multiple sizes. Many such multi-scale filter systems follow the wavelet building principle, that is, the kernels (filters) in each layer are scaled versions of the kernels in the previous layer, and, in turn, scaled versions of a mother wavelet. This eliminates redundancy and leads to a more compact representation. Gabor wavelets can further be tuned by orientations, specified by . The figure below shows the real part of 28 Gabor wavelets with four scales and 7 orientations.
Phase-quadrant demodulation and encoding
After a Gabor filter is applied to an iris image, the filter response at each analyzed region is then demodulated to generate its phase information. This process is illustrated in the figure below, as it identifies in which quadrant of the complex plane each filter response is projected to. Note that only phase information is recorded because it is more robust than the magnitude, which can be contaminated by extraneous factors such as illumination, imaging contrast, and camera gain.
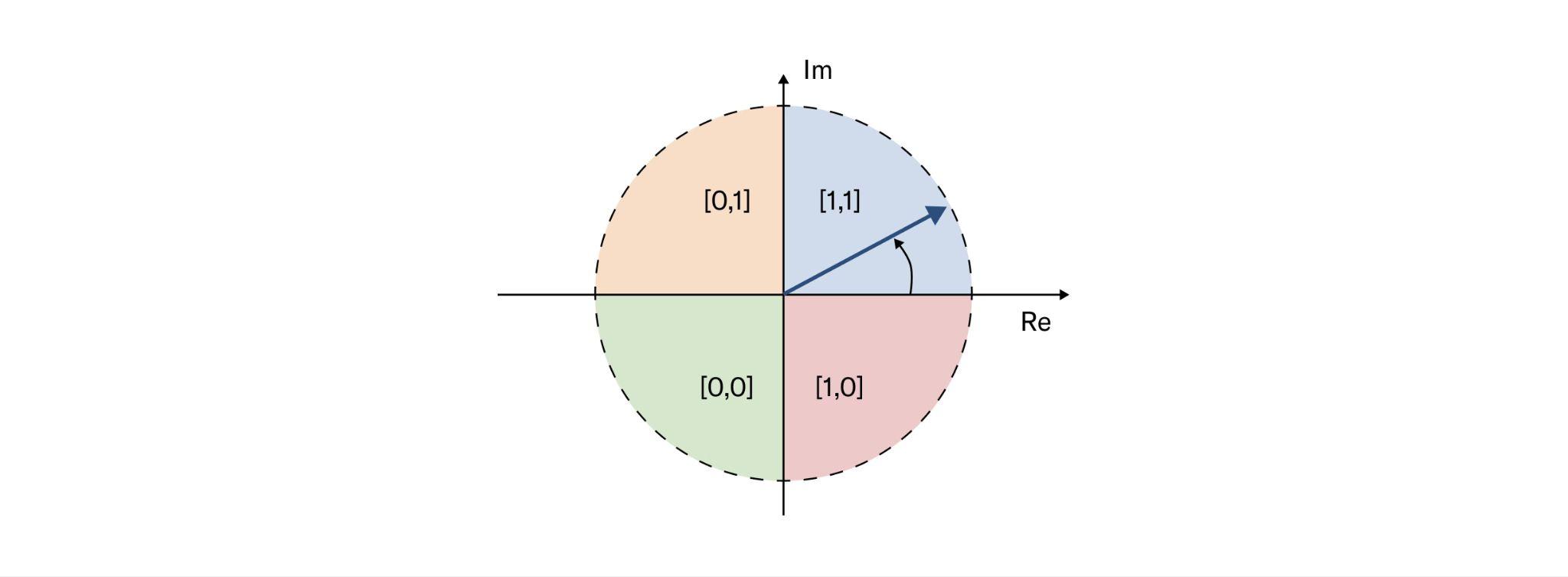
Another desirable feature of the phase-quadrant demodulation is that it produces a cyclic code. Unlike a binary code in which two bits may change, making some errors arbitrarily more costly than others, a cyclic code only allows a single bit change in rotation between any adjacent phase quadrants. Importantly, when a response falls very closely to the boundary between adjacent quadrants, its resulting code is considered a fragile bit. These fragile bits are usually less stable and could flip values due to changes in illumination, blurring or noise. There are many methods to deal with fragile bits, and one such method could be to assign them lower weights during matching.
When multi-scale Gabor filtering is applied to a given iris image, multiple iris codes are produced accordingly and concatenated to form the final iris template. Depending on the number of filters and their stride factors, an iris template can be several orders of magnitude smaller than the original iris image.
Robustness of iris codes
Because iris codes are generated based on the phase responses from Gabor filtering, they are rather robust against illumination, blurring and noise. To measure this quantitatively, each effect is added, namely, illumination (gamma correction), blurring (Gaussian filtering), and Gaussian noise to an iris image, respectively, in slow progression and measure the drift of the iris code. The amount of added effect is measured by the Root Mean Square Error (RMSE) of pixel values between the modified and original image, and the amount of drift is measured by the Hamming distance between the new and original iris code. Mathematically, RMSE is defined as:
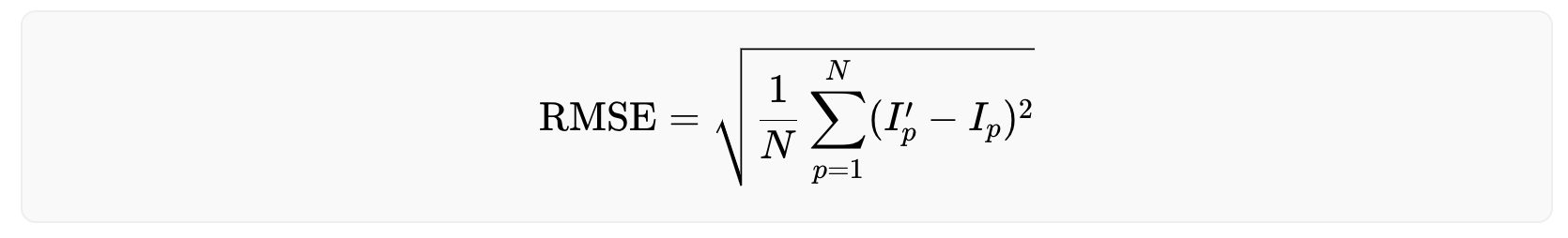
where N is the number of pixels in the original image I and the modified image I′. The Hamming distance is defined as:
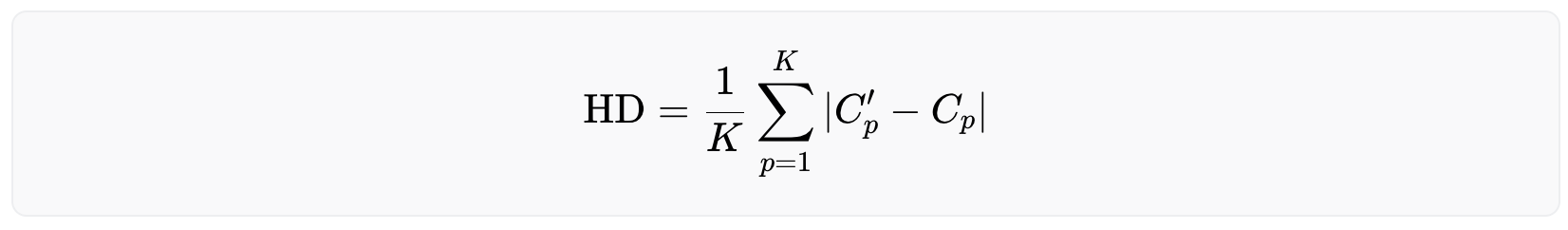
where K is the number of bits (0/1) in the original iris code C and the new iris code C′. A Hamming distance of 0 means a perfect match, while 1 means the iris codes are completely opposite. The Hamming distance between two randomly generated iris codes is around 0.5.
The following figures help explain the impact of illumination both visually and quantitatively, blurring and noise on the robustness of iris codes. For illustration purposes, these results are not generated with the actual filters that are deployed but nevertheless demonstrate the property in general of Gabor filtering. Also, the iris image has been normalized from a donut shape in the cartesian coordinates to a fixed-size rectangular shape in the polar coordinates. This step is necessary to standardize the format, mask-out occlusion and enhance the iris texture.
As shown in the figure below, iris codes are very robust against grey-level transformations associated with illumination as the HD barely changes with increasing RMSE. This is because increasing the brightness of pixels reduces the dynamic range of pixel values, but barely affects the frequency or spatial properties of the iris texture.

Blurring, on the other hand, reduces image contrast and could lead to compromised iris texture. However, as shown below, iris codes remain relatively robust even when strong blurring makes iris texture indiscernible to naked eyes. This is because the phase information from Gabor filtering captures the location and presence of texture rather than its strength. As long as the frequency or spatial property of the iris texture is present, though severely weakened, the iris codes remain stable. Note that blurring compromises high frequency iris texture, therefore, impacting high frequency Gabor filters more, which is why a bank of multi-scale Gabor filters are used.

Finally, observe bigger changes in iris codes when Gaussian noise is added, as both spatial and frequency components of the texture are polluted and more bits become fragile. When the iris texture is overwhelmed with noise and becomes indiscernible, the drift in iris codes is still small with a Hamming distance below 0.2, compared to matching two random iris codes (≈0.5). This demonstrates the effectiveness of iris feature generation using Gabor filters even in the presence of noise.

Conclusion
Iris feature generation is a necessary and important step in iris recognition. It reduces the dimensionality of the iris representation from a high resolution image to a much lower dimensional binary code, while preserving the most discriminative texture features using a bank of Gabor filters. It is worth noting that Gabor filters have their own limitations, for example, one cannot design Gabor filters with arbitrarily wide bandwidth while maintaining a near-zero DC component in the even-symmetric filter. This limitation can be overcome by using the Log Gabor filters. In addition, Gabor filters are not necessarily optimized for iris texture, and machine-learned iris-domain specific filters (e.g. BSIF) have the potential to achieve further improvements in feature generation and recognition performance in general. Moreover, the project’s contributors are investigating novel approaches to leverage higher quality images and the latest advances in the field of deep metric learning and deep representation learning to push the accuracy of the system beyond the state-of-the-art to make the system as inclusive as possible.
As the resilience of iris feature generation amidst external factors was showcased, it is crucial to note that even minor fluctuations in iris code variability hold significant importance when dealing with a billion people, as the tail-end of the distribution dictates the error rates, thus influencing the number of false rejections.
Iris Inference System
Building upon the theoretical foundation established in the previous sections, this section now focuses on the practical application of these principles within World. Having explored the scalability of iris recognition technology and the process of feature generation using Gabor wavelets, this section explains the details of the image processing. By the end of this section, one will have a thorough understanding of how World's iris recognition algorithm functions to ensure accurate and scalable verification of an individual's uniqueness.
Pipeline overview
The objective of this pipeline is to convert high-resolution infrared images of a human's left and right eye into an iris code: a condensed mathematical and abstract representation of the iris' entropy that can be used for verification of uniqueness at scale. Iris codes have been introduced by John Daugman in this paper and remain to this day the most widely used way to abstract iris texture in the iris recognition field. Like most state-of-the-art iris recognition pipelines, World’s pipeline is composed of four main segments: segmentation, normalization, feature generation and matching.
Refer to the image below for an example of a high resolution image of the iris acquired in the near infrared spectrum. The right hand side of the image shows the corresponding iris code, which is itself composed of response maps to two 2D Gabor wavelets. These response maps are quantized in two bits so that the final iris code has dimensions of , with and being the number of radial and angular positions where these filters are applied. For more details, see check the previous section. While only the iris code of one eye is shown below, note that an iris template consists of the iris codes from both eyes.
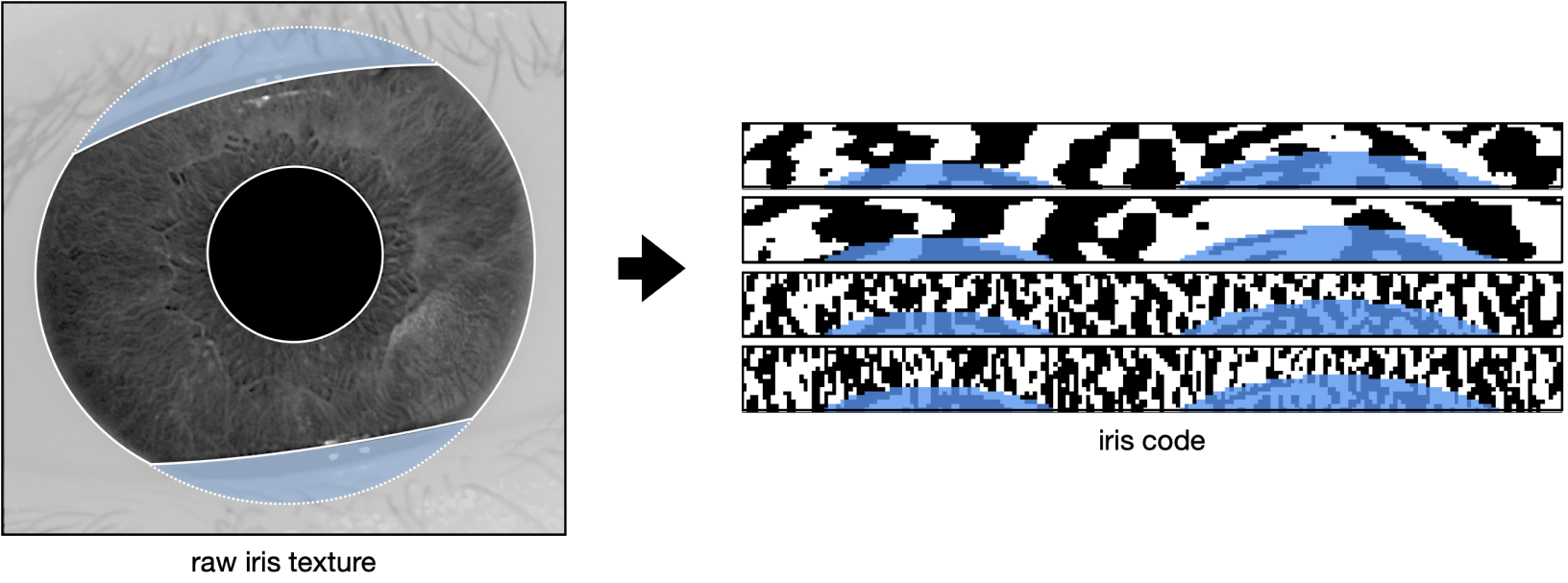
The purpose of the segmentation step is to understand the geometry of the input image. The location of the iris, pupil, and sclera are determined, as well as the dilation of the pupil and presence of eyelashes or hair covering the iris texture. The segmentation model classifies every pixel of the image as pupil, iris, sclera, eyelash, etc. These labels are then post-processed to understand the geometry of the subject's eye.
The image and its geometry then passes through tight quality assurance. Only sharp images where enough iris texture is visible are considered valid, because the quantity and quality of available bits in the final iris codes directly impact the system's overall performance.
Once the image is segmented and validated, the normalization step takes all the pixels relevant to the iris texture and unfolds them into a stable cartesian (rectangular) representation.
The normalized image is then converted into an iris code during the feature generation step. During this process, a Gabor wavelet kernel convolves across the image, converting the iris texture into a standardized iris code. For every point in a grid overlapping the image, two bits that represent the sign of the real and complex components of the filter response are derived, respectively. This process synthesizes a unique representation of the iris texture, which can easily be compared with others by using the Hamming distance metric. This metric quantifies the proportion of bits that differ between any two compared iris codes.
The following sections will explain each of the aforementioned steps in more detail, by following the journey of an example iris image through the biometric pipeline. This image was taken by the Orb, during a signup in the TFH lab. It is shared with user consent and faithfully represents what the camera sees during a live uniqueness verification.
The eye is a remarkable system that exhibits various dynamic behaviors, including blinking, squinting, closing, as well as the ability of the pupil to dilate or constrict and the eyelashes or any object to cover the iris. The following section also explores how the biometric pipeline can be robust in the presence of such natural variability.
Segmentation
Iris recognition was first developed in 1993 by John Daugmann and, although the field has advanced since the turn of the millennium, it continues to be heavily influenced by legacy methods and practices. Historically, the morphology of the eye in iris recognition has been identified using classical computer vision methods such as the Hough Transform or circle fitting. In recent years, Deep Learning has brought about significant improvements in the field of computer vision, providing new tools for understanding and analyzing the eye physiology with unprecedented depth.
Novel methods for segmenting high-resolution infrared iris images are proposed in Lazarski et al by the Tools for Humanity team. The architecture consists of an encoder that is shared by two decoders: one that estimates the geometry of the eye (pupil, iris, and eyeball) and the other that focuses on noise, i.e., non-eye-related elements that overlay the geometry and potentially obscure the iris texture (eyelashes, hair strands, etc.). This dichotomy allows for easy processing of overlapping elements and provides a high degree of flexibility in training these detectors. The architecture takes into account the DeepLabv3+ architecture with a MobileNet v2 backbone.
Acquiring labels for noise elements is significantly more time-consuming than acquiring labels for geometry, as it requires a high level of precision for identifying intertwined eyelashes. It takes 20 to 80 minutes to label eyelashes in a single image, depending on the levels of blur and the subject's physiology, while it only takes about 4 minutes to label the geometry to required levels of precision. For that reason, noise objects (e.g. eyelashes) are decoupled from geometry objects (pupil, iris and sclera) which allows for significant financial and time savings combined with a quality gain.
The model was trained over a mix of Dice Loss and Boundary Loss. The Dice loss can be expressed as
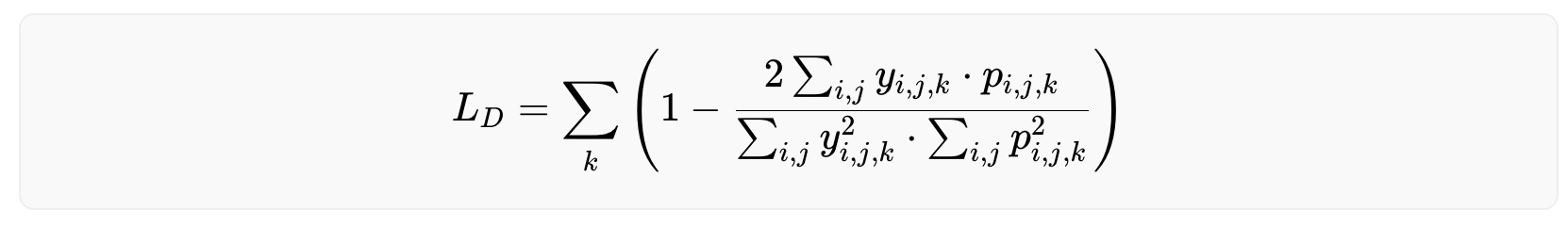
with being the one-hot encoded ground truth and the model’s output for the pixel (i,j) as a probability. The third index k represents the class (e.g. pupil, iris, eyeball, eyelash or background). The Dice loss essentially measures the similarity between two sets, i.e. the label and the model's prediction.
Accurate identification of the boundaries of the iris is essential for successful iris recognition, as even a small warp in the boundary can result in a warp of the normalized image along the radial direction. To address this, a weighted cross-entropy loss was also introduced that focuses on the zone at the boundary between classes, in order to encourage sharper boundaries. It is mathematically represented as:
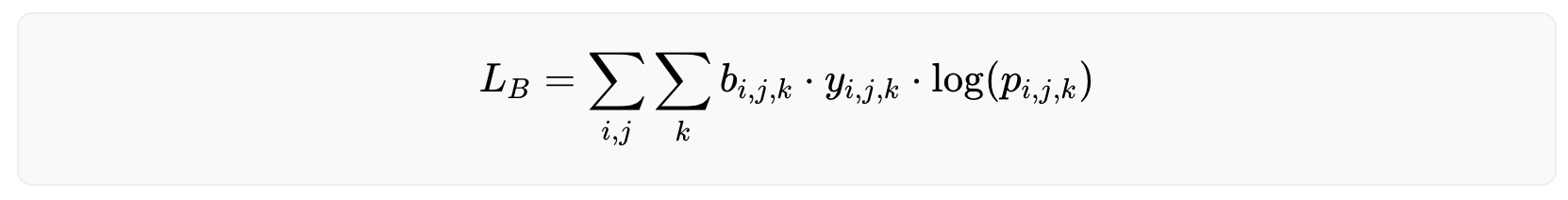
with the same notations as before and being the boundary weight, which represents how close the pixel (i,j) is to the boundary between class k and any other class. A Gaussian blur is then applied to the contour to prioritize the precision of the model on the exact boundary while keeping a lower degree of focus on the general area around it.
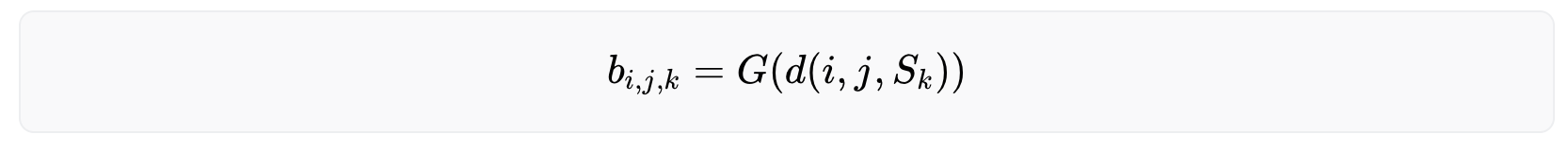
With being the distance between the point and the surface as the minimum of the euclidean distances between (i,j) and all points of . is the boundary between class and all other classes, the Gaussian distribution centered at 0 with some finite variance.
Experiments were conducted with other loss functions (e.g. convex prior), architectures (e.g. single-headed model), and backbones (e.g. ResNet-101) and this setup was found to have the best performance in terms of accuracy and speed. The following graph shows the iris image overlayed by the segmentation maps as predicted by the model. In addition, landmarks are displayed calculated by a separate quality assessment AI model during the image capture phase. This model produces quality metrics to ensure that only high-quality images are used in the segmentation phase and that the iris code is generated accurately for verification of uniqueness: sharp image focused on the iris texture, well-opened eye gazing in the camera, etc.
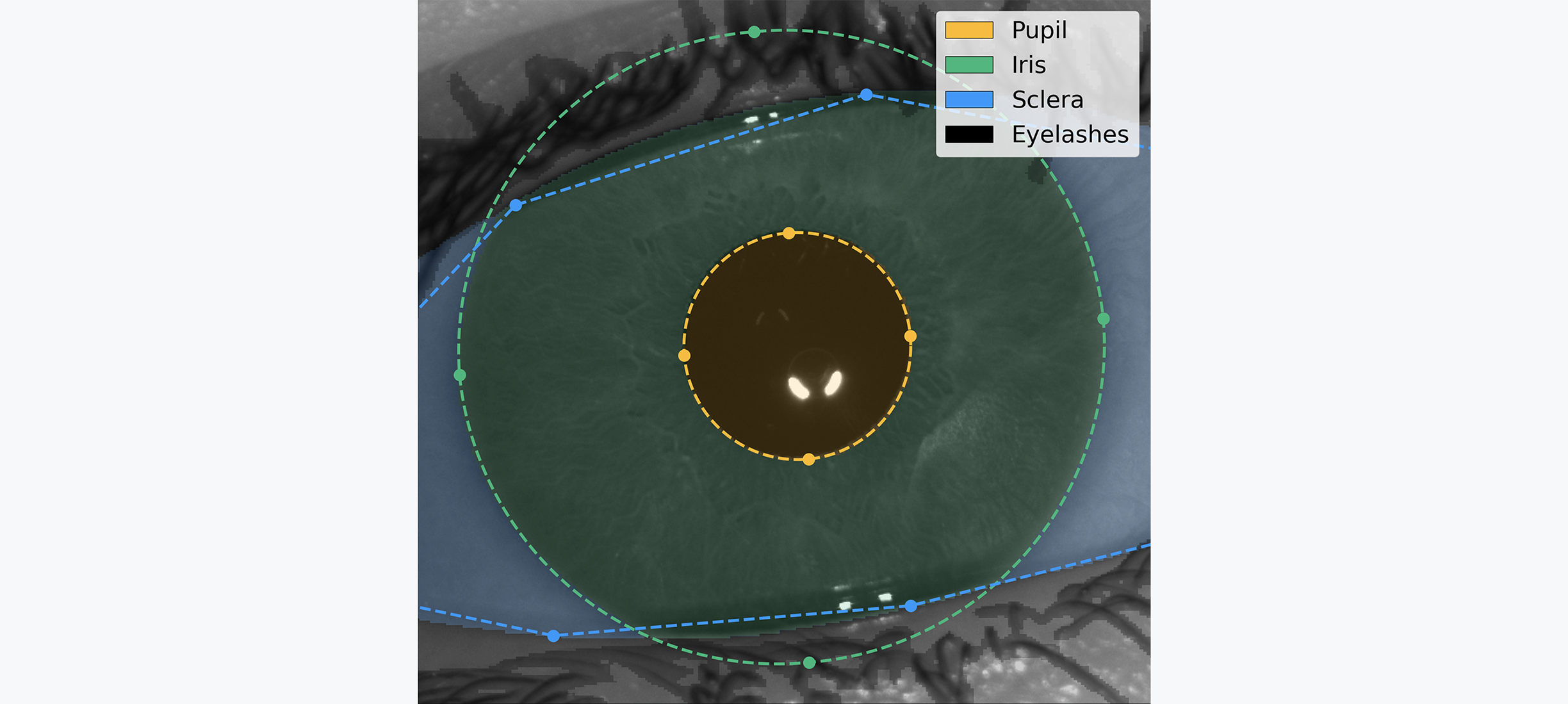
Normalization
The goal of this step is to separate meaningful iris texture from the rest of the image (skin, eyelashes, sclera, etc.). To achieve this, the iris texture is projected from its original cartesian coordinate system to a polar coordinate system, as illustrated in the following image. The iris orientation is defined as the vector pointing from one pupil center to the other pupil center of the opposite eye.
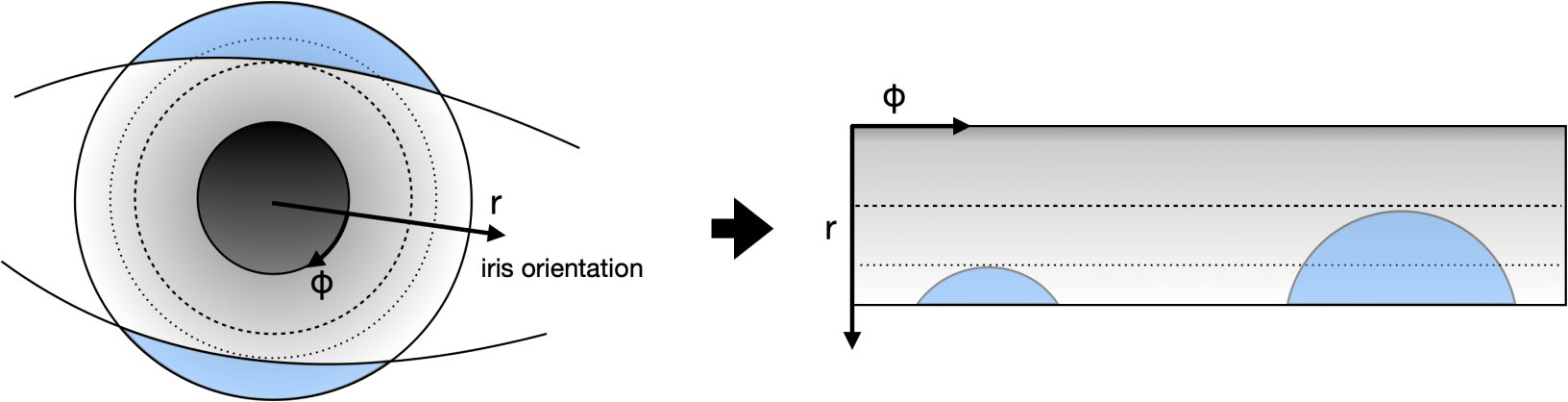
This process reduces variability in the image by canceling out variations such as the person’s distance from the camera, the pupil constriction or dilation due to the amount of light in the environment, and the rotation of the person’s head. The image below illustrates the normalized version of the iris above. The two arcs of circles visible in the image are the eyelids, which were distorted from their original shape during the normalization process.
Feature generation
Now that a stable, normalized iris texture is produced, an iris code can be coded that can be matched at scale. In short, various Gabor filters stride across the image and threshold its complex-valued response to generate two bits representing the existence of a line (resp. edge) at every selected point of the image. This technique, pioneered by John Daugmann, and the subsequent iterations proposed by the iris recognition research community, remains state-of-the-art in the field.
Matching
Now that the iris texture is transformed into an iris code, it is ready to be matched against other iris codes. To do so, a masked fractional Hamming Distance (HD) was used: the proportion of non-masked iris code bits that have the same value in both iris codes.
Due to the parametrization of the Gabor wavelets, the value of each bit is equally likely to be 0 or 1. As the iris codes described above are made of more than 10,000 bits, two iris codes from different subjects will have an average Hamming distance of 0.5, with most (99.95%) iris codes deviating less than 0.05 HD away from this value (99.9994% deviating less than 0.07 HD). As several rotations of the iris code are compared to find the combination with highest matching probability, this average of 0.5 HD moves to 0.45 HD, with a probability of being lower than 0.38 HD.
It is therefore an extreme statistical anomaly to see two different eyes producing iris codes with a distance lower than 0.38 HD. On the contrary, two images captured of the same eye will produce iris codes with a distance generally below 0.3 HD. Applying a threshold in between allows the ability to reliably distinguish between identical and different identities.
To validate the quality of the algorithms at scale, their performance was evaluated by collecting 2.5 million pairs of high-resolution infrared iris images from 303 different subjects. These subjects represent diversity across a range of characteristics, including eye color, skin tone, ethnicity, age, presence of makeup and eye disease or defects. Note that this data was not collected during field operations but stems from contributors to World and from paid participants in a dedicated session organized by a respected partner. Using these images and their corresponding ground truth identities, the false match rate (FMR) and false non match rate (FNMR) of the system was measured.
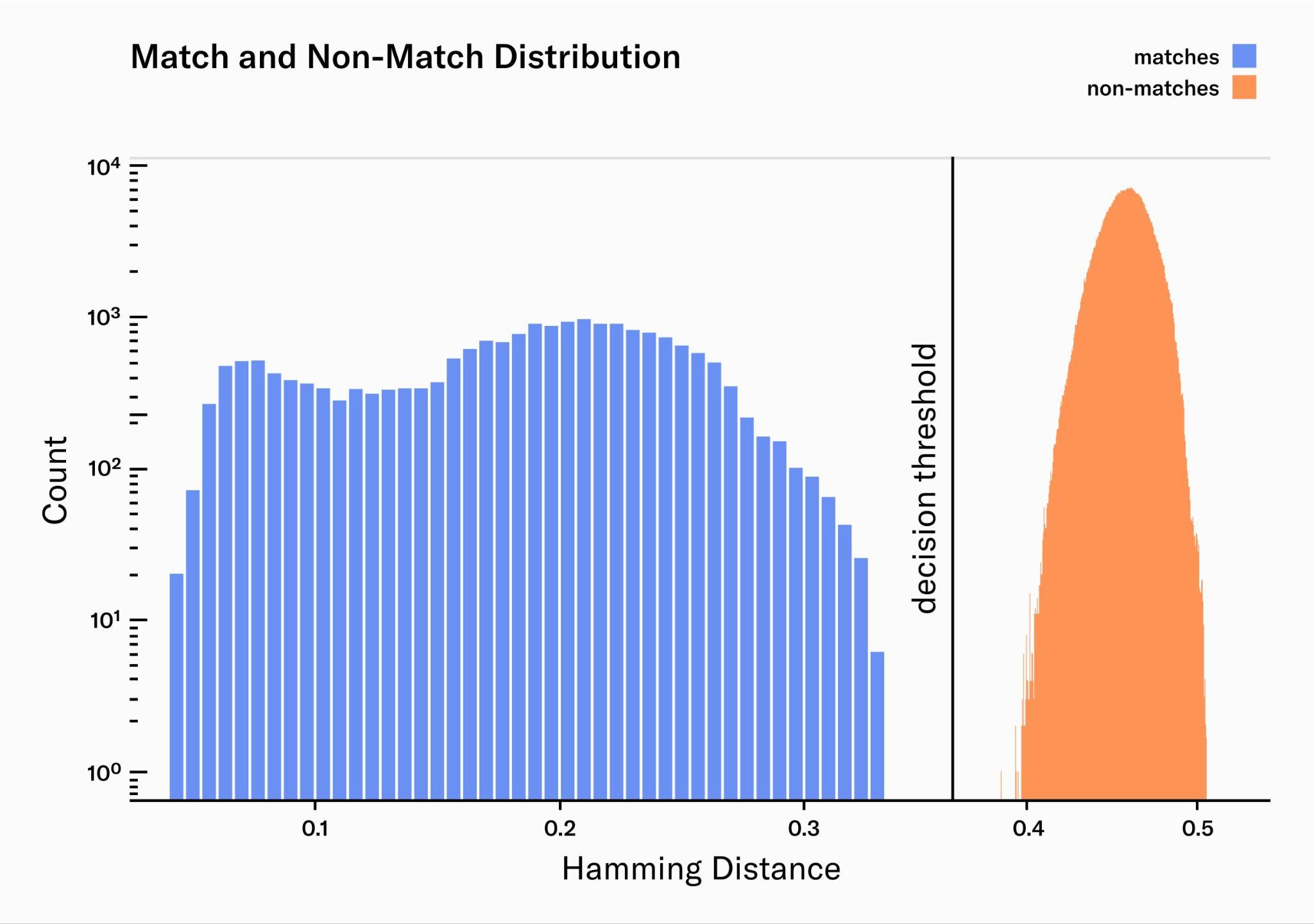
From 2.5 million image pairs, all were correctly classified as either a match or non-match. Additionally, the margin between the match and non-match distributions is wide, providing a comfortable margin of error to accommodate for potential outliers.
The match distribution presents two clear peaks, or maxima. The peak on the left (HD≈0.08) corresponds to the median Hamming distance for pairs of images taken from the same person during the same capture process. This means that they are extremely similar, as one would expect from two images of the same person. The peak on the right (HD≈0.2) represents the median Hamming distance for pairs of images taken from the same person but during different enrollment processes, often weeks apart. These are less similar, reflecting the naturally occurring variations in the same person's images taken at different times like pupil dilation, occlusion and eyelashes. Systems to narrow the matches distribution are continuously being iterated on: better auto-focus and AI-Hardware interactions, better real-time quality filters, Deep Learning feature generation, image noise reduction, etc.
As there were no misclassified iris pairs, FMR and FNMR cannot be calculated exactly. However, an upper bound for both rates can be estimated:

With these numbers, uniqueness on a billion people scale can be verified with very high accuracy. However, also acknowledged is the fact that the dataset used for this evaluation could be enlarged and more effort is needed to build larger and even more diverse datasets to more accurately estimate the biometric performance.
Conclusions
In this section, the key components of World’s uniqueness verification pipeline are presented. It illustrated how the use of a combination of deep learning models for image quality assessment and image understanding, in conjunction with traditional feature generation techniques, enables accurate verification of uniqueness on a global scale.
However, work in this area is ongoing. Currently, the team at TFH is researching an end-to-end Deep Learning model, which could yield faster and even more accurate uniqueness verification.
Iris code Upgrades
While the accuracy of the uniqueness verification algorithm of the Orb is already very high (with, specifically a false match rate of 1 in 40 trillion (1:1 match), an even higher accuracy would be beneficial on a billion people scale. To this end, the biometric algorithm is continuously being developed and will be upgraded over time.
There are three key types of upgrades that can increase accuracy further:
Image preprocessing upgrades.
These upgrades, which are backwards compatible, modify everything except the final step in the process: iris code feature generation. Elements such as the segmentation network and image quality thresholds are typical areas of improvement. For an in-depth look at the preprocessing algorithms, please refer to the image processing section. These types of upgrades generally occur multiple times a year.
Iris code generation upgrades for future verifications. Also backwards compatible, these upgrades involve modifying the iris code feature generation algorithm without recomputing previous iris codes. Such an upgrade involves the introduction of v2 codes, which are not compatible with the older v1 codes. Both v1 and v2 codes would be compared against their respective sets. If both comparisons result in no collision, the v2 code is added to the set of v2 codes. This way, the set of v1 codes doesn’t grow any more, yet none of the individuals who are part of the v1 set can get a second World ID.
In the event of an upgrade to the feature generation algorithm, the corresponding false match rate evolve as follows:
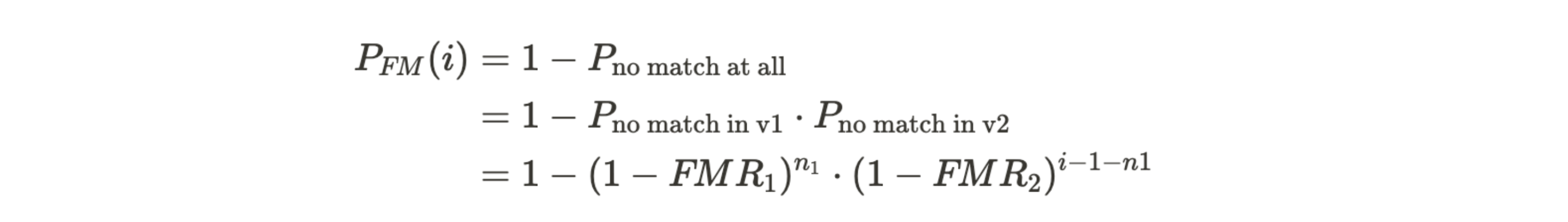
For an in-depth understanding of the error rates, please revisit the relevant information in the section biometric performance on a billion people scale. From the above equation we can deduce that the likelihood of the i-th legitimate user experiencing a false match continues to increase with the expansion of the v2 set. However, provided that , the rate of this growth is significantly reduced. For any individual included in the v1 set, the false non-match rate remains unaffected. For new enrollments, the false non-match rate of the v2 algorithm applies.
In principle, several such iris code versions can be stacked. This type of upgrade is expected to happen about once a year.
Recomputing existing iris codes. These upgrades may or may not be backwards compatible, depending on whether the original image is still available. These are expected to occur less frequently than iris code generation upgrades and to become less frequent over time.
To understand when a recomputation might be required, let us define the number of codes in the set of v1 codes as and similarly for v2 codes. If the error rates of the v1 code are much worse than the ones of v2 codes and therefore have major influence on the false match rate even at , the set of v1 codes should eventually be recomputed. For this to be possible, the iris images need to be available. This can happen in several ways:
Re-capture images. Individuals could return to an Orb. Depending on the distance to an Orb and individual preferences this may or may not be a realistic option.
Custodial image storage. Upon request, the issuer can securely store the images and automatically recompute the iris code if necessary. Currently, this is an option for individuals, but it is likely to be discontinued with the introduction of self custodial image storage.
Self custodial image storage. Expected to be introduced in late 2023, this option allows individuals to store their signed and end-to-end encrypted images on their device. For recomputing iris codes, individuals can upload their images temporarily to a dedicated, audited cloud environment that deletes images upon recomputation, or perform the computation locally on their phones. To ensure integrity, the local computation requires the upgrade to happen within a zero-knowledge proof, necessitating the use of Zero-Knowledge Machine Learning (ZKML) on the individual’s phone. The feasibility of this approach depends on the computational capabilities of the individual’s phone and ongoing ZKML research.
If local computation or temporary upload isn't viable or preferable, individuals can always revisit an Orb where the iris code is computed locally.
Biometric Uniqueness Service
While the iris code is computed locally on the Orb, the biometric uniqueness service i.e. the determination of uniqueness based on the iris code is performed on a server since the iris code needs to be compared against all other iris codes of humans who have verified before. This process is getting increasingly computationally intensive over time. Today, the biometric uniqueness service is run by Tools for Humanity. However, this should not be the case forever and there are several ideas regarding the decentralization of this service.
World Network Protocol
World Network is a blockchain-based protocol that consists of both off-chain and on-chain components (smart contracts) and is based on Semaphore from the Ethereum PSE group. The Protocol supports the World Network mission by distinguishing humans from non-human actors online, privately but uniquely identifying individuals to solve certain classes of problems related to abuse, fraud, and spam.
Current Status
The Protocol originally deployed on Polygon during its beta phase, and the current version runs on Ethereum with a highly scalable batching architecture. Bridges are in place for Optimism and Polygon PoS state changes on Ethereum, with each batch insertion being replicated to those chains. As of this writing, over two million users have been successfully enrolled with a combination of these deployments, representing an average load of almost five enrollments per minute.
Technical Implementation
While the Orb adheres to data minimization principles such that no raw biometric data (e.g. iris images) needs to leave the device, it calculates and transmits iris codes that are stored and processed separately from the user’s profile data or the user’s wallet address. The first version of the Protocol originated as a solution to this fundamental privacy challenge specifically for the WLD token airdrop. At its core, the Protocol combines the Orb-based uniqueness verification with anonymous set-membership proofs, thus allowing the issuer to determine whether the user has claimed their WLD tokens without collecting any further information about them. Realizing this solves a hard problem others are also facing, World ID was created in order to allow third parties to use the Orb-verified “unique human set” in the same privacy-preserving way.
Users start enrollment by creating a Semaphore keypair on their smartphone, hereafter referred to as the World ID keypair. The Orb associates the public key with a user’s iris code, whose current sole purpose is to be used in the uniqueness check. If this check succeeds, the World ID public key gets inserted into an identity set maintained by a smart contract on the Ethereum blockchain. The updated state is subsequently bridged to Optimism and Polygon PoS so World ID can be used natively on those chains. Integration with other EVM-based chains is straightforward, and integration with non-EVM chains is possible as long as the bridged chain has a gas-efficient means of verifying Groth16 proofs. After enrollment the user can prove their inclusion in this identity set, and therefore their unique personhood, to third parties in a trustless and private way. Since the scheme is private, it’s usually necessary to tie this proof to a particular action (e.g. claiming WLD tokens or voting on a proposal).
In the above scheme, the wallet creates a Groth16 proof that proves a user knows the private key to one of the public keys in the on-chain identity set and the action. An optional signal, like the preferred option in a vote, can also be included. By design, this provides strong anonymity of the size of the whole set. It is not possible to learn the public key or anything relating to the enrollment, including the iris code, other than that it was successfully completed, so long as the private key does not leak. It is also not possible to learn that two proofs came from the same person if the scheme is used for different applications.
In the context of the Orb verification, the Orb is the only trusted component in the system; after enrollment, World ID can be used in a permissionless way.
Overall Architecture and User Flow
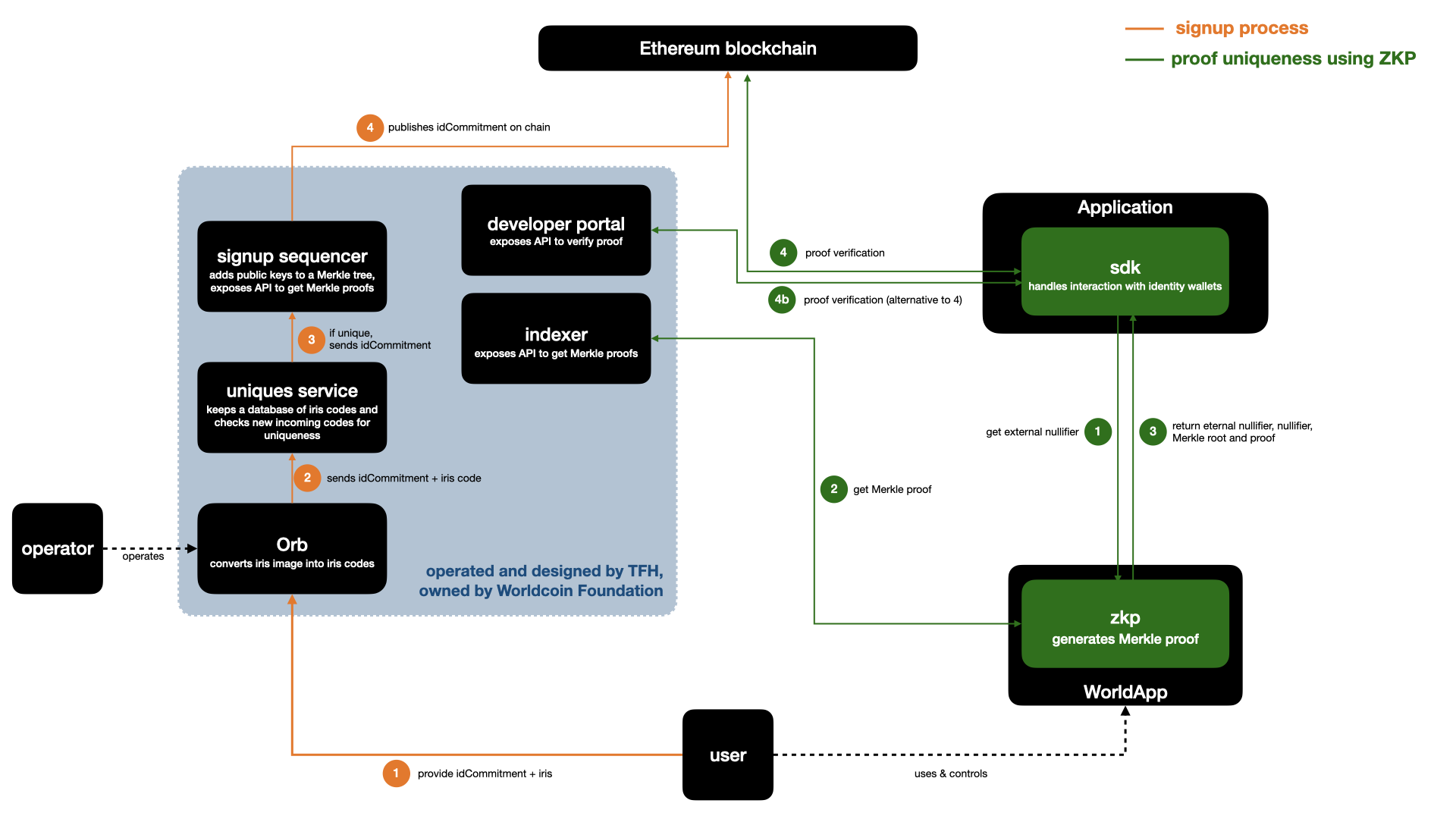
As mentioned, at the heart of the Protocol is the Semaphore anonymous set-membership protocol — an open-source project originally developed by a team from the Ethereum Foundation and extended by World. Semaphore is unique in that it takes the basic cryptographic design for privacy as found in anonymous voting and currencies and offers it as a standalone library. Semaphore stands out in its simplicity: It uses a minimalistic implementation while providing maximum freedom for implementers to design their protocols on top. Semaphore’s straightforward design also allows it to make the adaptations required to support multiple chains and enroll a billion people efficiently. World’s version of Semaphore is deployed as a smart contract on Ethereum, with a single set containing one public key (called an identity commitment) for each enrolled user. A commitment to this set is replicated to other chains using state bridges so that corresponding verifier contracts can be deployed there.
Users interact with the Protocol through an identity wallet containing a Semaphore key pair specific to World ID. Semaphore does not use an ordinary elliptic curve key pair, but leverages a digital signature scheme using a ZKP primitive. The private key is a series of random bytes, and the public key is a hash of those bytes. The signature is a ZKP that the private key hashes to the public key. Specifically, the hash function is Poseidon over the BN254 scalar field. The public key is not used outside of the initial enrollment (for interactions with smart contracts, the wallet also contains a standard Ethereum key pair). The user can initiate World ID verifications directly from the app, by scanning a QR code or tapping on a deep link. Upon confirmation, a ZKP is computed on the device and sent through the World ID SDK directly to the requesting party (e.g. a third-party decentralized application, or dApp).
Developers can integrate World ID on-chain using the central verifier contract. As part of any other business logic, the developer can call the verifier to validate a user-provided proof. The developer at a minimum provides an application ID and action (which are used to form the external nullifier). The external nullifier is used to determine the scope of the Sybil resistance, i.e. that a person is unique for each context. Within the zero-knowledge circuit that a user computes to generate a proof with their World ID, the external nullifier is hashed in conjunction with the user’s private key to generate a nullifier hash. The same person may register in multiple contexts but will always produce the same nullifier hash for a specific context. The developer may also provide an optional message (called a signal) which the user will commit to within the ZKP.
If the proof is valid, the developer knows that whoever initiated the transaction is a verified human being. The developer can then enforce uniqueness on the nullifier hash to guarantee sybil resistance.
For example, to implement quadratic voting, one would use a unique identifier for the governance proposal as context and the user’s preferred choice as message. In case of airdrops (just as for WLD tokens), the associated message would be the user’s Ethereum wallet address.
Alternatively, World ID can be used off-chain. On the wallet side, everything remains the same. The difference is that the proof-verification happens on a third-party server. The third-party server still needs to check whether the given set commitment (i.e. Merkle root) corresponds to the on-chain set. This is done using a JSON-RPC request to an Ethereum provider or by relying on an indexing service. All of that is abstracted away by the World ID SDK and additional tooling in order to provide a better developer experience.
Enrollment Process
This section outlines how the enrollment process works for generating a World ID and verifying at an Orb.

The Semaphore protocol provides World ID with anonymity, but by itself it does not satisfy World’s scaling requirements. A regular insertion takes about a million gas (a unit of transaction cost in Ethereum). Gas prices fluctuate heavily on Ethereum, but this transaction could easily cost over $100 in today’s fee market, making it prohibitively expensive to sign up billions of people.
One could use cheaper alternatives to Ethereum, but that comes at the cost of security and adoption; Ethereum has the largest app ecosystem and World aims for World ID to be maximally useful. For that, it is best to start from Ethereum and build out from there. However, from a cost perspective, there are limits to scaling atop Ethereum, as the large insertion operation still happens on-chain. The most viable options are optimistic rollups, but these require considerable L1 calldata. Therefore, World scaled Semaphore using a zk-rollup style approach that uses one-third the amount of L1 calldata of optimistic rollups. The enrollment proceeds as follows (see above diagram):
- The user downloads the World App, which, on first start, generates a World ID keypair. In World App, private keys are optionally backed up (details on this coming soon). Additionally, an Ethereum keypair is also generated.
- To verify their account, the user generates a QR code on the World App and presents it to the Orb. This air-gapped approach ensures the Orb isn’t exposed to any sort of device or network-related information associated with the user’s device.
- The Orb verifies that it sees a human, runs local fraud prevention checks, and takes pictures of both irises. The iris images are converted on the Orb hardware into the iris code. Raw biometric data does not leave the device (unless explicitly approved by the user for training purposes).
- A message containing the user’s identity commitment and iris code is signed with the Orb’s secure element and then sent to the signup service, which queues the message for the uniqueness-check service.
- The uniqueness-check service verifies the message is signed by a trusted Orb and makes sure the iris code is sufficiently distinct from all those seen before using the Hamming distance as distance metric.
- If the iris code is sufficiently distant (based on the Hamming distance calculation), the uniqueness service stores a copy of the iris code to verify uniqueness of future enrollments and then forwards the user’s identity commitment to the signup sequencer.
- The signup sequencer takes the user’s identity commitment and inserts it into a work queue for later processing by the batcher.
- A batcher monitors the work queue. When 1) a sufficiently large number of commitments are queued or 2) the oldest commitment has been queued for too long, the batcher will take a batch of keys from the queue to process.
- The batcher computes the effect of inserting all the keys in the batch to the identity set, the on-chain Semaphore Merkle tree. This results in a sequence of Merkle tree update proofs (essentially a before-and-after inclusion proof). The prover computes a Groth16 proof with initial root, final root, and insertion start index as public inputs. The private inputs are a hash of public keys and the insertion proofs.
- For optimization purposes, the above-mentioned “public inputs” are actually keccak-hashed as a single public input and non-hashed as private inputs, which reduces the on-chain verification cost significantly. The circuit verifies that the initial tree leaves are empty and correctly updated. Computing the proof for a batch size of 1,000 takes around 5 minutes on a single AWS EC2 hpc6a instance.
- The batcher creates a transaction containing the proof, public input, and all the inserted public keys and submits it to a transaction relayer. Relayer assigns appropriate fees, signs the transaction, and submits it to (one or more) blockchain nodes. It also commits it to persistent storage so mispriced/lost transactions will be re-priced and re-submitted.
- The transaction is processed by the World ID contract, which verifies it came from the sequencer. The initial root must match the current one, and the contract hashes the provided public keys. Public keys are available as transaction calldata.
- The Groth16-verifier contract checks the integrity of the ZKP. An operation takes only about 350k gas for a batch of 100.
- The old root is deprecated (but still valid for some grace period), and the new root is set to the contract.
The ZKP guarantees the integrity of the Merkle tree and data availability. What sets it apart from the ideal zk-rollup model is the lack of validator decentralization; the implementation uses a single fixed-batch submitter.
After enrollment is complete, the user can use the World App autonomously. At that point, the system works in a decentralized, trustless and anonymous manner.
Details regarding trust assumptions and limitations for World ID can be found in the limitations section.
Verification Process
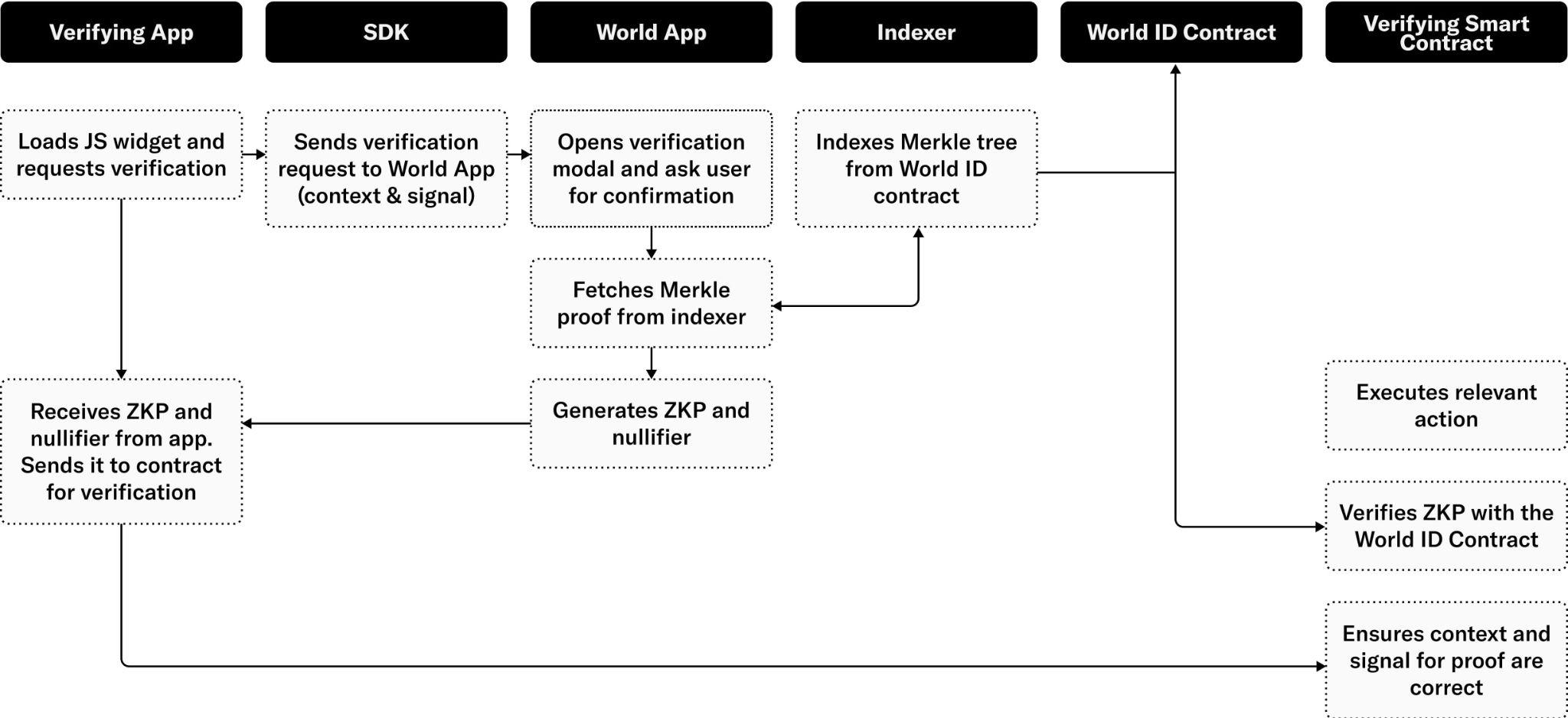
Developers can integrate World ID as part of a transaction (Web3) or request (Web2) through the World ID SDK:
- A verification process is triggered through one of the in-app options or through a QR code presented by a third-party application. Scanning the QR code opens the application. A verification request contains a context, message, and target. The context uniquely identifies the scope of the Sybil protection (e.g. the third-party application, a vote on a particular proposal, etc.). The message encodes application-specific business logic related to the transaction. The target identifies the receiving party of the claim (i.e. callback).
- The user inspects the verification details and decides to proceed using World ID. It is important that the user knows that the context is the intended one to avoid man-in-the-middle attacks.
- To generate a ZKP, the application needs a recent Merkle inclusion proof from the contract. It is possible to do this in a decentralized manner by fetching the tree from the contract, but at the scale of a billion users this requires downloading several gigabytes of data — prohibitive for mobile applications. To solve this, an indexing service that retrieves a recent Merkle inclusion proof on behalf of the application was developed. To use the service, the application provides its public key, and the indexer replies with an inclusion proof. Since this allows the indexer to associate the requester’s IP address to their public key, this constitutes a minor breach of privacy. One possible means to mitigate this is by using the services through an anonymization network1. The indexing service today is part of the sign up sequencer infrastructure and is open source, and anyone can run their own instance in addition to the one provided.
- The application can now compute a ZKP using a current Merkle root, the context, and the message as public inputs; the nullifier hash as public output; and the private key and Merkle inclusion proof as private inputs2. Note that no identifying information is part of the public inputs. The proof has three guarantees: 1) the private key belongs to the public key, hence proving ownership of the key, 2) the inclusion proof correctly shows that the public key is a member of the Merkle tree identified by the root, and 3) the nullifier is correctly computed from the context and the private key. The proof is then sent to the verifier.
- The verifier dApp will receive the proof and relay it to its own smart contract or backend for verification. When the verification happens from a backend in the case of Web2, the backend usually contacts a chain-relayer service as the proof inputs need to be verified with on-chain data.
- The verifier contract makes sure the context is the correct one for the action. Failing to do so leads to replay attacks where a proof can be reused in different contexts. The verifier will then contact the World ID contract to make sure the Merkle root and ZKP are correct. The root is valid if it is the current root or recently was the current root. It is important to allow for slightly stale roots so the tree can be updated without invalidating transactions currently in flight. In a pure append-only set, the roots could in principle remain valid indefinitely, but this is disallowed for two reasons: First, as the tree grows, the anonymity set grows as well. By forcing everyone to use similar recent roots, anonymity is maximized. Second, in the future one might implement key recovery, rotation, and revocation, which would invalidate the append-only assumption.
- At this point, the verifier is assured that a valid user is intending to do this particular action. What remains is to check the user has not done this action before. To do this, the nullifier from the proof is compared to the ones seen before3. This comparison happens on the developer side. If the nullifier is new, the check passes and the nullifier is added to the set of already seen ones.
- The verifier can now carry out the action using the message as input. They can do so with the confidence that the initiation was by a confirmed human being who has not previously performed an action within this context.
As the above process shows, there is a decent amount of complexity. Some of this complexity is handled by the wallet and World-provided services and contracts, but a big portion will be handled by third-party developed verifiers. To make integrating World ID as straightforward and safe as possible, an easy-to-use SDK containing example projects and reusable GUI components was developed, in addition to lower-level libraries.
Conceptually, the hardest part for new developers is the nullifiers. This is a standard solution to create anonymity, but it is little known outside of cryptography. Nullifiers provide proof that a user has not done an action before. To accomplish this, the application keeps track of nullifiers seen before and rejects duplicates. Duplicates indicate a user attempted to do the same action twice. Nullifiers are implemented as a cryptographic pseudo-random function (i.e. hash) of the private key and the context. Nullifiers can be thought of as context-randomized identities, where each user gets a fresh new identity for each context. Since actions can only be done once, no correlations exist between these identities, preserving anonymity. One could imagine designs where duplicates aren’t rejected but handled in another way, for example limiting to three tries, or once per epoch. But, because such designs correlate a user’s actions, they are recommended against. The same result can instead be accomplished using distinct contexts (i.e. provide three contexts, or one for each epoch).
For example, suppose the goal is that all humans should be able to claim a token each month. To do this, a verifier contract is deployed that can also send tokens. As context, a combination of the verifier-contract address and the current time rounded to months are used. This way each user can create a new claim each month. As the message, the address where the user wants to receive the token claim is used. To make this scalable, it is deployed on an Ethereum L2 and uses the World ID state bridge.
Multi-chain Support
While it’s important that World ID has its security firmly grounded, it is intended to be usable in many places. To make World ID multi-chain, the separation between enrollment and verification is leveraged. Enrollment will happen on Ethereum (thus guaranteeing security of the system), but verification can happen anywhere. Verification is a read-only process from the perspective of the World ID contract, so a basic state-replication mechanism will work.
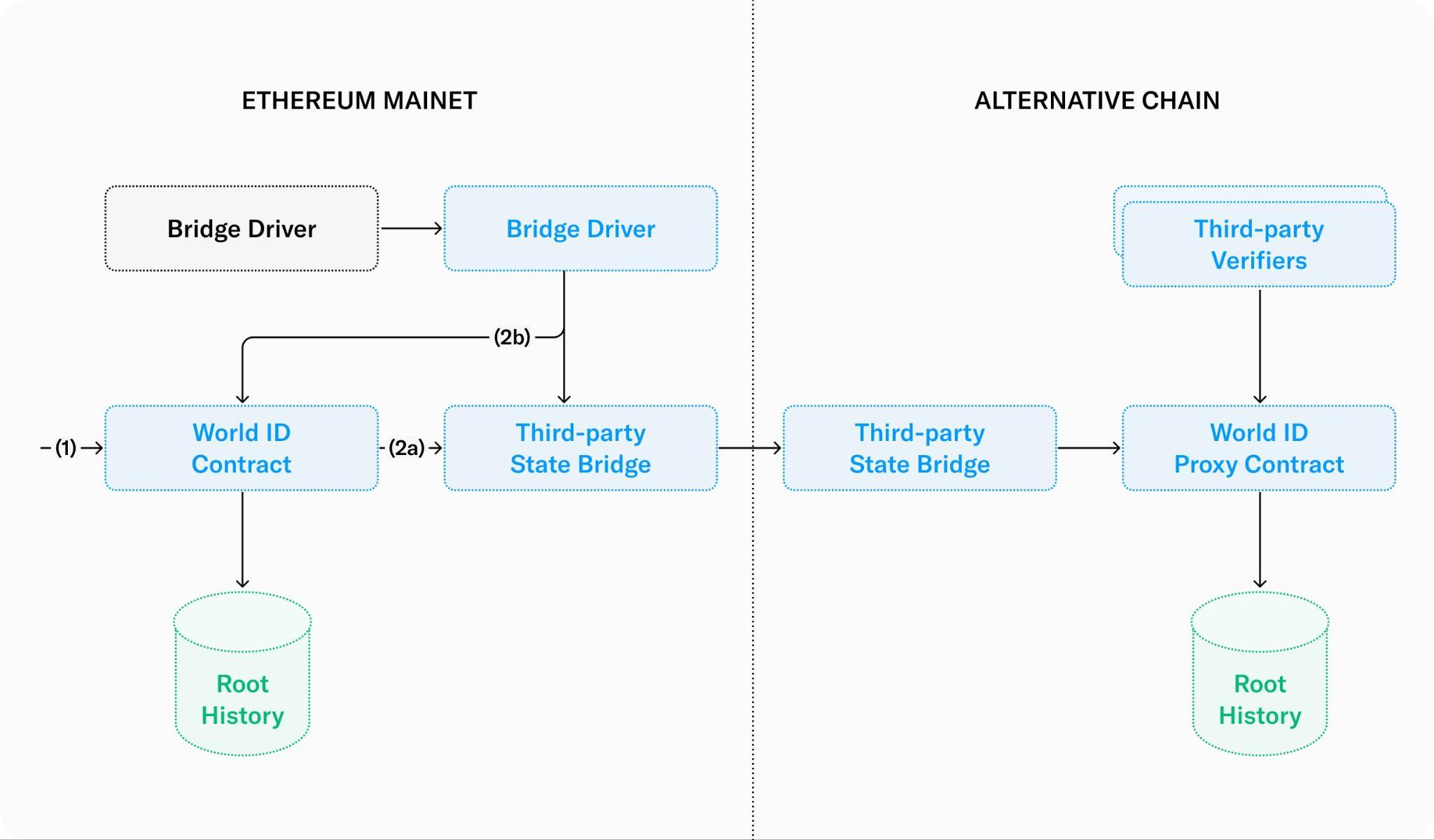
- Enrollment happens as before on Ethereum, but now each time the root history is updated a replication process is triggered.
- The replication is initiated by the World ID contract itself (route 2a) or by an external service that triggers a contract to read the latest roots from the contract (route 2b). Either way, the latest roots are pushed as messages to a third-party state bridge for the target chain.
- The Ethereum-side bridge contract forwards messages from Ethereum to the target chain. The details are implementation specific, but generally the direction from Ethereum to an L2 is easiest and fastest.
- The target-side bridge contract calls the World ID proxy contract with the new roots. After authenticating the message, the replica of the root history is updated. Now the proxy can be used for verification as if it were the main instance.
For the first bridge, a direct integration (2a) is used as this is the easiest and most reliable integration to implement. But direct routes require extension of the World ID contract, which are preferred to be kept to a minimum. So, for future bridges the externally driven route will be opted for. Externally driven integrations have the advantage of operating independently and can be added without modifying the World ID contract. In fact, anyone can build such a bridge.
For a target chain to support World ID, the most important requirement is Groth16-verification support. Groth16 is a widely supported proof system, but native support on some chains can be minimal. Secondary to this, World ID requires the existence of a reliable one-way message-passing bridge and sufficiently rich programmability with global persistent storage for the root history and nullifiers. For non-EVM target chains, there is extra work in porting the proxy and verifier contracts.
Data Handling
Blockchains play a primary role in the World ID Protocol, providing a trustless and decentralized source of truth (i.e. the list of valid credentials4 lives on-chain) and allow functionality such as revocation. Yet not all data is suited to live on-chain, which is why other-data handling mechanisms are introduced that are credential-specific and decided by issuers.
The diagram below shows the example of the Orb credential and how data is handled on-chain and off-chain.
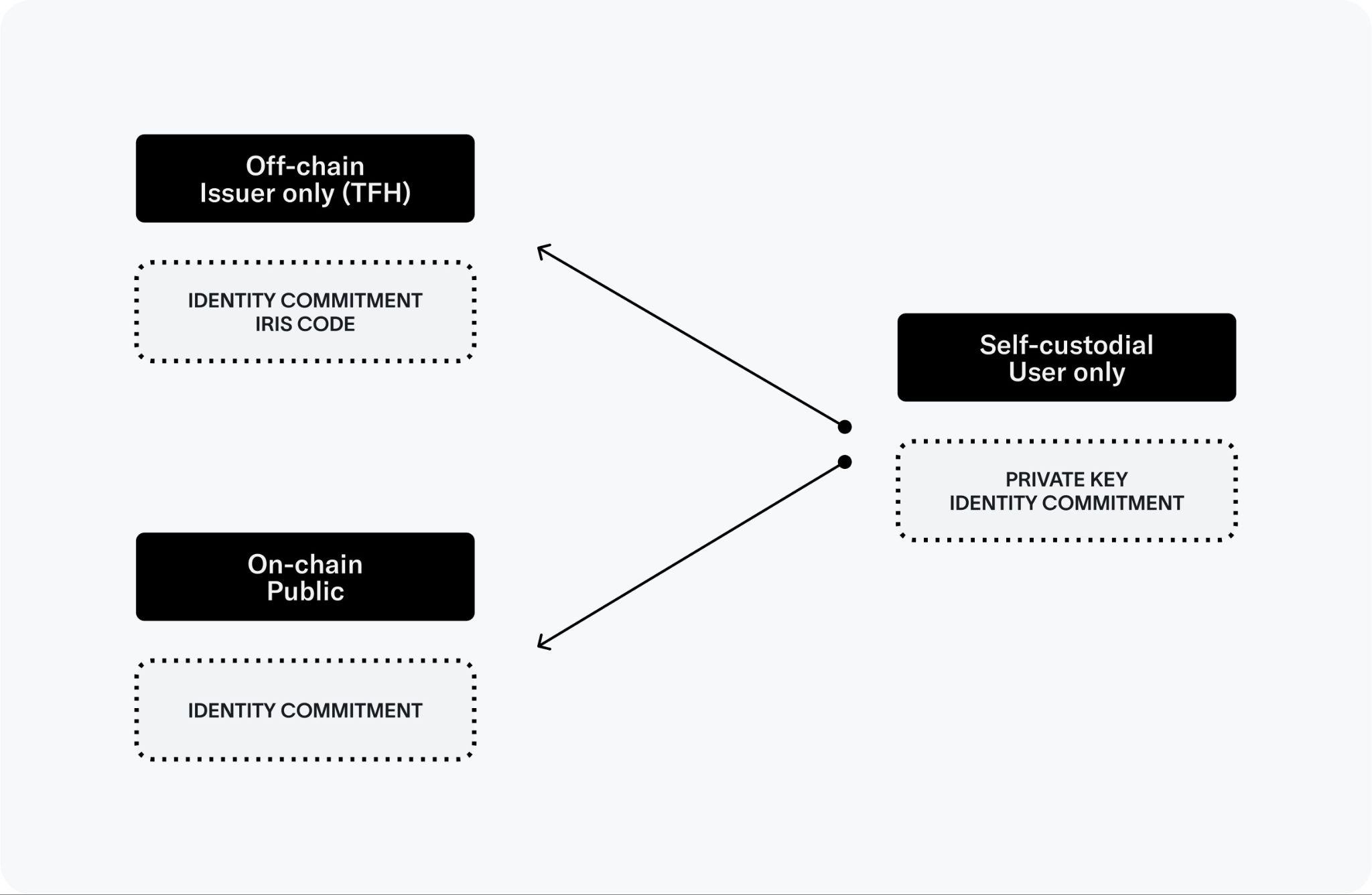
Versioning
The Orb credential must be subject to a versioning system, due to the evolution of algorithms used to transform iris images into iris codes. As training data is continually processed and research is pursued for more precise and quicker comparison algorithms, maintaining different versions becomes imperative.
What this means for users is that their Orb credential will have a “time-to-live,” or TTL, and at some point their signal may become deprecated and no longer recommended for use by third-party applications. When the credential expires, the user will be able to go to an Orb again to refresh their credential. One promising approach to allowing users to refresh their credential without going to an Orb or compromising their privacy is through zero-knowledge machine learning (ZKML):5
- When a user first enrolls at an Orb, the Orb will send their high-resolution signed iris image to the user’s device in an end-to-end encrypted, self-custodial manner. Users will be able to delete their images at any point in time.
- When the algorithm changes, the user’s wallet will get a prompt to update the iris code and download the relevant ML parameters.
- The user’s device will run the new ML model to generate the new iris code and a ZKP that asserts the model was properly run and the iris image is authentic.
- With the outputs above, the uniqueness and signup sequencer can update the user’s Orb credential seamlessly and privately.
Security Assessments
Two separate security assessments were conducted on the off-chain and on-chain components of the Protocol specifically related to its use of blockchain technologies, cryptography and smart contracts.
Future Development
World ID has and will continue to be developed iteratively. Development started by focusing on a single opinionated mechanism for proof of human, with particular attention to inclusivity and accuracy, hence the Orb. This section briefly introduces the different workstreams for future developments of the Protocol.
Recovery
Status: Active Development | Proof of Concept | Very High Priority
As previously mentioned, recovery is key for any proof-of-personhood protocol, and World ID is no exception. A user must always be able to maintain access and even get back their World ID in the case of theft, loss, etc. Recovery is initially being introduced to the Protocol by incorporating credential re-issuance, i.e. when a user loses their World ID, they get their credentials re-issued and the old ones revoked. This section outlines how this happens for the Orb proof-of-personhood mechanism.
There is ongoing research to understand whether a more abstract recovery mechanism can and should be introduced at the Protocol level. One important consideration with such mechanisms is security. Having the possibility of recovering “everything” with a single mechanism can introduce vulnerabilities that can be exploited. To use a real world analogy, when one’s wallet is stolen, they don’t perform a single action that recovers their driver’s license, credit cards, and ID all at once.
An overview of the current roadmap can be found in the World ID: Implementing PoH at Scale section.
Plurality
Status: Active Development | v0 Beta Testing | High Priority
World started with World ID to be able to bootstrap the Protocol. However, there is a tradeoff between accuracy of the biometric-based Orb verification and its availability to everyone on the globe. The Orb is not yet available in every country, and as operations continue to scale, other proof of human mechanisms may be viable alternatives, for low stakes applications.
Proof-of-personhood representation in the digital world can be viewed as a spectrum, rather than binary, as there are multiple ways to evaluate personhood — with varying degrees of accuracy.
The benefits of introducing different proof-of-personhood credentials to the Protocol are that it allows for:
- Wider Protocol usage while the Orb’s availability is scaled
- More issuers6, introducing further decentralization and resilience to the Protocol7
The drawbacks are:
- Deduplication across credentials is hardly possible, which can introduce the possibility of non-scalable Sybil attacks in some applications. For example, a World ID holder cannot be deduplicated from a unique phone number verification.
- If a high-accuracy credential reaches widespread adoption, the use of other credentials is likely to be less useful.
A beta test is currently underway with a unique phone number verification credential. This is at the low end of the spectrum in terms of accuracy, but it’s also something that is widely available across the world. While this is not a very reliable proof-of-personhood signal for something that requires a high level of assurance that someone is a unique person (e.g. universal basic income), it may be enough for low stakes applications.
Eventually, other parties (i.e. issuers) should be able to issue proof-of-personhood attestations (i.e. credentials). The verifier can then determine which attestations they accept, depending on the level of assurance their use case demands.
Interoperability
Status: Active Research | Proof of Concept | Medium Priority
Current internet applications are built on top of communication standards that have been progressively agreed on as a society. Similarly, widespread standards will be necessary for proof of human. These standards will extend the system’s interoperability and usability in a variety of contexts.
World ID is expected to integrate with widely used industry standards, current and future. This is a continuous effort, not a single end state. Already today, the Protocol is extending interoperability beyond its original inception. The first version was a single one-chain, one-credential system on the Polygon network. Today, it’s available on three chains: Ethereum, Optimism, and Polygon. It can also already be used in non-Web3-related contexts. The Protocol can be used with simple REST APIs, and even beyond that, it already integrates with widely used identity protocols like OpenID Connect (OIDC). In fact, a full-support integration with Auth0, a leading player in the identity space was launched.
Interoperability is not only being researched at the Protocol level but also at the SDK level. The World ID SDK can be conceptually split into two components: the wallet side and the application side. The application side already offers support for web and mobile applications, with further support being planned for more specific technologies, languages, and frameworks. The wallet side, which will offer portability of World ID and decentralization on the user side is currently being researched. Some of the challenges being researched to offer wallet portability are:
- Seamless but secure portability of secrets and metadata
- Trustworthy authentication, solving for the trust point of the user’s hardware
- Standardized risk management mechanisms
Privacy
Privacy is the bedrock on which World is built, and contributors to the project are committed to raising the bar far beyond today's best practices and ensuring that privacy is accessible to everyone. On a high level, custom hardware (like the Orb) enables the most privacy-preserving solution for proof of human (such as World ID). Getting privacy right, however, requires deliberate effort and additional work ‐ and the results must be demonstrable if they're to be trusted. This section explains in advanced technical detail how privacy is preserved in the different parts of World Network.
- A user-friendly introduction to privacy can be found in the Privacy page.
- An intermediate high-level overview on privacy for the more curious readers can be found in the privacy whitepaper.
Most of World Network's critical systems are designed in such a way that privacy cannot be compromised, even by any of the protocol’s contributors. This is achievable using cryptographically provable mechanisms such as Zero-Knowledge Proofs (ZKPs). World uses ZKPs to make it mathematically impossible to link usage of World ID across applications. Privacy protections such as these go beyond regulatory requirements.
Anyone can use the World App and their World ID fully pseudonymously.
Users don't have to provide personal information to register. No emails, no phone numbers, no social profiles, no names, everything is optional.
ZKPs are used to preserve the user's privacy and avoid cross-application tracking.
Whenever a user makes use of their World ID, ZKPs are used to prove they are a unique human. This means that no third-party will ever know a user's World ID or wallet public key, and in particular cannot track users across applications. It also guarantees that using World ID is not tied to any biometrical data or iris codes. When one wants to prove they are a unique human, they should be able to do so without revealing any personal information about themselves.
Image Custody Opt-In
Users have the option to opt-in to back up their images. This option exists because the algorithm that computes the iris code is still evolving to make sure it can support signing up everyone. This means using the images for training to improve the security and inclusivity of the network and to automatically update the user's iris code. Users who do not opt-in, can simply go back to an Orb to maintain their World ID verification if necessary. Updates are expected to be infrequent. In the near future, people should be able to backup this data self-custodially, and possibly, upgrade their iris code locally.
If a user opts-in to image custody, images are stored on an encrypted hard drive in the Orb before being uploaded. When a user does not opt-in, images are only processed in memory, and they never go through the hard drive. Furthermore, images for users who opted-in have a second layer of encryption via a public key of the server to make them irretrievable in the unlikely event of a compromised Orb. Uploads also happen over TLS. Once images are safely transmitted, they are encrypted at rest with AES-256.
Users can always change their mind and delete their stored images. The process is simple and processed quickly. Further, contributors are working on leveraging synthetic data to minimize the need for real images. This would further reduce the number of users that would even be needed to opt-in for training purposes.
An even more privacy-preserving approach is also being researched: performing these upgrades self-custodially. Users would still receive their images end-to-end encrypted and signed by the Orb. When a new algorithm is released, the parameters of the new model would be shared with the user's device. The user's device would run the model and generate a ZKP to confirm the inputs were valid, the model was run correctly and certifying the new iris code. The new iris code would be submitted with the ZKP and the user's World ID would be updated. While this system seems promising, technical challenges on zkML (Zero-Knowledge Machine Learning) and running complex models on a wide array of mobile devices have to be addressed.
To summarize:
- Image custody is optional.
- Any user can change their mind and delete their images easily from the app.
- No data collected, including images taken by the Orb has or will ever be sold. Nor will it be used for any other intent than to improve World ID. The World Foundation is bound to this commitment through the data consent form. where it states: “We will never sell your data. We will also not use any data listed in this form to track you or to advertise third parties’ products to you,” and that “We will not sell, lease, trade, or otherwise profit from your biometric data.”
The iris fragment
As discussed, the iris code is a numerical representation of the texture of a person's iris. It holds the property that it can be compared against different images of the same iris to determine whether the images came from the same iris.
The iris code cannot be a simple hash of the texture of the iris. This is because two pictures of the same iris will not be exactly the same. A myriad of factors change (lighting, occlusion, angle, etc.) in image capturing and a tiny change would lead to a different hash. With the iris code, those factors only lead to slightly modified Hamming distance between two codes which permits fuzzy comparison of irises. If the distance is below a certain threshold, the images are assumed to be from the same iris.
The iris code is computed by applying a set of 2D Gabor filters at various points of the iris texture, which leads to complex-valued filter responses. Only the phase information of the filter responses is taken into account (which means there is permanent information loss) and subsequently quantized in two bits. In other words: For each Gabor wavelet and each point of interest in the iris texture two bits are computed. Concatenating all these bits makes up the iris code.
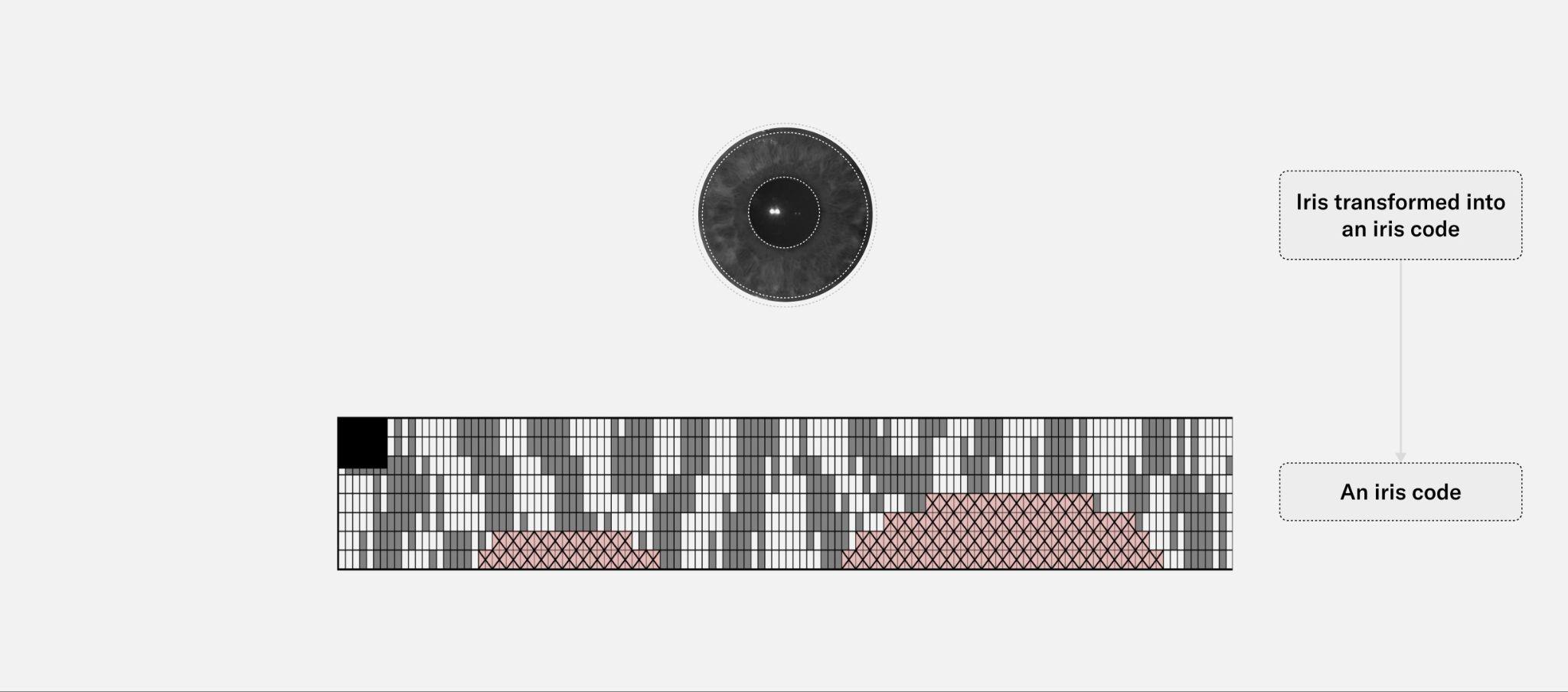
Fig. 3.37: An example iris code. In red, a second array can be seen that represents the mask applied to the image, these are pixels of the image that don't represent part of the iris texture, like eyelids, which are of course ignored when computing the Hamming distance between irises.
To date, there is no known way to reverse engineer an image that exactly matches the appearance of the input image. It is technically possible to generate an image from an iris code that generates the same iris code (if the same parameters for the Gabor wavelets are used, which are different for every system), but the image will look different from the actual image, mainly because of the information loss when generating the iris code.
Two important privacy assumptions ought to be underscored. First, private keys need to remain private, as otherwise, a user can deanonymize themselves, even to actions they have performed in the past. Second, while the Protocol is made to be used in a privacy-preserving manner, privacy cannot be enforced outside of the Protocol.
Wallets
While currently users must first download the World App to participate in World Network, the World Foundation aims for the development of other applications that support the creation of a World ID wallet. Afterall, the overall system is designed so that other developers can build their own clients without permission, meaning World App will hopefully be just one of the many wallets supporting World ID. Research is currently underway to develop SDKs for other wallets to support World ID.
Footnotes
-
Also evaluated were private information retrieval (PIR) protocols, but even with state-of-the-art protocols like OnionPIR and further optimizations, the services would need 10 seconds of multi-core compute per request. Multi-party computation (MPC)-based PIRs would perform much better, but they offer no anonymization advantage over using an MPC-based anonymization network. ↩
-
Note there’s a trust assumption on obtaining the inclusion proof from an indexing service as the user needs to provide their identity commitment to obtain an inclusion proof. Further decentralization of the indexing service is being explored. ↩
-
It is sufficient to check uniqueness on a per-context basis, but the nullifiers should be globally unique values. ↩
-
In this context, credential is used as a generic term to refer to a set of data about a subject, and in this case attested by a third-party (called issuer). ↩
-
ZKML would allow the iris code to be recalculated in the event of a model upgrade, without users needing to go back to an Orb. ↩
-
In this, issuer is the party who attests to a set of data about a subject. For example, Tools for Humanity is the issuer of the Orb credential. ↩
-
This is in addition to the decentralization introduced by the distribution of Orb manufacturing and operations across different entities. ↩
Advancing Decentralization
Introduction
World is a protocol, not a company. This makes decentralization an axiomatic end goal.
If World is to become critical, global-scale infrastructure, it must not—and cannot —be controlled by a single organization or small number of contributors. In that case, the political and economic pressures placed on any single entity would likely be too high: the network would either be corrupted or collapse entirely.
By contrast, decentralization of the World protocol so that it is sustained by a community with dozens, hundreds, or even more independent organizations that use and support the protocol, will enable the network to scale to billions of people while increasing utility and preventing fraud.
In the blockchain community, decentralization often refers to core infrastructure properties like transparency, verifiability, and permissionless access—conferring the network the ability to recover from local participant failures. Additionally, decentralization requires many independent participants to have a sustainable economic interest (e.g. a stake) in maintaining the infrastructure. Those properties are all important for World to function as a true public good. They are also important for adoption and continuous improvement of the protocol by application developers building on the protocol. Without them, the network cannot scale and it cannot be sustainable—that means failing its promise of becoming a trusted, global utility.
Because World is a complex system with multiple technologies that operate together, World Foundation has defined a series of critical use cases and tests to evaluate the stage of decentralization that has been achieved for those use cases.
This whitepaper explores avenues for decentralization of various components of World protocol, including software, hardware and governance.
Basic World Protocol Glossary
The Orb: The Orb is a verification device which takes pictures of a person, uses on-device analysis to determine that the person is a real, live human, and generates a privacy-preserving enrollment code that can be used to determine if they’ve previously enrolled—and therefore, whether they are unique. This enables the creation of a “Proof of Human,” perhaps the most important new property enabled by the World Protocol.
Relying Party: At its core, the World protocol allows applications to request a user-generated proof (such as Proof of Human, to confirm that they are a verified, unique human). The application requesting a proof is known as the “Relying Party.” The Relying Party is often an application on the user’s phone, a web application, or a smart contract.
World ID : World ID is a privacy-preserving digital ID. Discrete, unlinkable statements about the user can be generated with a secret value held only by the user—these are known as “Proofs”. Proof of Human, as an example, ensures that each human can only have a single “Verified World ID”. The World ID can also be used with other credentials to produce other proofs, such as Proof of Age, or Proof of Citizenship. An important property of the World ID is that proofs provided to two different Relying Parties cannot be linked together unless the user wants to do so.
Credential and Credential Issuer: World ID Proofs are generated using information from a credential. Every credential is produced and cryptographically signed by an issuer. For example, the World Foundation authorizes Orbs to produce the credential that is central to generating the Proof of Human, so the Orb credentials and Proof of Human are issued by the World Foundation.
Authenticator: The “World ID Authenticator” is software authorized by the user to generate World ID proofs. The authenticator may be a single purpose application, but it is more often provided as part of a larger application with other functionality. For example, the World App includes a World ID Authenticator while also bundling financial products and a mini-app ecosystem that extends functionality. Users may have multiple authenticators.
User Agent: Where the authenticator is bundled with other application functionality, it may be referred to as a User Agent. These User Agents may support a wide set of capabilities, as with the previously mentioned World App, or they may be an application with a specific purpose (for example, an application accessing a specific social media service, a gaming client, or an application to purchase concert tickets). User Agents may not necessarily run on a device that is controlled by the user – for example, “AI User Agents” are likely to run on infrastructure provided by an AI provider. As AI capabilities advance, we expect that humans may want to delegate the use of their World ID for certain purposes by providing the AI Agent with an Authenticator.
WLD / Worldcoin: A token governed by the World Foundation that will be used to pay for fees in the World Network such as the World ID Fees.
Tests to Evaluate Technical Decentralization
Progress in decentralizing the protocol can be measured with three major test cases:
- Test 1 – Permissionless Market Launch: Any operator can introduce the protocol to users in a new market without any dependency on any one (other) party.
- Test 2 – Protocol Use by Relying Party: Any relying party can use the protocol without dependency on any one (other) party.
- Test 3 – Enhancing the Protocol by Issuer: Any issuer can enhance the protocol with new credentials and proofs (including uniqueness modalities) without dependency on any one (other) party.
To further quantify progress, we defined decentralization stages for each of these test cases.
Test 1: Permissionless Market Launch
Much of the global population lives in areas that World Foundation and its existing contributors, such as Tools for Humanity (TFH), cannot directly service due to isolation, regulatory complexity, or mistrust. To allow these people to use the protocol, other parties must be able to provide access without needing World Foundation’s support or permission.
The use case: An individual within a new market should be able to go through the verification process (install a World Network-enabled wallet application, verify at an Orb) and then provide proof of human (PoH) without receiving World Foundation’s permission or using any technology controlled by World Foundation.
- Current: World Foundation governs the development and operation of PoH verification devices (Orbs) and wallets. These wallets use World Foundation authorized or managed backend systems.
- Stage 1: World Foundation-managed operation of verification devices will transition to Independent, arms-length operations using TFH/World Foundation front/backend systems.
- Stage 2: Stage 1 is achieved, and independent operations can be conducted without direct reliance on World Foundation managed or operated backend systems.
- Stage 3: Stage 2 is achieved, and there are multiple World-enabled wallets that can request WLD airdrops from World Foundation.
- Stage 4: Both Orb and wallet are provided by multiple parties. Airdrops are managed via smart contracts that are immutable or under decentralized governance.
Achieving Stage 4 will require technical changes to the World protocol, operations and governance. Some of these changes are already underway.
Test 2: Protocol Use by a Relying Party
Many enterprises and large applications hesitate to adopt a protocol that requires third-party permission, especially when long-term business interests may not align.
The use case: Any application or service provider that would like to leverage World Network and proof of human as a relying party should be able to deploy all parts of the technology stack for user enrollment, credential issuance and management, and proof verification without permission from or support of World Foundation (or any other third party). People who have a verified proof of human—originally issued for one relying party—should also be able to use the credential with other relying parties, such as the WLD airdrop highlighted in Test 1.
- Current: To prevent phishing and namespace collisions, applications and Mini Apps require a developer account overseen by Tools for Humanity. Users must have World App installed and use a World Foundation-authorized Orb to verify and generate their Proof of Human.
- Stage 1: Using a decentralized mechanism, developers can release apps that can request proofs from World App without needing a developer account or reduced trust.
- Stage 2: Stage 1 is achieved, multiple User Agents with World ID capable authenticators are connected to the World Network, including ones that are not developed by TFH or World Foundation. So a relying party can request and/or generate proofs without use of any User Agent managed by World Foundation or TFH.
- Stage 3: Stage 2 is achieved, and a relying party can deploy their full use case from user enrollment to credential issuance, proof generation and verification by the relying party without any dependency on World Foundation-managed technology or infrastructure.
- Stage 4: Stage 3 is achieved, and World Foundation authorization or support are not required for interoperability. Relying parties can independently assess third-party World-enabled applications and verification devices to determine whether they are trustworthy.
Achieving Stage 4 will require technical changes to the World Network protocol, operations and governance. Some of these changes are already underway.
Test 3: Credential integration with the protocol
Today’s digital identity infrastructure is fragmented and inefficient. Many discussions with potential relying parties (e.g., governments, identity companies, hardware manufacturers, etc.) are about enhancing the protocol to connect World Network to existing identity infrastructure and systems. World Network can provide a global, privacy-preserving way for users to manage and present credentials when using digital services online. Currently, only World Foundation and Tools for Humanity (via World App) can create a new credential that integrates with World ID.
The use case: Any credential provider can offer a new credential that can be integrated with World ID to be presented by the World ID user directly to relying parties or through privacy-preserving zero-knowledge proof (ZKP) attestations. This requires no permission from World Foundation (or any other party), and relying parties are able to use these credentials to enhance their services.
This enables the existence of a rich ecosystem of potential third-party credentials and proofs that can enhance the protocol.
- Current: Multiple credentials (Orb, NFC-enabled identity document, and device uniqueness) exist within World App.
- Stage 1: Credential formats are publicly documented. New credentials and ZKP attestations can be added by third parties with permission of World Foundation.
- Stage 2: User-controlled API for managing 3rd party credentials/attestations in World App (and other authenticators).
- Stage 3: Third-party unique credentials can be permissionlessly introduced using AMPC-based uniqueness services.
- Stage 4: World ID fees are deployed: relying parties pay credential issuers and the protocol to create a sustainable economic model for the protocol.
Achieving Stage 4 will require technical changes to the World Network protocol, operations and governance. Some of these changes are already underway.
Technical Roadmap for Decentralization
The following sections outline several different areas of World—User Agents (e.g., World App), verification hardware (e.g., Orbs), hardware operations, protocol, and governance—and how they can be improved through decentralization. The optimal mechanisms to increase decentralization may evolve over time, and suggestions for improvements are welcome.
User Agent
World App was the first application designed to work with the World Network, and it consists of three primary components:
- An authenticator that manages the user’s identity on the network and provides proofs to relying parties.
- A self-custody wallet that provides access to the financial functionality within World App.
- A miniapp platform that allows Third-Party applications to be deployed within the World App.
World App was launched as the first user agent to support World Network, enabling people to verify their World ID at an Orb and interact with relying parties. World ID is already available through the IDkit and Minikit (see developer portal), so any developer who wants to use Sybil protection in their application can connect to World Network via World App.
While currently users must first download World App to interact with the World Network, World Foundation is encouraging the development of other applications that connect to World Network. These applications are called User Agents, and, like World App, they connect to the network as an authenticator. World Network is designed so that any developer will be able to build their own user agent without requiring permission from World Foundation or any other contributor to the World project.
Research is currently underway to develop Authenticator SDKs that will make it easy for any application to connect directly to World Network while still serving the high level of privacy and security required by relying parties. This gives the user more choice of which user agent to use.
Enabling Decentralized Trust
There should be multiple user agents for people to choose from at the time of verification at an Orb, or when using World ID to provide a proof to a relying party. To enable a diverse range of trustworthy user agents, Tools for Humanity is currently working to improve the following components:
Integrity Services
Relying parties must be able to evaluate the authenticator environment that provides World ID proofs to determine whether they can trust the integrity of the provided proof. The World ID zero-knowledge proof itself is independent of the authenticator, however, additional security features (e.g., World ID Face Auth) require verifying the integrity of the User Agent and its authenticator. This is the result of privacy requirements which encourage local computation on the user’s phone. While local computation could potentially be secured through zero-knowledge proofs and the Orb’s image is signed, additional credential sources (including objects like a second input image taken through the user phone’s camera) may not maintain a similar level of data integrity. Until manufacturers begin attaching hardware attestations to those images, comparison to an image from the phone’s camera fully relies on trusting the integrity of the phone’s hardware and software. Thankfully, OS-level attestations already exist on an app level (e.g., Apple App Attest or Google Play Integrity) and can be used as a lower level integrity assurance signal. The verification of those can be handled by services that sign off on individual requests and enhance trust.
World ID Authenticator Kit (previously referred to as Wallet Kit)
World App already contains all the logic for handling an Orb verification and using World ID to generate and submit proofs (such as when receiving WLD grants). This process can be made simpler and quicker for new teams building their own applications. Authenticator Kit will handle the connection with the Orb and establish the privileged execution environment on the phone through the integrity services. Importantly, it should also contain a mobile-optimized proof-generation library.
Verification Devices
In the context of World, specialized verification devices (Orbs) enable the verification of humanness and the issuance of World IDs. There are several ways to make Orbs more transparent, verifiable and accessible. Increasing transparency and verifiability of the Orb’s functionality can help align the incentives of manufacturers not to be malicious. Furthermore, letting anyone develop alternative Orbs democratizes the solution space and accelerates decentralization.
The following sections walk through different milestones that can contribute to the robustness of Orb infrastructure.
Core Orb Engineering open source
To allow Orb functionality to be verifiable by the public and enable anyone to build their own Orb, the firmware and hardware have been made open source.
Hardware Source-Available
Today, hardware components that aren’t security critical (e.g., tamper detection and security board) have been made publicly available. Eventually, as much as possible should be made publicly available, but it is unclear whether publishing all Orb components is desirable given the security considerations described in the next section. There should be a continuous evaluation of which sensitive components can be made open source.
Core Firmware Components Are Open Source
Publishing core firmware components makes the functionality of the Orb more transparent and is a requirement to achieve verifiable Orb provenance and firmware. Therefore, a large part of the firmware of the Orb has been open-sourced.
Making these core components open source enables others to understand the functionality of the Orb in more detail and build alternative Orb firmware implementations. Potential vulnerabilities can be submitted through a public bounty program.
Given no hardware device can be perfectly secured, other sensitive components (like spoof-prevention algorithms and fraud models) that may pose a direct integrity or security risk to the ecosystem if exposed will likely not be made open source. Importantly, World doesn’t need to rely on perfect hardware security when complemented with mechanisms like auditing of Orb operations. To reduce trust requirements on non-open-source parts of the code, the open-source code defines software “sandboxes” for some closed-source components. For example, consider a closed-source fraud-detection module that ingests biometric data. The open-source code that interfaces with this module can provide strong evidence that the closed-source code cannot save/upload any biometric data.
Enabling Decentralized Trust
In a decentralized World Network, relying parties have access to the information they need in order to assess the trustworthiness of any credentials or proofs they verify. Orbs are one of the most important roots of trust for credentials in the network and must meet exceptional standards for trustworthiness. To ensure the integrity of the network and reduce trust in provisioning, Orbs should fulfill certain requirements (see Secure Provisioning Standard). However, no provably secure hardware exists, and certain points of trust remain as described in Orb Provenance Verification. Importantly, World Network doesn’t rely on perfectly secure hardware, and audit logging and in-person auditing of Orb locations can help decrease incentives for malicious actors.
The following technologies are currently being improved to help reduce trust assumptions; they provide relying parties and the broader community with the ability to evaluate the trustworthiness of any verification device.
On-chain Orb Registry
The “Orb Registry” refers to the set of active Orbs currently endorsed by World Foundation. If an entity’s process can be sufficiently trusted (e.g., by implementing a secure provisioning standard and conducting regular audits), the insertion of public keys from that entity in the Orb registry could be delegated to that entity. To limit the harm caused by a malicious Orb, World IDs registered with different Orb manufacturers (and ideally with different Orbs) should be distinguishable from each other. This makes it possible for the ecosystem to respond to (inevitable) attacks by removing individual Orb manufacturers, and perhaps even individual Orbs, from the whitelist on demand. Optionally, World IDs associated with fraudulent Orbs could be revoked. This information can be private and only stored on the World ID holder's device as long as it is provable on demand. If anyone were mistakenly affected by such action, they could re-verify through an active Orb. As a last resort, disagreement in the set of trusted provisioning entities could be resolved by forking the protocol and adding or removing provisioning entities.
Secure Provisioning Standard
“Secure provisioning” refers to the process of setting up the cryptographic keys of an Orb. One part of such a standard could, for example, specify that only certain approved secure element models can be used and require proofs of authenticity from each secure element (via die-unique certificates signed by the secure element vendor) to be reported alongside the public keys. Orbs generated by this process can then be considered securely provisioned.
Today, a secure provisioning process is in place that involves generating private keys on a secure element as well as burning secrets generated on an air-gapped machine connected to a hardware security module into private fuses (only accessible by TrustZone applets). These secrets are derived using a NIST-SP-800-108 KDF algorithm into two keys transmitted to the backend used for future device attestation, and then are immediately destroyed. The original key material only exists in the restricted fuse banks on the NVIDIA Jetson and within the secure element. Continual auditing of the process can help maintain a high security bar.
Auditing of Orb Operations
Auditing operations can help detect malicious operators and malicious Orbs, thereby disincentivizing malicious behavior. No entity in World Network should have to be trusted. Therefore, all operations need to be audited in a distributed manner.
One primary concern is someone being able to inject fake iris codes. In this case, “fraudulent” means the entity has a way to spoof requests to the uniqueness service to make them seem as if they came from a legitimate Orb. Security measures on the Orb should make such an attack very difficult. However, the risks associated with malicious individuals involved in provisioning and/or flaws in digital security can’t be entirely eliminated.
The auditing of Orb operations by incentivized users and dedicated auditing organizations, when combined with software- and hardware-security measures, can make generating fake IDs very hard. Today, operations are already audited by third-party organizations. To increase the robustness of this process, a list of all Orbs, their locations and operational information about the Orbs could be made public.
Incentivized Re-Verification
Similar to auditing of Orb operations, verified users can be incentivized to re-verify at a different Orb. For any attacker who compromised an Orb or spoofed verifications, such a second verification at a different Orb would be very difficult to also spoof. Therefore, statistically, the fraction of incentivized users that end up verifying a second time with a different Orb would be lower for a compromised Orb, allowing anomalies to be detected.
Orb Security Transparency
Below are steps toward making the security of the Orb more transparent:
Publish Audits
World Foundation regularly conducts and publishes hardware and firmware audits like this one to help ensure that the systems being built are as secure as possible, and to increase transparency into those systems. Such audits entail both security and privacy considerations.
Public Bug Bounty Program
A bounty program can raise the security bar by finding vulnerabilities early. In collaboration with Tools For Humanity and HackerOne, World launched a public bug bounty program in February, 2024. The program is being continuously extended with additional endpoints, source code and new categories of attacks.
Verifiable Orb Provenance and Firmware
While there is significant research involved, ideally, the public would be allowed to verify properties of an active Orb, including that it is:
- not counterfeit and is from an Orb vendor that meets manufacturing and security standards
- configured to only boot signed firmware
- running a specific version of the firmware
These verifications can help mitigate important privacy concerns related to biometrics. The public should not need to blindly trust an Orb vendor to faithfully/correctly implement privacy-preserving firmware.
Eventually, there may be a path to allow for firmware that hasn’t been approved by World Foundation governance, though it is unclear whether this would be desirable given the potential downsides. This would require appropriate incentive and audit mechanisms to disincentivize malicious behavior, which could turn out to be unviable in practice.
Orb Provenance Verification via User Agent
A first step towards verifying an Orb as non-counterfeit could be implemented through provenance verification via the user agent. Such a mechanism could help verify that an Orb is from a vendor that has been approved by World governance and therefore is running approved firmware. Such a feature can be integrated into other protocol-compatible apps.
One possible path for such a verification could be to ask the Orb to sign a challenge that has been generated by the App. Orbs contain two mechanisms for cryptographically attesting they are in the Orb registry: private keys in the secure element and private keys derived from fuses on the NVIDIA Jetson. Verifying signatures from both sources provides strong evidence that an Orb was manufactured by a vendor that has been approved and was not subsequently tampered with. Verification of the NVIDIA Jetson fuse state can provide strong evidence that Orbs can only boot firmware that has been signed. The user agent could also request an Orb’s firmware version from the Trusted Execution Environment’s (TEE) secure storage. As part of a normal boot, the root hash for dm-verity can be delivered to the bootloader by the TEE, ensuring that only code authorized by the TEE is able to boot. Inside of secure storage, these hashes would be associated with version numbers, allowing an entity (e.g., the World App) to request attestation of the current hashes and version numbers existing in the secure storage.
This mechanism assumes that an Orb’s private key only exists in its secure element (i.e., there are no other copies), a constraint which should be specified by the secure provisioning standard. Private keys are generated on the secure element directly and never leave, and a series of transparent certificate attestations during generation and export can prove that a particular key originated from a legitimate secure element. Therefore, physically attesting an Orb has a private key provides strong evidence that the same private key is not in the control of an attacker. Extracting private keys from the Orb’s secure element is assumed to be extremely difficult.
It is important to note that it is impossible to fully eliminate attack vectors of Orb hardware vendors/manufacturers or upstream vendors. The following attack vectors remain:
- The Orb vendor could bypass parts of the secure provisioning process (due to malice or incompetence), invalidating the guarantees of the proposed verifications. Therefore, Orb manufacturers should be audited to ensure the secure provisioning standard is maintained, and World Foundation is sponsoring research on other ways to harden the software supply chain..
- NVIDIA firmware could have security vulnerabilities or backdoors, which could threaten the Jetson fuse attestation.
- The secure element vendor could be compromised/incompetent/malicious, which would threaten the integrity of the corresponding attestation.
- The World Foundation could sign malicious firmware. Hardware support for firmware verification helps enable procedures to verify the actual firmware running on an Orb.
Therefore, there should be mechanisms to mitigate the risk of fraudulent manufacturers or compromised Orbs. In-person auditing of Orb locations and incentivized re-verification can make exploiting backdoors significantly harder and help detect malicious verification of World IDs in retrospect.
Reproducible Builds
Without reproducible builds, the public is required to trust that compiled firmware wasn’t maliciously modified during/after the build. Reproducible builds provide a mechanism to verify that Orb firmware was compiled from a specific state of the public repositories. To verify the integrity of the firmware, third parties should be able to build it from source on their own infrastructure. Full reproducibility means the resulting artifacts should be identical to those deployed to Orbs, and the signature from the signed firmware should be valid for the self-built firmware. The initial priority should be to make privacy-sensitive components of the firmware open source and reproducibly built.
However, there are some limitations. The firmware should (at least initially) include closed-source components, which are opaque parts of the system. Some of these are from Tools for Humanity (e.g., spoof-detection models) and some are from vendors (e.g., NVIDIA firmware components). Additionally, some components may be hard to make reproducible. These can be built separately and pulled in as compiled components to the main build.
Hardware Support for Firmware Verification
The most transparent way to verify firmware is by having read access to the storage of the main computing unit. The new generation Orb has a removable SD card that is easily accessible from the outside, and no persistent storage. Public auditors can use this mechanism to verify the integrity of a particular Orb’s firmware. The integrity verification of the dumped memory could optionally reuse the Orb’s internal integrity verification mechanism (dm-verity). This can provide stronger guarantees than Orb provenance verification via user agent, as there are fewer attack surfaces for spoofing direct physical access relative to remote attestation schemes.
While this mechanism provides strong guarantees for the firmware state, it is still possible to spoof the auditor at the hardware level. For example, there could be a second hidden flash chip that the Orb is actually booting from. This risk could be mitigated by additional audits that inspect the hardware directly on a random subset of devices. Further, in-person audits of Orb locations can make attacks significantly easier to detect and can create disincentives for malicious behavior.
Operations
Operations, in the context of World, refers to procedures in the “analog world” that allow people to get their World ID verified. The primary participants are Orb operators (i.e., independent entrepreneurs and their organizations around the world) who provide Orbs in physical locations for people to verify. Currently, all Orb operators have a commercial relationship with World Foundation. In the future, we expect that Orb operators will be able to acquire, deploy and manage operations without permission from World Foundation or any other entity. Certain infrastructure primitives can help reduce trust assumptions and align the incentives of all participants.
Community Operators
In 2025, Tools for Humanity (TFH) expects to provide the general public with the ability to become an Orb operator. They should be able to acquire an Orb and use it as part of a standalone operation to extend the protocol (as described in Test 1) or to develop a new use case (as described in Test 2). These new operators will complement the existing World Spaces and flagship operations that are overseen by TFH and other partners of World Foundation.
Protocol
The protocol contains off- and on-chain components that are responsible for handling, for example, verification or authentication requests from users. Since privacy is central to World ID, it is especially important to not sacrifice it in favor of accelerated increases in transparency, verifiability and resilience. One example of this is the uniqueness service, which still requires more research before it can be made more permissionless.
The following sections describe possible improvements to further increase transparency, verifiability and robustness of the protocol:
Protocol Open-Source
All of the components of the protocol are already open source (see the open source tree).
Protocol Security Transparent
Over the course of several months beginning in April 2023 prior to World’s public launch, audit firms Nethermind and Least Authority conducted two separate security assessments on the off-chain and on-chain components of World Network, including the following parts of the protocol:
- Correctness of the implementation, including cryptographic constructions and primitives and appropriate use of smart contract constructs
- Common and case-specific implementation errors
- Adversarial actions and other attacks on the code
- Secure key storage and proper management of encryption and signing keys
- Exposure of any critical information during user interactions
- Resistance to DDoS (distributed denial of service) and similar attacks
- Vulnerabilities in the code leading to adversarial actions and other attacks
- Protection against malicious attacks and other methods of exploitation
- Performance problems or other potential impacts on performance
- Data privacy, data leaking and information integrity
- Inappropriate permissions, privilege escalation and excess authority
Of the issues detected by Nethermind, which performed a comprehensive audit of World’s smart contracts, 92.6% were identified as fixed after the re-audit stage, while 3.7% were mitigated and 3.7% were acknowledged.
Details of these audits can be found in the Nethermind and Least Authority reports.
Since its launch, the World Protocol has continually evolved, with audits performed whenever sensitive or complex updates are introduced. For example, the uniqueness service, now based on an SMPC protocol, has undergone multiple audits from Least Authority which can be found here, here, and here.
Publicly Available Merkle Tree
The set of World ID public keys is already publicly available and committed to by the sequencer on Ethereum. The public keys are available as calldata, and the current state of the Merkle tree is committed as a Merkle root. Its validity is enforced through a ZK validity proof of batch insertions of public keys. While this ensures that the committed root actually corresponds to a Merkle tree, it’s not yet ensured in the validity proof that the public keys actually originate from an Orb. Even though the leaves are publicly available, it’s practically infeasible for the client to download all of this data and reconstruct the tree to be able to compute a Merkle inclusion proof. The tree availability service serves those Merkle inclusion proofs to clients. Clients can check the correctness of the Merkle proof against the on-chain root. However, this request can leak additional metadata about the client (e.g., IP address). This can be addressed by routing those requests through mixnets or through private information retrieval.
Permissionless Merkle Tree
As mentioned above, the validity proof of the Merkle tree needs to be enriched by a signature check of the public key. Once this check is added, trust in the identity sequencer is no longer required. Similar to the uniqueness service, this sequencer also needs to actually implement coordination to rotate between multiple sequencers so there is no possibility of censorship.
World ID Fees
The World Foundation is extending the World ID protocol to introduce World ID fees, payable in WLD. Usage will remain free for end users while applications will be charged for using World ID services. Each credential issuer will be able to set and retain their own credential fee, while a separate protocol fee will flow back to the protocol itself. More details were provided in a blog post on April 30, 2025 and technical specifications are expected to be released in 2025.
Decentralized Trust: Attestation and Auditability
Tools for Humanity and World Foundation are currently working to provide an update to the protocol that incorporates hardware and software security attributes (e.g., “attestations”) that allow for a decentralized trust model for authenticators, verification devices (Orbs), uniqueness services and relying parties. This will be released as open source and as a public standard that can be used by any third party to build or deploy infrastructure on the network.
Decentralization of Uniqueness Service
Increasing the resilience of the uniqueness service is challenging because a permissionless operation of the service would require iris codes to be public. A permissioned set of nodes that run the computation and agree on the result through consensus—or run the comparison on a reduced version of the iris codes so that no node has the full code—improves the verifiability of the system. As of 2024, such a system (known as AMPC) has been introduced.
AMPC
AMPC, or anonymized multi-party computation, is a quantum secure multi-party computation (SMPC) setup that anonymizes and securely protects the iris codes of Orb-verified World ID holders. It leverages NVIDIA H100 GPUs as the main compute platform to enable up to 50 million pairwise uniqueness comparisons per second.
AMPC incorporates the latest advances in cryptographic multiparty protocols and further improves on state-of-the-art techniques. This ensures that no iris codes ever leave the user's device. Instead, iris data is cryptographically processed directly on the Orb and rendered anonymous. Only anonymous data, which are secret shared and end-to-end encrypted, are transmitted separately to each compute node of the AMPC setup.
AMPC improves the way similarity comparisons are handled. In the previous version, pairwise Hamming distances were used in plaintext to determine the outcome of the enrollment process. In AMPC, only a binary result is revealed: whether the user is a match or not. This approach improves privacy even further.
In addition, iris masks, which are used to filter out noise and highlight relevant features of the iris for the uniqueness check, are now also secret shared, ensuring that they never exist in plaintext at any stage. This eliminates another piece of information and further enhances privacy protections for users. The architecture allows users' biometrics to remain secure, private and anonymous throughout the entire process.

Leveraging high-end hardware for superior performance
To achieve the high throughput required for global-scale biometric verification, AMPC leverages GPUs as the main compute platform. The AMPC protocol has been fully implemented using NVIDIA CUDA, enabling approximately 50 million pairwise comparisons per second overall.
Each compute node consists of an AWS p5.48xlarge instance with eight NVIDIA H100 GPUs. These instances provide around 3200 Gbps of bandwidth through Remote Direct Memory Access (RDMA) and 20 exaflops of compute performance.
Not only the uniqueness check itself, but also the transition from SMPC to AMPC was designed with the highest security and privacy in mind. This migration process, which involves changes in how the underlying cryptographic secret sharing works, is fully SMPC-based itself, meaning that no biometric data is ever processed or exposed during the upgrade. This ensures that user privacy is maintained throughout the entire transition process.
A decentralized and transparent approach
AMPC marks an important step toward decentralization and transparency.
World Foundation has partnered with Friedrich-Alexander-Universität Erlangen-Nürnberg in Germany, UC Berkeley Center for Responsible Decentralized Intelligence (RDI) in the U.S, and Nethermind, a trusted and reputable blockchain and research engineering company to operate a Multiparty Computation Setup, in which the anonymized data will be stored.

Additionally, the Blockchain Center of the University of Zurich in Switzerland and the Korea Advanced Institute of Science & Technology (KAIST) have committed to assisting in advancing the secure storage of the anonymized data. This shift will help create a global and decentralized system, ensuring that no entity has access to biometric data.
To further enhance community oversight, a governance board has been established, which will include independent external domain experts. This board will coordinate and supervise updates, ensure accountability, and govern the onboarding of third parties to operate compute nodes in the AMPC setup.
Scaling for the future
The future roadmap for AMPC includes numerous improvements aimed at scaling the system for future growth. These also ultimately serve to reduce the compute requirements, making it easier for new third parties to join the network. Additionally, trusted execution environments are in development to minimize potential room for manipulation of those trusted AMPC parties.
Like its predecessor, AMPC is open source. Transparency is essential for building trust in privacy-preserving technologies. Anyone is invited to review, contribute and build upon the codebase.
Unprecedented privacy in biometric systems
AMPC is not only one of the largest SMPC-based systems in production but also breaks new ground by leveraging high-end GPUs to significantly increase performance. These technologies set a new standard for privacy, security and scalability—all while advancing the state of biometric verification.
For a detailed description of the techniques used in AMPC, please refer to the paper, Large-Scale MPC: Scaling Private Iris Code Uniqueness Checks to Millions of Users.
Governance
A global community of developers, individuals, economists and technologists conceived and made early contributions to World Network. The original idea started with co-founders Sam Altman, Alex Blania and Max Novendstern, who founded Tools for Humanity and assembled a team to begin developing the technology to support World.
Tools for Humanity is a technology company building for humans in the age of AI. . It is a Delaware (U.S.) corporation headquartered in San Francisco, California, with a wholly-owned subsidiary, Tools for Humanity GmbH, based in Germany. Tools for Humanity supported World’s multi-year beta testing phase, during which it developed the Orb and the World App.
Tools for Humanity and other early contributors are committed to providing every person on the planet access to the global economy, regardless of country or background.
Today, the governance of World is overseen by World Foundation, an independent entity that is committed to transitioning World governance to all of humanity. It is important that this happens in a deliberate way. Therefore, governance (e.g., voting) must be well-studied and tested before this transition.
The following sections describe different improvements that are either already occurring or can contribute to this objective:
World Foundation Setup
On October 31st, 2022, World Foundation was established as the non-profit steward of World, supporting and growing the ecosystem as it becomes self-sufficient. The Foundation’s main objective is to scale an inclusive identity and financial network as a public utility and to expand the governance thereof. This infrastructure has the potential to empower everyone to participate in the global economy in the age of AI.
The Foundation is an exempted limited guarantee foundation company, which is a type of non-profit incorporated in the Cayman Islands. It has a wholly owned business company subsidiary in the British Virgin Islands called World Assets Limited. This is “one of the most often used, and internationally recognized structures” for decentralized blockchain projects.1 World Foundation is “memberless”; it has no owners or shareholders.
This entity setup was a good fit for World due to the Foundation’s separate personhood, limited liability, tax efficiency, support for compliance with virtual asset regulations and suitability for long-term community governance. That last point is especially important. Cayman foundation companies can be structured to be “memberless” (that is, have no owners or shareholders) and instead to take instructions from token holders and/or World ID holders. They can therefore gradually steer matters such as running a grant program, open sourcing intellectual property (IP), entering into service agreements and managing a treasury. In the case of World, the shared governance model is all the more critical so that, in the long term, decisions can reside with the community.
At the same time, the Foundation can aid the community’s governance by safeguarding protocol IP. In most legal systems today, a traditional legal entity is needed to protect IP such as trademarks, open-source copyrights and domains. Tools for Humanity has already transferred core protocol IP to the Foundation, including smart contracts, the World ID SDK, patents for the Orb design and iris recognition technology, brand assets, domains and social media accounts. And the Foundation has open-sourced several core tech repositories and made the Orb’s hardware available under its Responsible Use License.
Transfer of Control and Ownership to the Foundation
In order to facilitate future governance models, several assets and key components have been transitioned to World Foundation:
- Treasury: World Foundation (and/or its affiliate entities) manages the treasury of tokens once they are unlocked. This includes World grants, operator rewards, and other contributor grants.
- Orb IP: Tools for Humanity has transferred the Orb IP to World Foundation. The Orb hardware and software will be made publicly available under a restricted use license, prohibiting the misuse of the technology. This allows the Foundation to onboard other organizations building Orbs or similar devices.
- Ability to Whitelist Orb Provisioning Entities: The Foundation manages the permissions for adding Orbs to the network, balancing hardware distribution, security and growth.
In order to grow the network and ultimately enable all of humanity to participate in the governance of World, the issuance of World ID and allocation of the WLD token (in certain countries) is ongoing.
Support Future Development
To encourage individuals and organizations to contribute to World Network through research, the development and production of Orbs or auditing of the system, World Foundation is setting up a grants program. Further, the World Improvement Proposals process is currently being created and will be open for proposals soon.
Separately, the Foundation intends to work on common standards and ecosystem-wide proposals. For example, today, Orbs are developed and produced by Tools for Humanity. Orb operations are managed by several organizations around the world. With support from Tools for Humanity, the Foundation will work on standards and incentives for organizations to develop, produce and operate Orbs such that production of Orbs and their operation can be further distributed. More details can be found in the Orb whitepaper.
Initial Community
World maintains a dynamic and evolving blueprint that is subject to change and refinement through input and decisions from the World community.
To enhance transparency and facilitate community involvement, regular community calls should be established with the aim of providing a platform for open dialogue and updates on World’s progress. Additionally, a dedicated forum similar to ethresearch should be set up to further foster meaningful discourse and engagement around World. This forum can serve as a hub for ideas, suggestions and discussions among community members and the project team. Lastly, the Foundation has already hosted several developer meetups and strives to create more opportunities for developers to collaborate, innovate and contribute to World.
Decisions by Community
Increasing the resilience of the governance of World Network is both imperative and unprecedented, given the foundational nature of proof-of-personhood infrastructure and the ambition to scale it to billions of people. Building a community-based governance system for World represents perhaps the most formidable challenge of the entire project, and this process is still in its earliest stages.
The Foundation should ultimately have a limited role in the protocol’s governance. To this end, the Foundation’s founding documents have provisions for community-driven governance. These provisions make it possible, through a prescribed process, for the community to make recommendations to the Foundation’s board of directors. For further details, see the Foundation’s Memorandum of Association and Articles of Association.
World ID provides unique infrastructure for distributed governance and presents the opportunity to harness input from a large and diverse set of individuals for community-driven governance. The reach of World ID is unprecedented. As a proof-of-personhood protocol, World ID naturally supports “one-person-one-vote” voting, in contrast to token-based voting commonly used by other blockchain projects. Notably, this adds more democratic options to the design space of voting mechanisms for World. However, the exact structure of delegating decisions to the community needs careful iteration and consultation with experts. Further, many governance decisions notoriously lack engagement from participants. Therefore, it will be important to encourage a large set of people to participate and explore the decisions. In the future, the user agent should serve as an entry point for using World as well as the governance of it. Additionally, multi-stakeholder governance models akin to ICANN should be explored.
Full Handover to Community
World Foundation is committed to continuously transitioning governance toward a model that sustainably enables World to benefit all humanity. This is an unprecedented endeavor in scale and complexity for a decentralized system, which will require a methodical and gradual approach. Key aspects like voting mechanisms should be thoroughly researched, validated with experts and tested before meaningful control is transferred. Transparency, inclusivity and neutrality are essential. However, these attributes contribute to intricate governance structures like today’s democracies, which can lead to often slow and expensive decision-making. While this deliberateness is beneficial for making long-term strategic decisions, such as amending a constitution, it can hinder the ability to quickly adapt to new challenges during the initial growth phases. Hence, prematurely adopting a governance model that fully transitions governance to the community without a well-vetted plan is itself a failure mode to be avoided.
The Foundation seeks input from contributors, the community and experts in the field as it increases the robustness of the governance of World Network
Other Resources
The World roadmap is a dynamic and evolving blueprint that is subject to change and refinement through input and decisions from the World community. Whether you are a developer, a user, an enthusiast or simply someone interested in the future of decentralized systems, please reach out through the appropriate channel:
- Join the community discussion on X or Discord.
- Contribute to open-source repositories on GitHub.
- Visit the World ID Developer Docs and Portal.
- View live on-chain data on the Dune Dashboard.
- View the Decentralization and Open Source Roadmap.
Footnotes
-
To learn more about this arrangement, check out this Guide to the Cayman Islands Foundation Company from the Foundation’s outside counsel at the law firm Ogier. ↩
Worldcoin Tokenomics
Version:
Mission: Building a global identity and financial network
The mission of World is to build the world’s largest identity and financial network as a public utility, giving ownership to everyone. The project’s goals regarding the Worldcoin token, WLD, are as follows:
- The majority of WLD tokens will be claimed by individuals simply for being verified unique humans.
- The majority of humans alive today will claim WLD tokens, which may result in WLD becoming the most widely distributed digital currency.
- The WLD token, alongside World ID, will be used for protocol governance.
- The WLD token will form the basis of the largest anonymous identity and financial network.
Introducing WLD
WLD is designed as a cryptocurrency with governance properties, with the goal of eventually empowering users by giving them a say over the future of the protocol. Beyond conventional “one-token-one-vote” governance mechanisms, the introduction of World ID paves the way for “one-person-one-vote” mechanisms. These two mechanisms can be combined in many ways to enable new ways of governance. While World Foundation currently acts as the steward of the protocol, it plans to solicit proposals and interface with community-governance projects on how World ID and the WLD token should interact in World’s future governance model.
The community of users may determine the token’s utility for governance, but a few other use cases could emerge. For example, users may decide to use WLD within the World Network ecosystem to access features within World App or another wallet app, such as tipping, buying and selling goods, or signaling their support for causes or initiatives.
World Foundation is currently governing the project and is working toward progressively decentralizing governance and the ecosystem. The goal of decentralization will be aided by World Foundation’s unique approach of giving the majority of the WLD token supply to participants of World Network—simply for being humans.
The WLD Token
Launch Date | July 24, 2023 |
Network Information | Worldcoin (WLD) is an ERC-20 token on Ethereum Mainnet. |
Address: Ethereum | |
Address: World Chain | |
Address: Optimism | 0xdC6fF44d5d932Cbd77B52E5612Ba0529DC6226F1 Between July 24, 2023, and October 17, 2024, Optimism was the main venue for access and use of WLD. While WLD remains available on Optimism, the main venue for access and use is now World Chain. |
Upgradability | None. No control, except inflation starting 15 years after token launch (see Inflation below). |
Token allocation entity | World Assets, Ltd., based in the British Virgin Islands. World Foundation is its sole member and director. |
Initial supply cap | 10B WLD tokens (also see Inflation below) |
Inflation | Any inflation of the WLD supply beyond the initial 10B token amount can only start, at the earliest, 15 years after launch (specifically, on July 24, 2038, 4am UTC). The rate of inflation is to be determined by protocol governance. The allocation of any newly-minted tokens is to also be decided by governance. The inflation cap, enforced by the WLD token smart contract, is 1.5% annually. The default inflation rate = 0%. |
Availability
Worldcoin tokens are not available to people or companies who are residents of, or are located, incorporated or have a registered agent in, the State of New York or certain other restricted territories. More details can be found in the Terms of Use, including additional restrictions on eligibility.
Safety reminder
Watch out for fake apps claiming to be associated with World, and platforms or third parties that may try to sell or provide you with fake WLD tokens! Ensure that whenever you are transacting in WLD that it has the correct token address listed above. If the WLD have been “bridged” to another chain that is not Ethereum, World Chain, or Optimism, make sure this bridged version is secure and can always be redeemed or bridged back for WLD on Ethereum, World Chain, or Optimism. World Foundation and its affiliates are not responsible for the creation, operation, or security of any bridges deployed by third parties, nor any WLD that is bridged through them.
Important User Information
Cryptocurrencies, tokens, and blockchain applications are highly risky. They are novel and rapidly-evolving technologies whose availability, usage, utility, value, and functionality is dependent on and affected by third party actors, market forces, regulatory environments, and emergent or changing technologies and behaviors. These factors create significant complexity and introduce new and unanticipated risks or consequences. WLD may never increase in value and/or utility, or it may lose all value and/or utility. For more information, visit www.world.org/risks.
WLD Token Allocation
The following figure shows the allocation of WLD’s total supply to the four high-level stakeholder groups. Note that, since launch, the token allocation has changed within the 25% of the TFH Investors + Team + TFH Reserve allocation of tokens. The 75% World Community tokens are unaffected by this.

The following table provides details on the token allocation.
Percentage | Category | Description |
75% | World Community | World Foundation governs the allocation of these tokens in line with its Articles of Association and a mandate to continue decentralizing governance of token management decision-making. Most of these tokens are allocated to users; some will be used for the ecosystem fund and network operations (details below). |
11.1% | Team | These tokens go to the TFH team and other service providers that took the steps to develop World. |
13.6% | TFH Investors | TFH investors provided funding that enabled TFH to support the multi-year pre-launch phase of World. |
0.3% | TFH Reserve | TFH retains a reserve of WLD tokens to address future needs of TFH. |
Unlocked Supply and Circulating Supply
This section discusses token lock-ups and how WLD comes into circulation. Here are two terms to understand:
- Circulating supply denotes the total amount of WLD tokens that are freely circulating, meaning they do not have any specific transfer restrictions imposed upon them, and are not subject to the protocol’s governance discretion. This also includes tokens that could be acquired by external parties at any time, e.g., liquidity positions.
- Unlocked supply denotes the total amount of WLD tokens that are either part of the circulating supply or are unlocked but subject to the protocol’s governance discretion on their rate of release into the circulating supply.
Unlocked Supply Schedule
An important feature of the unlocked supply schedule is that (a) team and investor tokens are subject to lock-ups, while (b) tokens claimed by users are not locked up. The following figure shows the 15-year WLD token unlock schedule. Importantly, governance will determine the rate at which WLD tokens from the World community category are introduced into the circulating supply. This will depend on several factors, particularly the speed at which the number of World users grows. Thus, the unlocked supply represents an upper bound on the maximum circulating supply.

Note: For simplicity, the figure above assumes that the tokens contained in the TFH Reserve unlock according to, a one-year full lockup starting 2025-04-27 plus two years of linear unlock (see below). Given that these tokens are currently unassigned, they may be subject to additional lock-up periods and may unlock somewhat later than shown in the figure. A live version of the unlocked schedule can be found on Dune.
Below are details about the unlocked supply schedule for each category of recipient:
World Community Tokens
Ahead of launch, all 7.5B WLD tokens allocated to the World Community were minted. However, the vast majority of those tokens unlock over a 15-year span (details below). This unlock schedule constrains the pace at which these tokens can be made available for ecosystem participants. The unlock schedule of tokens is enforced by four smart contracts (1,2,3,4). Importantly, the tokens allocated to users and operators are not locked up.
The WLD token amounts shown in the following table unlock across the specified periods. During each period, an equal number of tokens are unlocked each calendar day.
Time Period | Amount of WLD Unlocked During Period | Cumulative WLD Unlocked at End of Period |
At Launch | 0.5B WLD | 0.5B WLD |
Launch – End of Year 3 | 3.5B WLD | 4B WLD |
Start of Year 4 – End of Year 6 | 1.75B WLD | 5.75B WLD |
Start of Year 7 – End of Year 9 | 0.875B WLD | 6.625B WLD |
Start of Year 10 – End of Year 15 | 0.875B WLD | 7.5B WLD |
Note: World aims to scale the network to every human. As the project grows, the number of people who are not part of the community necessarily becomes smaller. Given these dynamics, a substantial quantity of tokens are available for the World community within the first few years after launch, when the number of people who can join is highest and the rate of growth is the fastest. This is why 4B of the World Community tokens unlock over the initial three years. However, the rate at which these tokens enter the circulating supply depends on the speed of the network’s growth.
TFH Team and Investor Tokens
The tokens allocated to TFH investors were contractually fully locked up for 12 months after those investors exercised their respective token warrants (which they were able to do at launch). The team tokens had the same 12-months full lockup in place. After the full lockup period, approximately 80% of the TFH team and investor tokens started unlocking linearly over a 48-month period while approximately 20% unlock linearly over a 24-month period. Unlocking for nearly all of these tokens therefore concludes by the end of July 2028—five years after protocol launch. Originally, all unlock schedules were over 24 months, but they were extended to 48 months for the majority of tokens in July 2024. The World Foundation previously shared information about these unlocks (see here), as this very gradual unlock schedule is longer than that of many projects and aligns with the long-term nature of World’s mission. Note that team members’ tokens may additionally be constrained by vesting schedules, which have their own timelines, typically tied to a person’s tenure at TFH.
TFH Reserve
The tokens in the TFH Reserve are contractually locked up for at least one year of full lockup plus two years of linear unlock from the time they are allocated. The exact lock-up period will depend on when these tokens are allocated.
Circulating Supply at Launch
Figure 4.2 shows the amount of unlocked WLD tokens over time. This is different from circulating supply, which excludes unlocked WLD tokens that are held in the Foundation’s treasury but have not been allocated for any specific purpose.
The circulating supply of WLD primarily grows with network size and usage. At launch, there were about 2M humans who had verified and were allocated a total of 43M Beta WLD tokens during the pre-launch phase of the project. In line with World’s goal of creating a network of as many humans as possible, the circulating supply of WLD was quite low at 100.7M WLD (1% of total supply), consisting of the following parts:
-
700k WLD tokens had been migrated by users from the pre-launch phase at launch. The remaining 42.3M WLD from the pre-launch phase remained available for migration for a period of time after launch.
-
100M WLD tokens had been loaned to trading firms operating outside of the US.
Since launch, the circulating supply of WLD has grown steadily. As of April 28, 2025, it stands at about 1.3B WLD (i.e., 13% of total supply). See the dune dashboard for live numbers.
Foundation’s Token Allocation Goal
Until the protocol is self-sufficient, the World Foundation acts as the steward of the World Community tokens. As part of its role, the Foundation has allocated those tokens towards three purposes: (1) user tokens, (2) network operations, and (3) an ecosystem fund.
World’s evolution over time may be affected by a variety of factors, each of which could be significant. These factors include the number of Orbs deployed in the field, the number of new verifications per week, the activity of World’s users, the number and location of merchants, platforms, developers, and others seeking to utilize the functionalities of World, future governance decisions, and numerous other known and unknown factors. Therefore, the final allocation of the World Community tokens cannot yet be determined. Nonetheless, taking into account the project’s objectives and current scale, the World Foundation has formulated an aspirational token allocation goal, as shown in the following figure:

World Foundation seeks to maximize the number of WLD tokens allocated to users in line with the various factors that affect World Network’s growth. This may mean that the Foundation allocates fewer tokens to network operations and the ecosystem fund over time than shown in the above figure.
User Tokens (target allocation: ≥ 60%)
Worldcoin’s tokenomics is unique in that the majority of WLD tokens will be freely available to claim by individuals over time in the form of user tokens (previously known as “user grants” or the “WLD airdrop”). Individuals can claim these tokens simply for engaging in World Network and verifying their unique humanness. Because of this, the circulating supply of WLD primarily grows with network size and usage.
Given that equality is one of the project’s guiding values, there was not a large one-time airdrop at launch, as such an event would have likely resulted in tokens flowing to a small group of people. Instead, the availability of WLD tokens is based on the following three principles:
-
Unique humanness. Every verified unique human is eligible to claim user tokens (subject to the availability noted above).
-
Fairness. At any given point in time, all verified individuals, across all applicable countries, can claim the same amount of tokens (subject to availability).
-
Incentives: User tokens are given out over time, and the claimable user token amount decreases over time. This gives users an additional incentive to join the network early and to regularly engage with the protocol, thereby addressing the cold-start problem inherent to launching a new network.
The user tokens are not an investment. If you already have an eligible credential (see below) attached to your World ID, you may claim user tokens without providing anything of value to World as the claim is in and of itself a simple check (using zero-knowledge proofs) to determine that you are in fact eligible. No appreciation or receipt of value is guaranteed or implied–and you don’t have to claim user tokens at all to participate in World Network.
How users can claim WLD tokens
To be eligible to claim user tokens, a user needs to have a credential attached to their World ID that is recognized by the protocol for the claiming of user tokens. Currently, two credentials are recognized for this purpose. The first is the proof of human credential, which individuals obtain by verifying their uniqueness at an Orb; this automatically attaches the credential to their World ID. The second is the passport credential (or in some countries a government ID credential), which individuals can attach to their World ID by connecting their phone to a compatible NFC-enabled government issued ID, such as a passport. Note that these credentials may not be available in some jurisdictions.
Eligible individuals can then make a claim for the following two types of user token amounts via a compatible app, such as World App, by checking if their credential is in the protocol:
-
First User Token Amount: 24 hours after the credential is added, they can claim their first user token amount. As of August 1, 2025, the first user token amount is 25 WLD for the proof of human credential and 12.5 WLD for the passport credential. The amounts are expected to decrease over time.
-
Recurring User Token Amounts: Starting one month after the credential is added, individuals can claim their first recurring user token amount. Each recurring user token amount is available to claim for one month to every (eligible) individual in the world. Recurring user token amounts are the same for everyone at a given point in time but decrease over time. The recurring amount for August 2025 is 3.22 WLD for the proof of human credential and 1.61 WLD for the passport credential. The ability to claim recurring user token amounts does currently not expire, though governance could change that at a later time.
If the same individual has attached both the proof of human and the passport credential, they can claim both of the respective (first and recurring) user token amounts. For example, an individual who attaches both credentials in April 2025 can claim a total first user token amount of 25 + 12.5 = 37.5 WLD.
For a user who becomes eligible today, one can compute how much WLD they may be able to maximally claim over the following year. To do this, one fetches the first user token amount and the currently configured future recurring user token amounts for one year (see Technical Information) and sums them up. The Worldcoin Mini App in World App currently displays the result to the user as their total user token amount to abstract away the intricacies of the schedule of recurring amounts.
As of 2025-08-01, the future recurring user token amounts (as currently configured in the smart contract) are as follows. Note that governance may change these amounts.
Year | Month | Recurring user token amount, proof of human credential (WLD) | Recurring user token amount, passport credential (WLD) |
2025 | August | 3.22 | 1.61 |
2025 | September | 3.20 | 1.60 |
2025 | October | 3.18 | 1.59 |
2025 | November | 3.16 | 1.58 |
2025 | December | 3.14 | 1.57 |
2026 | January | 3.12 | 1.56 |
2026 | February | 2.68 | 1.43 |
2026 | March | 2.60 | 1.30 |
2026 | April | 2.34 | 1.17 |
2026 | May | 2.08 | 1.04 |
2026 | June | 1.82 | 0.91 |
2026 | July | 1.56 | 0.78 |
2026 | August | 1.36 | 0.68 |
Unclaimed WLD tokens remain in the World community pool. Importantly, “claim” refers to the process described above by which user token amounts are received and is not intended to create or imply any legal relationship between any individual and World Foundation or any other entity.
Governance over user token amounts. The user token amounts are set by the protocol’s governance. Currently, governance is implemented via World Foundation, but it is expected that over time, governance will be increasingly decentralized. This means that governance could also alter the emission mechanism for user tokens. For example, once the system has stabilized, governance may decide to automatically update the user token amounts according to some rule implemented in a smart contract.
Long-term sustainability of the user token emission. To achieve the goal of providing WLD tokens to every living human being (subject to availability and eligibility), governance may also decide to phase out the recurring user token amounts after a few years and only keep the first amount, thereby reserving the remaining tokens for new users in the future. As explained below, governance may also decide to direct a portion of the future fee revenue from World ID fees towards user tokens. Finally, as explained above, 15 years after launch, governance may also decide on enacting an inflation rate of up to 1.5% per year, if this is deemed necessary to continue the user token mechanism into the future.
Historical note: user token reservations for unverified individuals. For a period after launch, individuals were able to reserve user token amounts prior to verification and they would receive their reserved amounts once they verified at an Orb. Reservations have now been phased out and redemptions of these reservations close in July 2025.
Historical note: User token allocations during the pre-launch phase. During the pre-launch phase of World, which lasted from May 2021 until July 2023, Beta WLD tokens were allocated to users in different stages (subject to availability). Users were able to migrate their Beta WLD to WLD at or after launch.
The remainder of this section discusses the other categories in the Foundation’s token allocation goal.
Network Operation (target allocation: ≤ 10%)
A portion of the WLD token supply allocated to the World Community is intended to be used to fund network operations. This section describes the main operational costs for the network, though this list is not intended to be exhaustive. Where necessary, these costs may be covered by World Foundation converting a portion of WLD tokens allocated to network operation into fiat or other currency.
Areas and responsibilities for network operations. The World Foundation is the steward of the World project, supporting and growing the community. The World Foundation owns the IP for the World ID protocol, the Orb, World Chain, and the Worldcoin token protocol. The World Foundation also governs the 75% of all Worldcoin (WLD) tokens that have been allocated to the World Community. In line with the project goals, the Foundation is allocating part of these tokens towards network operations and ecosystem building.These include the operation of the World ID sign up sequencer and uniqueness services, entities supporting World Chain, user engagement, and community outreach.
Other areas of network operations are the responsibility of ecosystem contributors. These areas include Orb manufacturing and operations. One of these ecosystem contributors is Tools for Humanity (TFH), the initial development company that launched World Network.
The World Foundation plans to further decentralize network operations, for example, through additional service providers and decentralized structures that ensure the long-term sustainability of the operations of the network.
Orb Manufacturing
Part of the WLD token supply is used to fund ongoing manufacturing costs. To this end, World Foundation engages TFH to oversee manufacturing of the Orb. In the future, other service providers may also be engaged to manufacture the Orb or devices similar to the Orb.
Orb Operations
Orb Operators are independent ecosystem participants who operate the Orbs and receive Operator rewards for verifying individuals at the Orb. It is important that Operators provide users with a high-quality experience by educating them about the project and supporting them during the verification process. To align the Operators’ financial interests with the objectives of World, Operator rewards are impacted by measures of sign-up quality.
To ensure the long-term financial viability of World (given the Foundation’s long-term goal of deploying 50,000 Orbs), competitive mechanisms have been trialed to determine fair Operator rewards. This also encourages Operators to innovate and quickly adapt to the changing needs of the project. The vast majority of Operator rewards is paid in WLD tokens (subject to the availability noted above), while a small share is paid in USDC.
Other Operations
Part of the WLD token supply is used by World Foundation to fund other operational costs, which includes logistics associated with Orb deployment, production of equipment provided to Operators, etc.
Market Operations Support
Part of the WLD token supply will be used by World Foundation to fund market operations support, which includes the recruitment, training and coordination of the network of Operators around the world.
User Engagement Initiatives and Community Outreach
When launching in a new country or region, part of the WLD token supply can be used by World Foundation to fund user engagement initiatives and community outreach programs (e.g., partnering with local organizations).
Sequencer and Uniqueness Service Operation
When a person verifies with an Orb, the uniqueness of their biometric information needs to be verified, and the proof of uniqueness needs to be written to the blockchain. The corresponding service is operated by World Foundation. World Foundation also supports the operation of a sequencer for World Chain that writes the state of the World Chain to Ethereum. Part of the token supply is allocated toward covering the cost of these services.
Bug Bounty Programs
While the hardware and software have been extensively audited by external security auditing companies (see the Orb audit and protocol audits), additional bug bounty programs have been set up for the smart contracts and other software. These bug bounty programs may also function as tools for the progressive decentralization of the project.
Ecosystem Fund (target allocation: ≤ 5%)
The ecosystem fund is intended to be used by World Foundation to support activities for the continued development and decentralization of World. These costs are largely independent of the network size or the size of the on-the-ground operations.
Protocol R&D
Some funds are used by World Foundation for continued development of World and related software. This includes, for example, the development of the World ID protocol, World Chain, and may in the future include the development of client apps.
Orb R&D
Ecosystem funds are also used for continued research and development of Orb hardware and software, including security mechanisms and new features.
Standards Development, Audits, and Certification
Some funds are used by World Foundation to foster standardization of the different parts of World, including different wallet apps, the Orb and the on-chain protocol. Standards help decentralization by making it easier for different parties to become part of the network. In the future, some funds are expected to be used for audits (e.g., of new biometric devices or new wallet apps) and certifying new service providers.
Ecosystem Grants
Some funds are used for ecosystem grants, which are issued for the development of new protocols, systems and integrations that are part of World, as well as for additional research and development.
Incentive Programs
Some funds are used for programs that directly incentivize activities by persons, companies and protocols that contribute to the ecosystem’s growth.
Liquidity Provisioning
World Assets,, Ltd. entered into loan agreements with several trading firms operating outside of the US. These loans enable trading firms to independently assess and provide liquidity for WLD tokens.
As of 2025-04-28, these entities collectively hold loans worth 13M WLD. Out of this amount, 10M WLD expire on 2025-06-14, 1M WLD expire on 2025-09-26, and 2M WLD are currently not marked for expiry. The loans must be repaid in full in WLD – in particular, there is no call option.
World Foundation Operations
Part of the ecosystem fund will be used to fund a small staff working at World Foundation, along with associated operational costs (e.g., legal, administration).
World ID Fees
World ID is a protocol enabling a global, privacy-preserving identity network. At its core is the proof of human credential provided by the Orb. Additionally, the World ID protocol enables any entity (e.g., enterprises or governmental institutions) to create a new World ID Credential (e.g., a credit report or a university certificate), which individuals can attach to their World ID. Individuals can then share things about themselves without revealing their real identity. For example, Orb-verified individuals can prove to an application (aka a relying party) “I am a unique human”, while individuals who have added a passport credential can prove “I am over 18” or “I am a US citizen”. Credentials can also be combined to make composite proofs, for example “I am a unique human who is over 18”, without revealing any other information. Given the importance of knowing whether a credential (like the age credential) has only been used once for a given application, it is expected that most World ID proofs will include the proof of human credential in this way.
Applications that integrate World ID can request and use such proofs, for example, to avoid bot accounts, to prevent AI impersonation and fraud, or to implement age controls. Furthermore, AI Agents may soon require a technology like World ID for humans to delegate authority to agents.
As part of its mission, the World Foundation aims to progressively decentralize the ecosystem and make the project self-sufficient. In the context of the World ID protocol, this has two primary components:
-
Incentives for credential issuers: Enable credential issuers to generate sufficient revenue such that they are incentivized to issue and maintain their credentials.
-
Protocol sustainability: Generate sufficient revenue to make the protocol sustainable.
To this end, the Foundation is currently designing changes to the World ID protocol that will enable the option to charge fees, payable in WLD, to applications using World ID proofs.
Charging Applications, not Users
World ID fees will be charged to applications, not to end users. The motivation for this is that value creation is most directly measurable by the applications. The value of World ID is realized when applications integrate it to either enhance their existing services or enable entirely new services—potentially even spawning new business models previously impossible to implement. It is therefore natural for the protocol to charge applications for consuming World ID services. Applications are accustomed to paying for the components they integrate and can be expected to recognize the value World ID brings to their offerings. This approach ensures that a portion of the value created for applications flows back to the credential issuers and the protocol.
Details on World ID Fees
World ID fees will consist of two components:
-
Credential fee: Each credential issuer (e.g., the World Foundation for the Orb credential, enterprises or governmental institutions for their credentials) will be able to set a fee for their credential, and they will receive the corresponding fee revenue. This ensures that credential issuers have an incentive to create and maintain their credentials.
-
Protocol fee: The protocol will set a base fee and additionally charge a small premium on top of the credential fee. This will ensure that enough revenue is generated to make the protocol self-sufficient.
From an application’s perspective, there will only be one World ID fee – the sum of the credential fee and the protocol fee. The World ID fee will be charged when an application (identified via a unique app id) requests a World ID proof.
Fee payment will be enforced at the protocol level. This is one of the features enabled by the private state blockchain employed by the future World ID architecture (see here for a technical background on the underlying cryptography used). Informally speaking, a private state blockchain can update its internal state without anyone being able to observe it, while still being permissionless: anyone can operate a node, but certain state variables are only available within the computation of the private state blockchain itself, not observable in clear text outside of it.
Employing a private state blockchain will enable various features for the World ID protocol (e.g., World ID recovery and multi-wallet usage). Importantly, it will also store part of the application state belonging to each verified user. The World ID smart contract will programmatically check whether the fee has been paid before providing a receipt of the state change from the private state blockchain that enables the user to then generate the proof. In this way, using a private state blockchain also ensures that applications cannot circumvent World ID fees, as they cannot observe the state of the blockchain.

Figure 4.4 presents a high-level overview of the planned World ID fee implementation, using the example of a user who has already enrolled with a credential issuer and had their credential registered on the private state blockchain. World ID fees then work as follows: (1) An application that has integrated with World ID requests a proof (e.g., of unique humanness) from the user. (2) The user (via a World ID app like World App) decides to execute the request towards the World ID smart contract on the private state blockchain. (3) The smart contract automatically triggers the WLD fee payment from a wallet associated with the requesting application. (4) The corresponding credential fee is paid to the credential issuer wallet, and the protocol fee is paid to the protocol wallet. (5) The World ID smart contract updates its own state. (6) The World ID smart contract sends a receipt of the state change to the user. (7) The user’s app generates and sends the World ID proof to the application.
The World ID smart contract will require fees to be paid in WLD, meaning applications’ wallets on the private state blockchain must be pre-funded with WLD. Web3-native applications can directly pre-fund their wallet on the blockchain. Alternatively, applications (e.g., Web2 platforms) might use a third-party pre-funding service that handles the wallet pre-funding for them and charges the application in fiat. Either way, WLD tokens are ultimately used to pay all fees.
Pricing Mechanisms
Figure 4.4 implicitly assumes that World ID fees are paid for every World ID proof. In practice, each credential issuer will be able to choose any pricing mechanism compatible with the architecture shown in Figure 4.4. Because pricing mechanisms are implemented as smart contracts on the private state blockchain, a wide array of options becomes possible, including:
-
Per-proof: A fee could be charged for every World ID proof.
-
Per-monthly-active-user: A fee could be charged for every monthly active user (per app-id). For each user, the fee would be collected the first time a proof is requested for that user in a given month. Since the computation happens inside the private state blockchain, per-monthly-active-user pricing models can be implemented without revealing the identity of users.
-
Free tiers: The first 1000 users or the first 1000 proofs could be free.
-
Volume discounts: The per-user or per-proof fee could decrease with volume.
-
Discounts for specific applications: A credential issuer could offer discounts to specific applications (e.g., NGOs), or even offer their credentials for free.
-
Fees proportional to economic value: A credential issuer could offer multiple proof variants at different fee levels, with some variants intentionally providing a lower level of proof assurance, allowing applications to select the level that best fits their needs.
For the base fee component of the protocol fee, governance will similarly be able to decide on a suitable pricing mechanism. While several different pricing mechanisms are possible, it is likely that most applications will prefer a per-monthly-active-user fee, as it allows applications to compare that fee with the value that World ID generates for them per user per month (e.g., due to an increase in ARPU).
For composite proofs like “I am a unique human who is over 18 years old,” fee amounts could potentially depend on the combination of credentials required by a World ID proof. For example, the fee for a “uniqueness” proof could be lower than the fee for a “uniqueness + age” proof.
Fee usage
Each credential issuer will have discretion over how to use their credential fees. As for protocol fees, the World Foundation will initially govern their allocation. Over time, as governance becomes more decentralized, the World community will take over this responsibility. The community may choose to direct a portion of the fees toward continued network growth—for example, by supporting Operators or funding the User Tokens—or even decide to burn a share of the fees. As the World ID protocol grows (with more participants, more applications, and more proof verifications), more fees will be generated, which can then flow back into the ecosystem to create further growth, leading to a self-reinforcing growth mechanism.
Next steps on World ID Fees
The World Foundation is currently working on the protocol changes necessary to enable World ID fees. The Foundation expects to complete this work and run a first pilot to test the fee mechanism during Q3 2025. The Foundation believes that demonstrating a path towards World ID fees early on is important to incentivize other parties in the ecosystem to issue and maintain their credentials, and to show how the protocol can become self-sufficient.
While the Foundation prepares to launch World ID fees, its primary focus remains squarely on growing World Network. The Foundation will also continue providing ecosystem grants to support the community of mini app developers, credential issuers, and applications integrating with World ID.
Technical Information
Contracts and Addresses
Smart Contracts
Contract | Network | Address |
WLD Token Contract | Ethereum | |
WLD Token Contract | World Chain | |
WLD Token Contract | Optimism | |
Community Tokens Unlock Contracts | Ethereum | |
Recurring User Token Amounts Allocation Contract, Orb | World Chain | |
Optimism (deprecated) | ||
Recurring User Token Amounts Allocation Contract, Passport Credential | World Chain | |
First User Token Amounts Allocation Contract, Orb | World Chain | |
First User Token Amounts Allocation Contract, Passport Credential | World Chain | |
Beta WLD Token Contract (deprecated) | Optimism |
User token amounts can be fetched as follows: the currently active grant IDs and future recurring user token amounts can be fetched from the WLDGrant contract available at (Recurring User Token Amounts Allocation Contract).grant() where one chooses the Recurring User Token Amounts Allocation Contract corresponding to the respective credential (Orb or Passport). The current first user token amount can be fetched from API endpoint at: https://api.airdrop.world.org/v1/grants/first-claim-amount?grantId=<current grant id>
Main Wallets
Wallet | Network | Address |
World Foundation | Ethereum | |
Optimism | ||
World Chain | ||
World Assets, Ltd. | Ethereum | |
Optimism | ||
World Chain | ||
World Assets, Ltd. | Ethereum | |
World Chain | ||
World Assets, Ltd. Hot Wallet: Recurring User Token Amounts | World Chain | |
Optimism (deprecated) | ||
World Assets, Ltd. Hot Wallet: First User Token Amount | World Chain | |
World Assets, Ltd. Hot Wallet: Reservations | World Chain | |
WLD Vault | World Chain | |
Optimism (deprecated) | ||
Optimism – World Chain Migration | Optimism | |
World Chain | ||
World Assets, Ltd. Hot Wallet: Welcome Grants and Beta Token Migration (deprecated) | Optimism | |
World Assets, Ltd. Hot Wallet: | Optimism | |
World Assets, Ltd. Hot Wallet: | Optimism | |
Polygon Bridge | Optimism |
FAQ
How do the World Chain contracts relate to the Ethereum contracts?
The WLD token contract is deployed on Ethereum mainnet, and the token is bridged to the World Chain “layer 2” network. However, World Foundation expects that most of the activity in WLD tokens will happen on World Chain, where verified individuals receive their user token amounts. In addition, World App primarily interacts with the World Chain network. The reasons for choosing World Chain over Ethereum as the primary venue were scalability and transaction costs. A legacy bridged version of WLD also still exists on Optimism.
Who pays the transaction costs (gas fees)?
World App users generally do not currently incur gas costs; the gas fees for claiming WLD tokens, performing swaps, and other transactions are currently funded by TFH. In the future, World App could require users to pay gas fees for certain actions, e.g., transfers made to other wallets. When users verify their identity to a third-party application via World ID, this does not incur gas costs for the protocol. However, the third-party applications may charge users gas fees (depending on whether they verify the proof on-chain or off-chain) or other fees. For instance, when using the swap feature in World App, users do pay any fees incurred on third-party platforms. Users may incur gas fees for transactions that are not made through World App that are dependent on the platform and chain on which the transaction is occurring.
How are the World Community tokens stored? Do you use a custody provider?
The majority of the World Community tokens are stored in a cold wallet. Additionally, several hot wallets are used by World Foundation and World Assets, Ltd., to manage everyday operations. Tokens are typically only stored in these hot wallets for a short period of time, and these wallets only store as many tokens as needed.
Who controls the WLD token contract? Is it upgradable? Does anyone have minting rights?
The WLD token contract is not upgradable. No control can be exercised over the contract, except for setting the “minter” address in case the community decides to activate inflation. For 15 years following the launch, no address is able to mint any new tokens. After 15 years, a “minter” address (controlled by protocol governance) can mint up to 1.5% new WLD tokens per year, with governance deciding how to allocate them.
What are the involved entities and where are they incorporated?
The World Foundation is an exempted limited guarantee foundation company, incorporated in the Cayman Islands. It is “memberless,” meaning it has no shareholders or beneficial owners. Its registered office is located at Suite 3119, 9 Forum Lane, Camana Bay, George Town, Grand Cayman KY1-9006, Cayman Islands. World Foundation’s principal purpose, as set forth in its Articles of Association, is to support and encourage the growth of those building in the World ecosystem, support and foster the decentralization of World technologies and governance, hold and license intellectual property relating to the World Network, and to receive, sell, hold, loan, and spend assets to support these purposes.
World Assets, Ltd. is a company registered in the British Virgin Islands on December 7, 2022 with BVI Company Number 2113558. The World Foundation is the sole member/director of World Assets, Ltd. World Assets, Ltd.is responsible for issuing the 7.5B Worldcoin tokens (WLD) that have been allocated to the World community.
World Chain LLC is a limited liability company formed in the Cayman Islands. World Foundation is its sole member and manager. World Chain LLC is responsible for the ownership and operation of World Chain infrastructure.
More information about these entities, including incorporation documentation and equity composition, can be found at foundation.world.org/about.
Tools for Humanity (TFH) is a Delaware corporation headquartered in San Francisco, California (US), with a wholly-owned subsidiary, Tools for Humanity GmbH based in Germany. Its registered office is located at CSC 251 Little Falls Drive, Wilmington, Delaware 19808. It registered on June 26, 2019 and its legal entity number is 7487684. TFH supported World’s multi-year pre-launch phase, during which it developed the Orb, the first version of the protocol, and the World App, the first wallet for World Network, which it still operates today. It is governed entirely independently of World Foundation. Founded in 2019, TFH has grown to a team of approximately 500 people today. However, World is an open protocol that anyone can contribute to and build on.
Disclaimer
PLEASE READ THE ENTIRETY OF THIS “NOTICE AND DISCLAIMER” SECTION CAREFULLY. NOTHING HEREIN CONSTITUTES LEGAL, FINANCIAL, BUSINESS, INVESTMENT OR TAX ADVICE AND YOU SHOULD CONSULT YOUR OWN LEGAL, FINANCIAL, BUSINESS, INVESTMENT, TAX OR OTHER PROFESSIONAL ADVISOR(S) BEFORE ENGAGING IN ANY ACTIVITY IN CONNECTION HEREWITH. NEITHER THE WORLD FOUNDATION (THE FOUNDATION) AND ANY OF THE PROJECT PARTICIPANTS (TOGETHER WITH THE PROJECT PARTICIPANTS, THE WORLD NETWORK) WHO HAVE WORKED ON WORLD NETWORK (AS DESCRIBED HEREIN) OR DEVELOPERS OF WORLD NETWORK IN ANY CAPACITY WHATSOEVER, NOR ANY SERVICE PROVIDER SHALL BE LIABLE FOR ANY KIND OF DIRECT OR INDIRECT DAMAGE OR LOSS WHATSOEVER WHICH YOU MAY SUFFER IN CONNECTION WITH ACCESSING THIS WHITEPAPER, THE WEBSITE AT HTTPS:// WORLD.ORG (THE WEBSITE) OR ANY OTHER WEBSITES OR MATERIALS PUBLISHED BY THE FOUNDATION.
Crypto Products
Crypto products can be highly risky and their regulatory treatment is unsettled in many jurisdictions. There may be no regulatory recourse for any loss from transactions in WLD tokens. Any value ascribed to WLD tokens may change quickly and may be lost in its entirety. Further, the technologies comprising World Network, including the WLD token, are experimental in nature. There is no guarantee that the network will operate as planned. For more information, visit www.world.org/risks. Holding, buying, or selling WLD tokens may not be permitted where you live, and it is your responsibility to comply with all applicable laws. Worldcoin (WLD) tokens are not intended to be available to residents of the State of New York or certain other restricted territories. More details can be found at http://www.world.org/tos.
As described further below, this document contains forward-looking estimates and statements regarding the intended actions and objectives of World Foundation and World Network, based largely on current expectations and projections about future events for which the outcome is uncertain. It is therefore subject to a number of known and unknown risks, including those described at www.world.org/risks, that could cause the actual outcomes to differ materially from what is expressed or implied herein. Readers are cautioned not to put undue reliance on these future-looking estimates and statements. The content of this document speaks only as of the date thereof.
Nature of the Whitepaper
The Whitepaper and the Website are intended for general informational purposes and community discussion only and do not constitute a prospectus, an offer document, an offer of securities, a solicitation for investment, or any offer to sell any product, item or asset (whether digital or otherwise). Nothing contained in the Whitepaper or the Website is or may be relied upon as a promise, representation or undertaking as to the future performance of World Network. The information herein may not be exhaustive and does not imply any element of a contractual relationship commitment in relation to the acquisition of WLD Token, and no virtual currency or other form of payment is to be accepted on the basis of the Whitepaper or the Website. There is no assurance as to the accuracy or completeness of such information and no representation, warranty or undertaking is or purported to be provided as to the accuracy or completeness of such information. Nothing contained in the Whitepaper or the Website is or may be relied upon as a promise, representation or undertaking as to the future performance of World Network. Any agreement between any third party and you, in relation to any sale, purchase, or other distribution or transfer of WLD Token, is to be governed only by the separate terms and conditions of such agreement, and such agreement must be read together with the Whitepaper. Where the Whitepaper or the Website includes information that has been obtained from third party sources, the Foundation, their respective affiliates and/or World Network have not independently verified the accuracy or completion of such information. Further, you acknowledge that circumstances may change and that the Whitepaper or the Website may become outdated as a result; and the Foundation is not under any obligation to update or correct this document in connection therewith.
The information set out in the Whitepaper and the Website is for community discussion only and is not legally binding. No person is bound to enter into any contract or binding legal commitment in relation to the acquisition of any WLD token, and no virtual currency or other form of payment is to be accepted on the basis of the Whitepaper or the Website. Any agreement governing the sale or acquisition of WLD tokens shall be governed by a separate set of Terms of Service, available at www.world.org/tos. The Terms of Service must be read together with the Whitepaper and further information available at www.world.org/risks. In the event of any inconsistencies between the Terms of Service and the Whitepaper or the Website, the Terms of Service shall prevail.
Token Features
The native digital cryptographically-secured cryptocurrency of World Network (WLD Token) is a transferable representation of attributed functions specified in the protocol/code of World Network, designed to play a major role in the functioning of the ecosystem on World Network, and intended to be used solely as the primary utility and future governance token on the platform. The goal of introducing WLD Token is to provide a convenient and secure mode of payment and settlement between participants who interact within the ecosystem on World Network, and it is not, and not intended to be, a medium of exchange accepted by the public (or a section of the public) as payment for goods or services or for the discharge of a debt; nor is it designed or intended to be used by any person as payment for any goods or services whatsoever that are not exclusively provided by the issuer. WLD Token may only be utilized on World Network, and ownership of WLD Token carries no rights, express or implied, other than the right to use WLD Token as a means to enable usage of and interaction within World Network. WLD Token is not intended to be an investment, and no value appreciation is guaranteed or implied.
Deemed Representations and Warranties
By accessing the Whitepaper or the Website (or any part thereof), you shall be deemed to represent and warrant to the Foundation, their respective affiliates, and World Network as follows:
-
in any decision to receive and/or purchase any WLD Token, you shall not rely on any statement set out in the Whitepaper or the Website;
-
you will and shall at your own expense ensure compliance with all laws, regulatory requirements and restrictions applicable to you (as the case may be);
-
you acknowledge, understand and agree that WLD Token may have no value, there is no guarantee or representation of value or liquidity for WLD Token, and WLD Token is not an investment product including for any speculative investment;
-
WLD tokens may not always be transferable or liquid;
-
WLD tokens may not be exchangeable against any goods or services contemplated in the Whitepaper, especially in case of failure or discontinuation of the project;
-
none of the Foundation, their respective affiliates, and/or World Network members shall be responsible for or liable for the value of WLD Token, the transferability and/or liquidity of WLD Token and/or the availability of any market for WLD Token through third parties or otherwise; and
-
you acknowledge, understand and agree that you are not eligible to purchase any WLD Token if you are a citizen, national, resident (tax or otherwise), domiciliary and/or green card holder of a geographic area or country (i) where it is likely that the sale of WLD Token would be construed as the sale of a security, financial service or investment product and/or (ii) where participation in token sales is prohibited by applicable law, decree, regulation, treaty, or administrative act; and to this effect you agree to provide all such identity verification document when requested in order for the relevant checks to be carried out.
The Foundation disclaims all representations, warranties or undertakings to any entity or person (including without limitation warranties as to the accuracy, completeness, timeliness or reliability of the contents of the Whitepaper or the Website, or any other materials published by the Foundation). To the maximum extent permitted by law, the Foundation, their respective affiliates and service providers, and the World Network shall not be liable for any indirect, special, incidental, consequential or other losses of any kind, in tort, contract or otherwise (including, without limitation, any liability arising from default or negligence on the part of any of them, or any loss of revenue, income or profits, and loss of use or data) arising from the use of the Whitepaper or the Website, or any other materials published, or its contents (including without limitation any errors or omissions) or otherwise arising in connection with the same. Prospective purchasers of the WLD Token should carefully consider and evaluate all risks and uncertainties (including financial and legal risks and uncertainties) associated with the WLD Token sale, the Foundation, and World Network.
Disclaimers Relating to the WLD Token
It is expressly highlighted that WLD Token:
-
does not have any tangible or physical manifestation, and does not have any intrinsic value (nor does any person make any representation or give any commitment as to its value), and may lose its value in part or in full;
-
is non-refundable and cannot be exchanged for cash (or its equivalent value in any other virtual currency) or any payment obligation by the Foundation, the World Network, or any of their respective affiliates, and may not always be transferrable or liquid;
-
does not represent or confer on the token holder any right of any form with respect to the Foundation, the World Network (or any of their respective affiliates), or its revenues or assets, including without limitation any right to receive future dividends, revenue, shares, ownership right or stake, share or security, any voting, distribution, redemption, liquidation, proprietary (including all forms of intellectual property or license rights), right to receive accounts, financial statements or other financial data, the right to requisition or participate in shareholder meetings, the right to nominate a director, or other financial or legal rights or equivalent rights, or intellectual property rights or any other form of participation in or relating to World Network, the Foundation, and/or their service providers;
-
does not entitle token holders to any promise of fees, dividends, revenue, profits or investment returns, and are not intended to constitute securities in any relevant jurisdiction;
-
is not intended to represent any rights under a contract for differences or under any other contract the purpose or pretended purpose of which is to secure a profit or avoid a loss;
-
may not be exchangeable against the good or service described herein, especially in case of failure or discontinuation of World;
-
is not intended to be a representation of money (including electronic money), security, commodity, bond, debt instrument, unit in a collective investment scheme or any other kind of financial instrument or investment;
-
is not a loan to the Foundation, the World Network, or any of their respective affiliates, is not intended to represent a debt owed by the Foundation, the World Network, or any of their respective affiliates, and there is no expectation of profit; and
-
does not provide the token holder with any ownership or other interest in the Foundation, the World Network, or any of their respective affiliates.
Informational Purposes Only
The project roadmap in the Whitepaper is being shared in order to outline the current status of World as well as some of the plans of World Network and is provided solely for informational purposes and does not constitute any binding commitment. Please do not rely on this information in making purchasing decisions because ultimately, further development, release, and timing of any products, features or functionality remains at the sole discretion of the Foundation, the World Network, or their respective affiliates, and is subject to change. Further, the Whitepaper or the Website may be amended or replaced from time to time. There are no obligations to update the Whitepaper or the Website, or to provide recipients with access to any information beyond what is provided herein.
Regulatory Approval
The legal and regulatory treatment of digital assets in the United States and globally continues to evolve. The Foundation actively monitors applicable laws and may adjust its operations and distribution mechanisms to maintain compliance with future regulatory developments.
No regulatory authority has examined or approved, whether formally or informally, of any of the information set out in the Whitepaper or the Website. No such action or assurance has been or will be taken under the laws, regulatory requirements or rules of any jurisdiction. The publication, distribution or dissemination of the Whitepaper or the Website does not imply that the applicable laws, regulatory requirements or rules have been complied with. World Foundation is solely responsible for the content of this Whitepaper. This Whitepaper has not been reviewed or approved by any competent authority in any Member State of the European Union.
Cautionary Note on Forward-Looking Statements
All statements contained herein, statements made in press releases or in any place accessible by the public and oral statements that may be made by the Foundation and/or the World Network may constitute forward-looking statements (including statements regarding intent, belief or current expectations with respect to market conditions, business strategy and plans, financial condition, specific provisions and risk management practices). You are cautioned not to place undue reliance on these forward-looking statements given that these statements involve known and unknown risks, uncertainties and other factors that may cause the actual future results to be materially different from that described by such forward-looking statements, and no independent third party has reviewed the reasonableness of any such statements or assumptions. These forward-looking statements are applicable only as of the date indicated in the Whitepaper, and the Foundation, as well as World Network expressly disclaim any responsibility (whether express or implied) to release any revisions to these forward-looking statements to reflect events after such date.
English Language
The Whitepaper and the Website may be translated into a language other than English for reference purpose only and in the event of conflict or ambiguity between the English language version and translated versions of the Whitepaper or the Website, the English language versions shall prevail. You acknowledge that you have read and understood the English language version of the Whitepaper and the Website.
Limitations
This section outlines some limitations (without claiming exhaustiveness) based on laws, intrinsic limitations of the project as well as temporary limitations that can be mitigated by further open development.
UBI
World enables the fair distribution of UBI globally as it offers both globally-accessible digital financial rails while ensuring each participant cannot double-claim the same UBI distribution. World Network is not intended to generate profits to distribute UBI, and instead, it requires a separate funding source (e.g., a share of the profits generated by an AI Lab) to distribute global UBI.
Orb Security
The Orb sets a high bar to defend against scalable attacks; however, no hardware system interacting with the physical world can achieve perfect security. The security and anti-fraud measures integrated into the Orb are continuously refined. Several contributor teams are continuously working on increasing the efficacy of the liveness algorithms as well as other security measures that are deployed via over-the-air updates. Even though significant effort has been spent on raising the security bar of the Orb, it is expected that an Orb may get spoofed or compromised by determined actors. The Orb has been designed with this threat model in mind: any World ID issued by a particular Orb can later on be revoked through the governance of World Network. To continuously discover potential vulnerabilities of the Orb, contributor red teams test various attack vectors. Several audits on the Orb and its infrastructure have been conducted and a bug bounty program will soon launch. Implementing suitable incentive mechanisms for Operators and decentralized audits of all Orbs in operation can help raise the bar beyond what hardware security could achieve in isolation, especially for scalable attacks.
False Rejections
Biometrics are probabilistic and biometric verification has inherent error rates. Currently, the error rate of the Orb for confusing any two people to be the same, is approximately 1 in 40 trillion. On a billion people scale, this translates to a 99.999% true acceptance rate or 0.001% false rejection rate, which is significantly better than other known alternatives. However, the ultimate objective is enabling total inclusivity. Using the birthday problem approximation, a false rejection rate of is statistically required to prevent the false exclusion of a single individual at a global scale. Ongoing community research is focussed on improving iris biometrics beyond the current state-of-the-art by leveraging AI and advanced hardware capabilities of the Orb. In the event that iris biometrics turn out to be insufficient, combining several biometric signals (biometric fusion1) could be employed to further reduce the error rate, a functionality already supported by the current hardware version of the Orb.
It is important to note that many health conditions, like cataracts to a certain degree, do not impede iris biometrics. Already today, iris biometrics surpass the inclusivity of other proof of human verification alternatives like official IDs since less than 50% of the global population has digitally verifiable identities. However, if the proof of human mechanism becomes essential for society, it is important that eventually every single person can verify if they want to. Although not currently established, there could be specialized verification centers to facilitate alternative means of verification for individuals with eye conditions, via e.g. facial biometrics. The introduction of alternative means of verification for World ID could potentially create loopholes. More details on the biometric verification through the Orb can be found here.
Decentralization and Open Sourcing
Today, large parts of World Network stack are open source. This includes the World ID protocol, the sequencer for the Orb credential, and the SDK to access it. Other parts, like the firmware of the Orb are not yet open source due to security considerations; however, eventually every part of the infrastructure supporting the Orb credential should be open source. Further, while operations are already spread across independent entities, Orbs are only available via Tools for Humanity. For more details, see the decentralization section.
World ID Transferability
While deduplication, i.e. ensuring that everyone can only verify once, has been solved to a high degree of certainty with the Orb, the authentication of the legitimate owner of a proof of human credential is both an important as well as a difficult challenge. This challenge is the same for any digital identity or proof of human mechanism. Today, if someone passes on their World ID keys to a fraudster (e.g., through being tricked to sell their keys), the fraudster can then use that World ID to authenticate. Therefore, fraudsters could bypass the “one-person one-X” principle by acquiring multiple World IDs. There are several preventative measures in the World App that make it harder to restore another user’s backup, however, those measures are only temporary, especially since access to World ID through other wallets will become increasingly important over time. Therefore, several additional measures should be implemented:
- Face Authentication: Facial recognition, performed locally on the user’s device in a fashion similar to Face ID, can be used to authenticate users against their Orb verification, thereby ensuring that only the person to whom the World ID was originally issued can use it to prove that they are human. Authentication involves a 1:1 comparison with a pre-existing template that is stored on the user's phone, which requires considerably lower levels of accuracy in contrast to the 1:N global verification of uniqueness that the Orb is performing. Therefore, the entropy inherent to facial features is sufficient.
- Iris Authentication: This is conceptually similar to face authentication with the difference that an individual needs to return to an Orb. This process validates the individual as the rightful owner of their proof of human credential. Using iris authentication through the Orb instead of face authentication on the users phone increases security. This authentication mechanism can be compared with, for example, physically showing up to a bank or notary to authenticate certain transactions. Although inconvenient, and therefore rarely required, it provides increased security guarantees.
- World ID Recovery and Re-Issuance of Keys: If a proof of human credential has been lost or compromised by a fraudulent actor, individuals can get their Orb credential re-issued by returning to the Orb, without the need to remember a password or similar information.
More details on the different mechanisms and their roadmap can be found here.
Key Recovery and Persistent Reputation
Today, keys can be recovered through restoring user-managed backups. If someone lost their keys, they can get a new World ID (and deactivate their previous one); however, the keys for the previous World ID cannot be recovered through biometrics. For privacy reasons, actions associated with a particular World ID cannot be recovered today. Consequently, humanness validation should be implemented today with time bounds to ensure sybil resistance. It also means that certain use cases like persistent reputation, as would be required for undercollateralized lending, are limited today. Enabling World ID recovery requires solving hard research challenges to preserve privacy as well as a careful consideration of societal implications of persistent reputation. More details on recovery and the roadmap can be found here.
Footnotes
-
This requires the prevention of combinatorial attacks and therefore excludes e.g. fingerprints. Therefore, the only possible combination would be combining pictures of the iris and the face since they are imaged at the same point in time and in the same location (i.e. the face). ↩